A a short while ago patched security flaw in the well-known WinRAR archiving software has been exploited as a zero-working day since April 2023, new findings from Group-IB expose.
The vulnerability, cataloged as CVE-2023-38831, makes it possible for risk actors to spoof file extensions, therefore earning it achievable to launch malicious scripts contained in an archive that masquerades as seemingly innocuous image or text files. It was dealt with in edition 6.23 introduced on August 2, 2023, alongside CVE-2023-40477.
In attacks discovered by the Singapore-based mostly business in July 2023, specifically crafted ZIP or RAR archive documents dispersed by using investing-similar community forums this kind of as Forex trading Station have been used to provide a wide range of malware households these kinds of as DarkMe, GuLoader, and Remcos RAT.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“After infecting gadgets, the cybercriminals withdraw dollars from broker accounts,” Team-IB malware analyst Andrey Polovinkin mentioned, incorporating as quite a few as 130 traders’ equipment have been compromised as section of the marketing campaign. The overall amount of victims and money losses stemming from this exercise are presently not distinct.
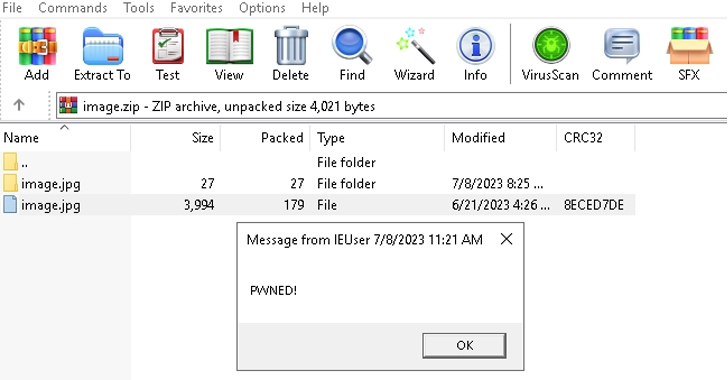
The booby-trapped archive file is created this kind of that it has an impression file as perfectly as a folder with the similar identify.
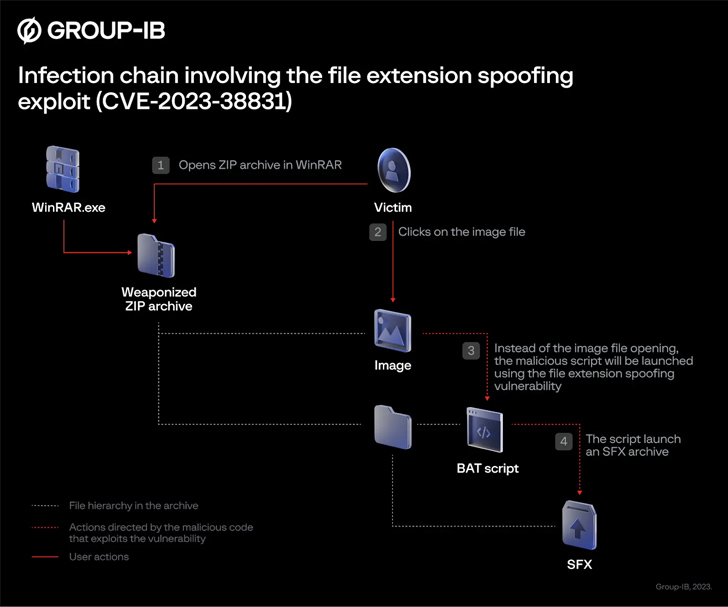
As a end result, when a victim clicks on the image, a batch script existing inside of the folder is executed instead, which is then utilised to start the next-phase, an SFX Taxi archive built to extract and launch added data files. At the similar time, the script also hundreds the decoy image so as not to arouse suspicion.
“CVE-2023-38831 is induced by a processing mistake in opening the file in the ZIP archive,” Polovinkin informed The Hacker News. “Weaponized ZIP archives have been dispersed on at minimum 8 popular trading discussion boards, so the geolocation of victims is wide, and the attacks are not qualified at unique nations around the world or industries.”

It truly is not still identified who is guiding the attacks leveraging the WinRAR flaw. That mentioned, DarkMe is a Visual Primary trojan attributed to the EvilNum team, first documented by NSFOCUS in September 2022 in relationship with a phishing campaign codenamed DarkCasino targeting European on the web gambling and investing companies.
Also sent utilizing this approach is a malware strain referred to as GuLoader (aka CloudEye) that subsequently makes an attempt to fetch Remcos RAT from a distant server.
“Modern situations of exploitation of CVE-2023-38831 remind us of the regular challenges connected to computer software vulnerabilities,” Polovinkin stated. “Threat actors are hugely resourceful, and they will constantly find new approaches to find out and subsequently exploit vulnerabilities.”
Located this short article interesting? Stick to us on Twitter and LinkedIn to go through extra distinctive content we article.
Some pieces of this posting are sourced from:
thehackernews.com

 Thousands of Unpatched Openfire XMPP Servers Still Exposed to High-Severity Flaw
Thousands of Unpatched Openfire XMPP Servers Still Exposed to High-Severity Flaw