Cybercriminals are ever more leveraging malicious LNK files as an preliminary entry method to obtain and execute payloads these kinds of as Bumblebee, IcedID, and Qakbot.
A latest study by cybersecurity experts has revealed that it is possible to identify relationships among various menace actors by analyzing the metadata of destructive LNK documents, uncovering information such as the distinct tools and techniques applied by various teams of cybercriminals, as perfectly as prospective backlinks among seemingly unrelated attacks.
“With the increasing utilization of LNK files in attack chains, it can be rational that danger actors have started out producing and working with instruments to build this kind of data files,” Cisco Talos researcher Guilherme Venere said in a report shared with The Hacker News.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This consists of tools like NativeOne’s mLNK Builder and Quantum Builder, which enable subscribers to crank out rogue shortcut information and evade security options.
Some of the key malware households that have made use of LNK information for initial obtain incorporate Bumblebee, IcedID, and Qakbot, with Talos pinpointing connections among Bumblebee and IcedID as nicely as Bumblebee and Qakbot by examining the artifacts’ metadata.
Precisely, multiple samples of LNK data files leading to IcedID and Qakbot infections and those people that have been applied in diverse Bumblebee strategies have all been located to share the same Drive Serial Selection.
LNK files have also been used by sophisticated persistent danger (APT) teams like Gamaredon (aka Armageddon) in its attacks aimed at Ukrainian govt entities.
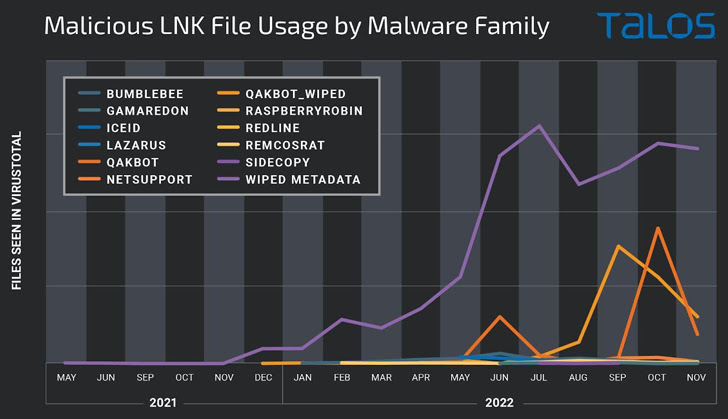
The apparent spike in campaigns employing destructive shortcuts is viewed as a reactive reaction to Microsoft’s choice to disable macros by default in Office documents downloaded from the Internet, prompting danger actors to embrace substitute attachment forms and delivery mechanisms to distribute malware.
New analyses from Talos and Trustwave have disclosed how APT actors and commodity malware people alike are weaponizing Excel include-in (XLL) files and Publisher macros to drop remote obtain trojans on compromised equipment.
What’s a lot more, menace actors have been observed using benefit of rogue Google Adverts and lookup motor optimization (Web optimization) poisoning to drive off-the-shelf malware like BATLOADER, IcedID, Rhadamanthys Stealer, and Vidar to victims hunting for a slew of legit program.
BATLOADER, linked with an intrusion set tracked by Pattern Micro as Drinking water Minyades, is an “evasive and evolutionary malware” that is able of installing more malware, which includes Cobalt Strike, Qakbot, Raccoon Stealer, RedLine Stealer, SmokeLoader, Vidar, and ZLoader.
“Attackers are imitating the web sites of preferred program initiatives to trick victims into infecting their pcs and obtaining research motor adverts to drive targeted visitors there,” HP Wolf Security researcher Patrick Schläpfer said.
Uncovered this article intriguing? Stick to us on Twitter and LinkedIn to study more distinctive content material we publish.
Some areas of this report are sourced from:
thehackernews.com

 6 Types of Risk Assessment Methodologies + How to Choose
6 Types of Risk Assessment Methodologies + How to Choose