The North Korea-joined threat actor acknowledged as Lazarus Group has been noticed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Additionally to distribute a distant accessibility trojan named this kind of as QuiteRAT.
Targets include things like internet backbone infrastructure and healthcare entities in Europe and the U.S., cybersecurity corporation Cisco Talos mentioned in a two-section examination released these days.
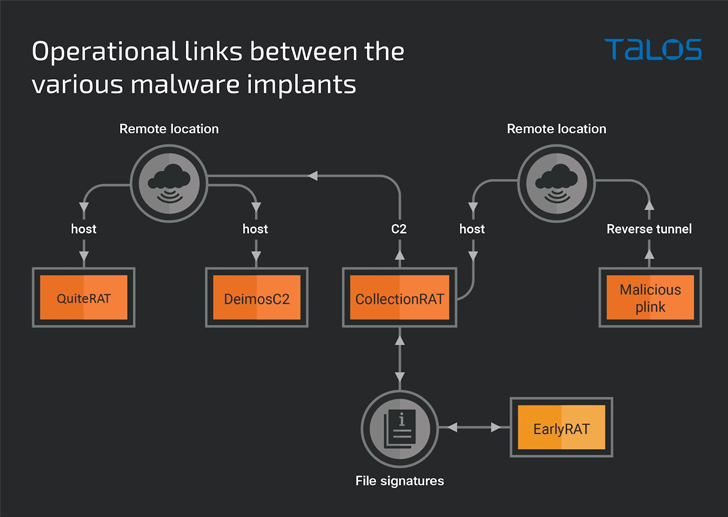
What’s much more, a closer assessment of the adversary’s recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The truth that the Lazarus Team continues to depend on the exact same tradecraft regardless of those people factors getting effectively-documented in excess of the a long time underscores the threat actor’s self-assurance in their functions, Talos pointed out.
QuiteRAT is said to be a successor to MagicRAT, alone a observe-up to TigerRAT, even though CollectionRAT appears to share overlaps with EarlyRAT (aka Jupiter), an implant published in PureBasic with capabilities to operate commands on the endpoint.

“QuiteRAT has numerous of the identical abilities as Lazarus Group’s much better-recognised MagicRAT malware, but its file measurement is drastically scaled-down,” security researchers Asheer Malhotra, Vitor Ventura, and Jungsoo An stated. “Both implants are crafted on the Qt framework and include things like capabilities this kind of as arbitrary command execution.”
The use of the Qt framework is viewed as an intentional hard work on the portion of the adversary to make assessment a ton additional demanding as it “increases the complexity of the malware’s code.”
The activity, detected in early 2023, included the exploitation of CVE-2022-47966, a mere 5 days just after evidence-of-notion (Poc) for the flaw emerged online, to right deploy the QuiteRAT binary from a destructive URL.
“QuiteRAT is clearly an evolution of MagicRAT,” the scientists said. “When MagicRAT is a more substantial, bulkier malware spouse and children averaging all-around 18 MB in sizing, QuiteRAT is a considerably substantially scaled-down implementation, averaging all over 4 to 5 MB in size.”
A different crucial change among the two is the lack of a designed-in persistence system in QuiteRAT, necessitating that a command be issued from the server to ensure ongoing operation on the compromised host.
The conclusions also overlap with another campaign uncovered by WithSecure before this February in which security flaws in unpatched Zimbra devices were being utilized to breach target techniques and ultimately install QuiteRAT.

Cisco Talos said the adversary is “ever more relying on open-supply resources and frameworks in the first access phase of their attacks, as opposed to strictly employing them in the write-up-compromise stage.”
This includes the GoLang-dependent open up-source DeimosC2 framework to attain persistent entry, with CollectionRAT mostly used to obtain metadata, run arbitrary instructions, handle documents on the infected program, and deliver supplemental payloads.
It can be not right away clear how CollectionRAT is propagated, but proof displays that a trojanized copy of the PuTTY Url (Plink) utility hosted on the very same infrastructure is remaining made use of to set up a remote tunnel to the method and serve the malware.
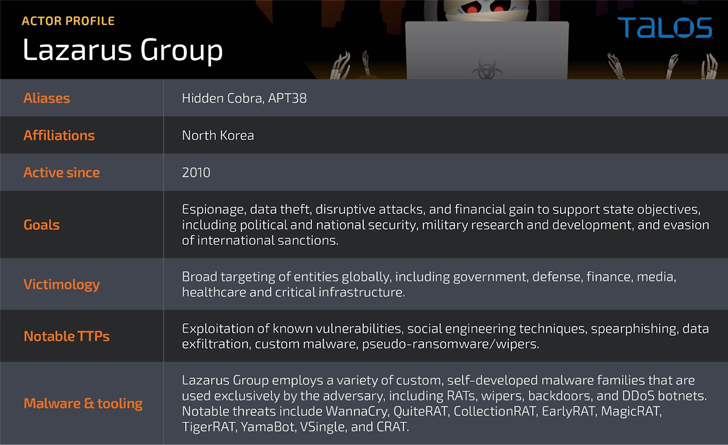
“Lazarus Team formerly relied on the use of personalized-built implants these kinds of as MagicRAT, VSingle, Dtrack, and YamaBot as a usually means of setting up persistent preliminary access on a correctly compromised procedure,” the researchers mentioned.
“These implants are then instrumented to deploy a selection of open up-source or twin-use tools to conduct a multitude of destructive palms-on-keyboard actions in the compromised business network.”
The advancement is a indicator that the Lazarus Group is constantly shifting ways and increasing its malicious arsenal, at the same time weaponizing freshly disclosed vulnerabilities in computer software to devastating outcome.
Found this article intriguing? Abide by us on Twitter and LinkedIn to browse additional exceptional information we write-up.
Some pieces of this article are sourced from:
thehackernews.com


 New Telegram Bot “Telekopye” Powering Large-scale Phishing Scams from Russia
New Telegram Bot “Telekopye” Powering Large-scale Phishing Scams from Russia