With speculative execution attacks remaining a stubbornly persistent vulnerability ailing modern day processors, new research has highlighted an “sector failure” to adopting mitigations launched by AMD and Intel, posing a firmware source chain threat.
Dubbed FirmwareBleed by Binarly, the details leaking assaults stem from the ongoing publicity of microarchitectural attack surfaces on the element of business sellers possibly as a result of not accurately incorporating the fixes or only employing them partially.
“The influence of these attacks is targeted on disclosing the material from privileged memory (which includes shielded by virtualization technologies) to attain delicate facts from processes managing on the exact same processor (CPU),” the firmware protection firm claimed in a report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Cloud environments can have a higher impression when a actual physical server can be shared by many users or lawful entities.”
In latest many years, implementations of speculative execution, an optimization technique that predicts the result and focus on of department directions in a program’s execution pipeline, have been considered susceptible to Spectre-like attacks on processor architectures, probably enabling a menace actor to leak cryptographic keys and other techniques.

This works by tricking the CPU into executing an instruction that accesses delicate info in memory that would usually be off-limitations to an unprivileged software and then extracting the information right after the procedure is undone adhering to a misprediction.
A key countermeasure to protect against the damaging effects of speculative execution is a program protection identified as retpoline (aka “Return Trampoline”), which was introduced in 2018.
Whilst current results these types of as Retbleed have conclusively demonstrated that retpoline by by itself is inadequate against halting these attacks in certain situations, the most recent investigation displays a deficiency of regularity in even making use of these mitigations in the very first spot.
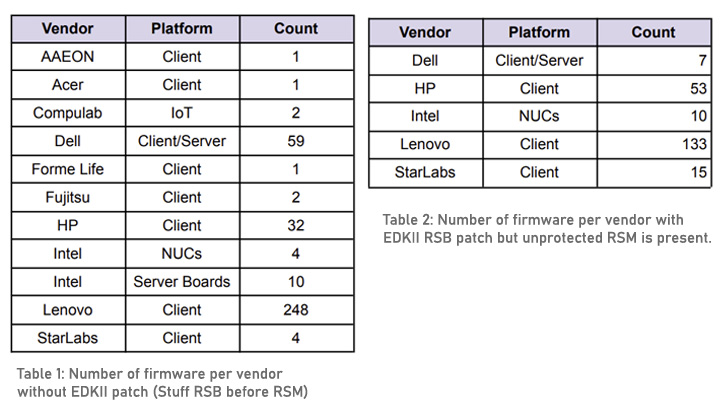
Specifically, it normally takes aim at a best practice known as Return Stack Buffer (RSB) stuffing released by Intel to avoid underflows when applying retpoline. RSBs are handle predictors for return (aka RET) instructions.
“Certain processors may possibly use branch predictors other than the Return Stack Buffer (RSB) when the RSB underflows,” Intel notes in its documentation. “This could effect program working with the retpoline mitigation approach on this kind of processors.”

“On processors with distinctive empty RSB actions, [System Management Mode] code must things the RSB with Connect with guidelines just before returning from SMM to prevent interfering with non-SMM utilization of the retpoline method.”
Intel is also recommending RSB stuffing as a mechanism to thwart buffer underflow attacks like Retbleed, alternatively urging distributors to “set [Indirect Branch Restricted Speculation] ahead of RET guidelines at risk of underflow because of to deep phone stacks.”
The Binarly investigation, nonetheless, has identified as a lot of as 32 firmware from HP, 59 from Dell, and 248 from Lenovo as getting not integrated the RSB stuffing patches, underscoring a “failure in the firmware source chain.”
What’s a lot more, the deep code evaluation has unearthed instances whereby mitigation was existing in the firmware, but contained implementation faults that spawned security issues of its personal, even in updates launched in 2022 and for units showcasing the modern generation of hardware.
“Firmware offer chain ecosystems are really complex and usually have repeatable failures when it arrives to applying new industry-vast mitigations or correcting reference code vulnerabilities,” the researchers said. “Even if a mitigation is current in the firmware, it isn’t going to necessarily mean it is used the right way with out developing security holes.”
Observed this report exciting? Comply with THN on Fb, Twitter and LinkedIn to study extra unique information we write-up.
Some areas of this posting are sourced from:
thehackernews.com


 Pegasus Spyware Used Against Thailand’s Pro-Democracy Movement
Pegasus Spyware Used Against Thailand’s Pro-Democracy Movement