A new Android backdoor has been found out with potent abilities to have out a vary of destructive steps on infected units.
Dubbed Xamalicious by the McAfee Mobile Research Group, the malware is so named for the point that it’s created employing an open-supply mobile application framework referred to as Xamarin and abuses the running system’s accessibility permissions to fulfill its objectives.
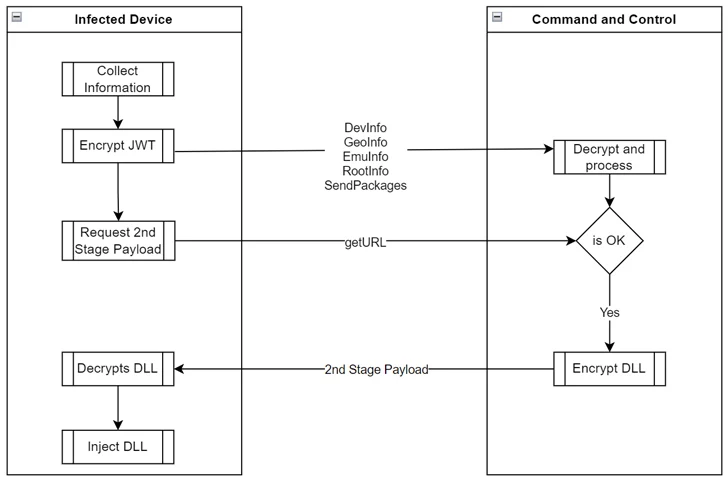
It truly is also capable of accumulating metadata about the compromised product and getting in touch with a command-and-control (C2) server to fetch a next-stage payload, but only just after identifying if it suits the invoice.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The next phase is “dynamically injected as an assembly DLL at runtime amount to choose entire management of the product and perhaps accomplish fraudulent steps these types of as clicking on ads, setting up apps, between other actions economically inspired without user consent,” security researcher Fernando Ruiz explained.
The cybersecurity agency claimed it recognized 25 apps that occur with this energetic danger, some of which had been dispersed on the formal Google Enjoy Retail outlet due to the fact mid-2020. The applications are approximated to have been put in at minimum 327,000 times.
Impending WEBINAR From Consumer to ADMIN: Find out How Hackers Get Entire Control
Find the mystery ways hackers use to become admins, how to detect and block it before it really is also late. Sign-up for our webinar nowadays.
Sign up for Now
A the greater part of the infections have been reported in Brazil, Argentina, the U.K., Australia, the U.S., Mexico, and other elements of Europe and the Americas. Some of the applications are mentioned down below –
- Necessary Horoscope for Android (com.anomenforyou.essentialhoroscope)
- 3D Skin Editor for PE Minecraft (com.littleray.skineditorforpeminecraft)
- Symbol Maker Pro (com.vyblystudio.dotslinkpuzzles)
- Vehicle Click on Repeater (com.autoclickrepeater.cost-free)
- Count Simple Calorie Calculator (com.lakhinstudio.counteasycaloriecalculator)
- Audio Quantity Extender (com.muranogames.easyworkoutsathome)
- LetterLink (com.regaliusgames.llinkgame)
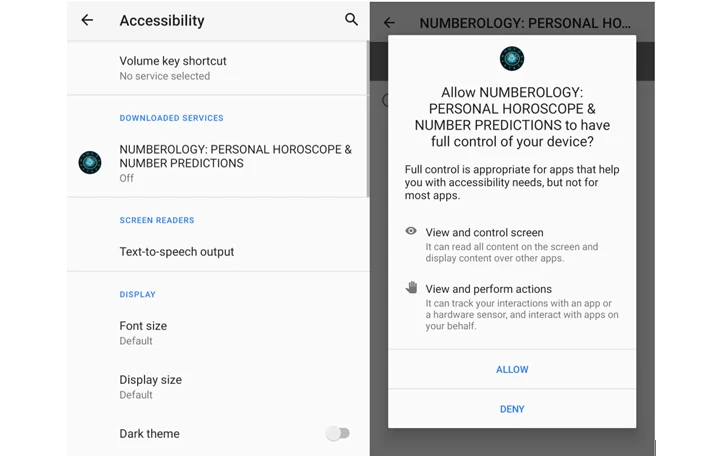
- NUMEROLOGY: Individual HOROSCOPE &Variety PREDICTIONS (com.Ushak.NPHOROSCOPENUMBER)
- Stage Keeper: Uncomplicated Pedometer (com.browgames.stepkeepereasymeter)
- Keep track of Your Sleep (com.shvetsStudio.trackYourSleep)
- Seem Volume Booster (com.devapps.soundvolumebooster)
- Astrological Navigator: Day by day Horoscope & Tarot (com.Osinko.HoroscopeTaro)
- Common Calculator (com.Potap64.universalcalculator)
Xamalicious, which ordinarily masquerades as wellness, online games, horoscope, and productivity apps, is the most up-to-date in a lengthy list of malware family members that abuse Android’s accessibility services, requesting users’ entry to it on installation to have out its duties.
“To evade analysis and detection, malware authors encrypted all interaction and information transmitted between the C2 and the contaminated device, not only protected by HTTPS, it truly is encrypted as a JSON Web Encryption (JWE) token applying RSA-OAEP with a 128CBC-HS256 algorithm,” Ruiz noted.
Even a lot more troublingly, the first-stage dropper consists of capabilities to self-update the key Android offer (APK) file, this means it can be weaponized to act as spy ware or banking trojan devoid of any person interaction.
McAfee stated it determined a url in between Xamalicious and an advertisement-fraud application named Dollars Magnet, which facilitates app obtain and automatic clicker exercise to illicitly get paid profits by clicking on ads.

“Android applications penned in non-java code with frameworks these kinds of as Flutter, respond indigenous and Xamarin can offer an extra layer of obfuscation to malware authors that deliberately decide these equipment to stay clear of detection and attempt to keep under the radar of security suppliers and preserve their presence on applications marketplaces,” Ruiz said.
Android Phishing Campaign Targets India With Banker Malware
The disclosure will come as the cybersecurity corporation comprehensive a phishing marketing campaign that employs social messaging applications like WhatsApp to distribute rogue APK data files that impersonate legitimate banking companies such as the Point out Financial institution of India (SBI) and prompt the user to put in them to entire a necessary Know Your Customer (KYC) method.
Once put in, the app asks the user to grant it SMS-related permissions and redirects to a bogus web site that only captures the victim’s credentials but also their account, credit/debit card, and national identification info.
The harvested knowledge, along with the intercepted SMS messages, are forwarded to an actor-managed server, thereby allowing for the adversary to comprehensive unauthorized transactions.
It truly is really worth noting that Microsoft previous month warned of a identical campaign that utilizes WhatsApp and Telegram as distribution vectors to focus on Indian online banking customers.
“India underscores the acute risk posed by this banking malware within the country’s electronic landscape, with a couple of hits uncovered elsewhere in the globe, maybe from Indian SBI consumers residing in other countries,” researchers Neil Tyagi and Ruiz said.
Identified this posting exciting? Adhere to us on Twitter and LinkedIn to go through extra special content material we article.
Some areas of this write-up are sourced from:
thehackernews.com


 Warning: Poorly Secured Linux SSH Servers Under Attack for Cryptocurrency Mining
Warning: Poorly Secured Linux SSH Servers Under Attack for Cryptocurrency Mining