A malicious actor has been linked to a cloud credential thieving marketing campaign in June 2023 that is centered on Azure and Google Cloud Platform (GCP) products and services, marking the adversary’s enlargement in focusing on beyond Amazon Web Solutions (AWS).
The conclusions appear from SentinelOne and Permiso, which explained the “strategies share similarity with resources attributed to the infamous TeamTNT cryptojacking crew,” even though it emphasized that “attribution stays tough with script-based tools.”
They also overlap with an ongoing TeamTNT marketing campaign disclosed by Aqua identified as Silentbob that leverages misconfigured cloud providers to drop malware as portion of what is claimed to be a screening hard work, whilst also linking SCARLETEEL attacks to the threat actor, citing infrastructure commonalities.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“TeamTNT is scanning for credentials throughout a number of cloud environments, which include AWS, Azure, and GCP,” Aqua noted.
The attacks, which solitary out general public-dealing with Docker occasions to deploy a worm-like propagation module, are a continuation of an intrusion established that beforehand qualified Jupyter Notebooks in December 2022.
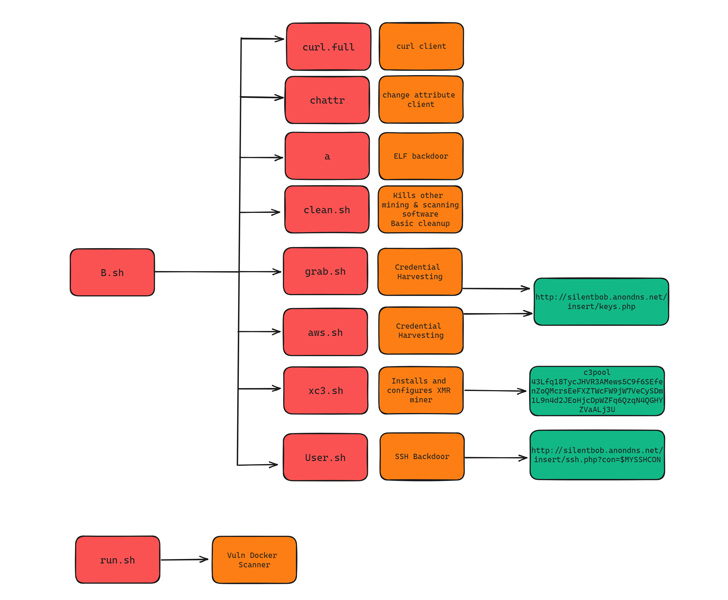
As several as 8 incremental versions of the credential harvesting script have been discovered in between June 15, 2023, and July 11, 2023, indicating an actively evolving marketing campaign.
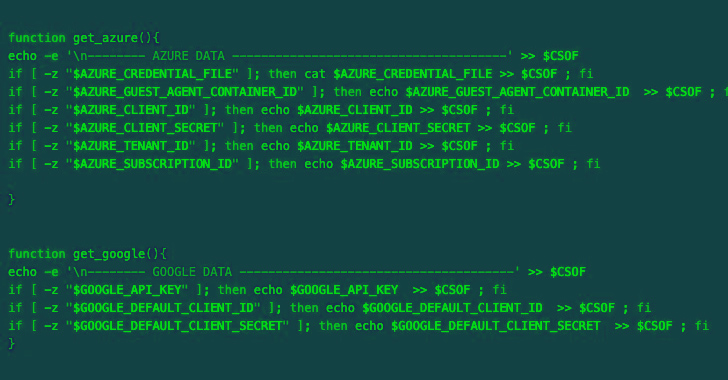
The more recent versions of the malware are made to assemble qualifications from AWS, Azure, Google Cloud System, Censys, Docker, Filezilla, Git, Grafana, Kubernetes, Linux, Ngrok, PostgreSQL, Redis, S3QL, and SMB. The harvested credentials are then exfiltrated to a distant server less than the menace actor’s management.
Future WEBINARShield In opposition to Insider Threats: Master SaaS Security Posture Management
Nervous about insider threats? We have bought you included! Sign up for this webinar to investigate practical methods and the insider secrets of proactive security with SaaS Security Posture Administration.
Be a part of Right now
SentinelOne reported the qualifications assortment logic and the files specific bears similarities to a Kubelet-focusing on campaign carried out by TeamTNT in September 2022.
Along with the shell script malware, the threat actor has also been noticed distributing a Golang-centered ELF binary that functions as a scanner to propagate the malware to vulnerable targets. The binary further more drops a Golang network scanning utility called Zgrab.
“This campaign demonstrates the evolution of a seasoned cloud actor with familiarity across lots of technologies,” security scientists Alex Delamotte, Ian Ahl, and Daniel Bohannon claimed. “The meticulous awareness to depth implies the actor has clearly expert lots of demo and mistake.”
“This actor is actively tuning and improving their equipment. Dependent on the tweaks observed across the past various months, the actor is probably getting ready for larger sized scale strategies.”
Located this write-up exciting? Abide by us on Twitter and LinkedIn to study much more special content material we write-up.
Some areas of this posting are sourced from:
thehackernews.com

 New SOHO Router Botnet AVrecon Spreads to 70,000 Devices Across 20 Countries
New SOHO Router Botnet AVrecon Spreads to 70,000 Devices Across 20 Countries