A new monetarily motivated procedure is leveraging a malicious Telegram bot to support menace actors scam their victims.
Dubbed Telekopye, a portmanteau of Telegram and kopye (which means “spear” in Russian), the toolkit functions as an automatic means to build a phishing web website page from a premade template and mail the URL to prospective victims, codenamed Mammoths by the criminals.
“This toolkit is carried out as a Telegram bot that, when activated, presents various simple-to-navigate menus in the sort of clickable buttons that can accommodate several scammers at at the time,” ESET researcher Radek Jizba explained in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The precise origins of the danger actors, dubbed Neanderthals, are unclear, but evidence factors to Russia as the place of origin of the toolkit’s authors and users, owing to the use of Russian SMS templates and the reality that a the vast majority of the targeted on the internet marketplaces are common in the region.
Various variations of Telekopye have been detected to day, the earliest relationship all the way back again to 2015, suggesting that it really is remaining actively preserved and applied for a number of several years.
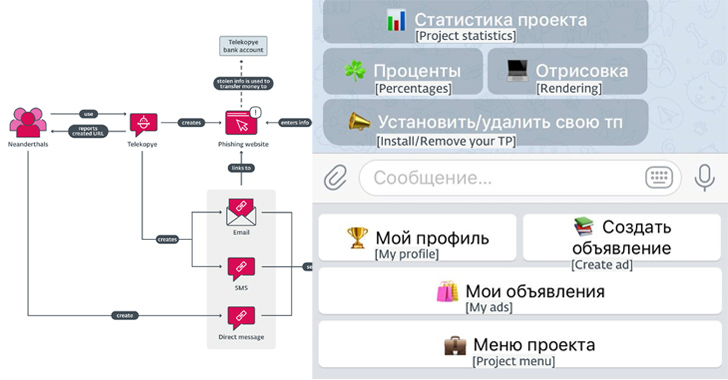
The attack chains progress thus: Neanderthals uncover their Mammoths and test to create rapport with them, ahead of sending a bogus connection made applying the Telekopye phishing kit by way of email, SMS, or a immediate message.

When the payment facts are entered on the phony credit rating/debit card gateway, the facts is used to siphon money from the victim, which are then laundered as a result of cryptocurrency.
Telekopye is totally-showcased, enabling its consumers to send out phishing email messages, produce web pages, send out SMS messages, make QR codes, and develop convincing images and screenshots of checks and receipts.
The phishing domains applied to host the webpages are registered such that closing URL starts with the expected brand name title — cdek.id7423[.]ru, olx.id7423[.]ru, and sbazar.id7423[.]ru — in an energy to make them complicated to spot.
A notable facet of the operation is the centralized character of the payouts. Somewhat than transferring dollars stolen from Mammoths to their personal accounts, it’s funneled to a shared account managed by the Telekopye administrator, offering the main group an oversight into the operations of every Neanderthal.
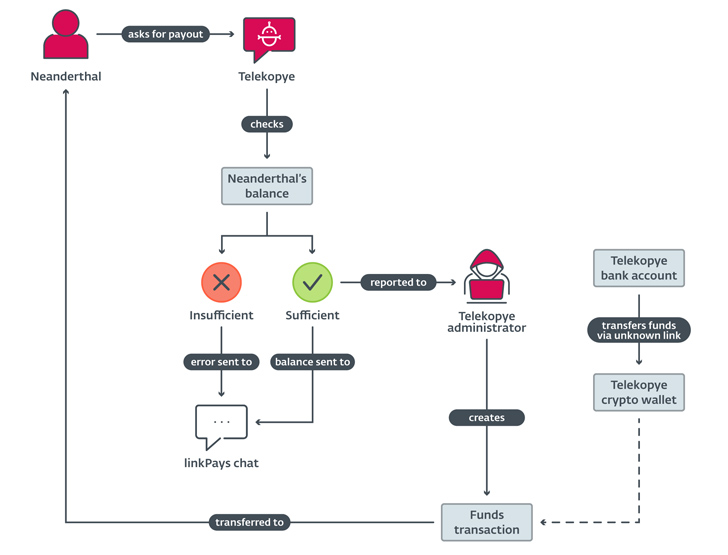
In other terms, Neanderthals get paid by the Telekopye administrator just after requesting for a payout by way of the toolkit by itself, but not just before a chunk of it is taken as commission charges to the system owner and the recommender.
“Telekopye checks the Neanderthal’s balance, ultimate ask for is authorised by the Telekopye administrator and, eventually, funds are transferred to the Neanderthal’s cryptocurrency wallet,” Jizba claimed.
“In some Telekopye implementations, the first phase, asking for a payout, is automatic and the negotiation is initiated anytime a Neanderthal reaches a certain threshold of stolen dollars from properly pulled off scams.”

In what is actually a even more sign of the professionalization of the criminal company, users and operators of Telekopye are structured in a obvious hierarchy spanning roles such as directors, moderators, superior workers (or assistance bots), workers, and blocked.
- Blocked: Users who are prohibited from utilizing Telekopye for probable breaking the undertaking rules.
- Employees: A popular job assigned to all new Neanderthals.
- Excellent personnel: An update of the Worker job with a larger payout and a reduced commission expenses.
- Moderators: People who can encourage and demote other associates and approve new members, but are not able to modify toolkit options.
- Directors: Consumers with the best privileges who can add phishing web web page templates and alter payout rates.
“The least difficult way to convey to no matter whether you are currently being specific by a Neanderthal attempting to steal your dollars is by wanting at the language made use of,” Jizba reported. “Insist on in-particular person funds and items trade any time probable when dealing with secondhand items on on line marketplaces. Prevent sending revenue except you are sure exactly where it will go.”
Uncovered this post appealing? Follow us on Twitter and LinkedIn to browse more exclusive content we article.
Some elements of this posting are sourced from:
thehackernews.com

 The Hidden Dangers of Public Wi-Fi
The Hidden Dangers of Public Wi-Fi