A new malware strain has been identified covertly concentrating on tiny business/household office (SOHO) routers for far more than two decades, infiltrating more than 70,000 devices and creating a botnet with 40,000 nodes spanning 20 international locations.
Lumen Black Lotus Labs has dubbed the malware AVrecon, making it the 3rd these types of pressure to concentration on SOHO routers just after ZuoRAT and HiatusRAT about the earlier calendar year.
“This can make AVrecon 1 of the most significant SOHO router-concentrating on botnets ever found,” the corporation mentioned. “The reason of the marketing campaign appears to be the development of a covert network to quietly allow a assortment of prison routines from password spraying to digital promoting fraud.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
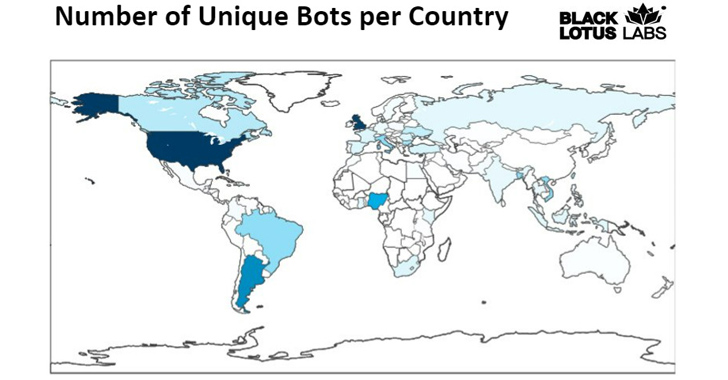
A vast majority of the infections are located in the U.K. and the U.S., adopted by Argentina, Nigeria, Brazil, Italy, Bangladesh, Vietnam, India, Russia, and South Africa, between many others.
AVrecon was initially highlighted by Kaspersky senior security researcher Ye (Seth) Jin in Might 2021, indicating that the malware has managed to prevent detection until finally now.
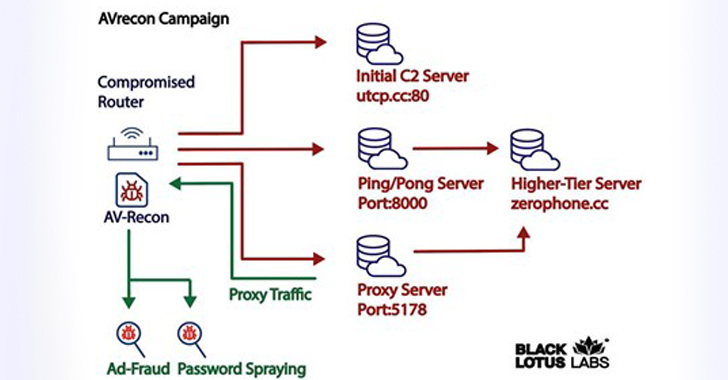
In the attack chain comprehensive by Lumen, a successful an infection is followed by enumerating the victim’s SOHO router and exfiltrating that facts back again to an embedded command-and-control (C2) server.
It also checks if other situations of malware are by now working on the host by hunting for existing processes on port 48102 and opening a listener on that port. A procedure certain to that port is terminated.
The upcoming stage entails the compromised procedure creating call with a independent server, identified as the secondary C2 server, to await additional commands. Lumen explained it determined 15 these types of exclusive servers that have been energetic due to the fact at the very least October 2021.
It is really worth noting that tiered C2 infrastructure is common among infamous botnets like Emotet and QakBot.
Upcoming WEBINARShield Towards Insider Threats: Learn SaaS Security Posture Management
Fearful about insider threats? We’ve got you included! Be part of this webinar to check out sensible methods and the techniques of proactive security with SaaS Security Posture Administration.
Sign up for Currently
AVrecon is created in the C programming language, earning it easy to port the malware for distinctive architectures. What is actually more, a essential reason why these attacks work is for the reason that they leverage infrastructure living on the edge that commonly lacks assistance for security answers.
Proof gathered so far points to the botnet staying utilized for clicking on numerous Facebook and Google advertisements, and to interact with Microsoft Outlook. This probably implies a two-pronged effort to carry out promotion fraud and details exfiltration.
“The way of attack appears to be to aim predominantly on thieving bandwidth – devoid of impacting conclusion-people – in order to build a residential proxy assistance to enable launder destructive activity and steer clear of attracting the exact amount of consideration from Tor-concealed solutions or commercially out there VPN products and services,” the scientists claimed.
Observed this article intriguing? Adhere to us on Twitter and LinkedIn to study extra exclusive content we put up.
Some elements of this write-up are sourced from:
thehackernews.com

 Zimbra Warns of Critical Zero-Day Flaw in Email Software Amid Active Exploitation
Zimbra Warns of Critical Zero-Day Flaw in Email Software Amid Active Exploitation