A menace with a North Korea nexus has been uncovered leveraging a “novel spear phish methodology” that requires generating use of trojanized variations of the PuTTY SSH and Telnet customer.
Google-owned menace intelligence organization Mandiant attributed the new campaign to an emerging danger cluster it tracks under the identify UNC4034.
“UNC4034 established interaction with the victim around WhatsApp and lured them to obtain a destructive ISO package with regards to a faux career providing that led to the deployment of the AIRDRY.V2 backdoor via a trojanized instance of the PuTTY utility,” Mandiant researchers stated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The use of fabricated job lures as a pathway for malware distribution is an oft-utilised tactic by North Korean point out-sponsored actors, including the Lazarus Team, as section of an enduring marketing campaign termed Procedure Dream Task.
The entry issue of the attack is an ISO file that masquerades as an Amazon Assessment as element of a probable occupation prospect at the tech huge. The file was shared in excess of WhatApp immediately after establishing original get hold of around email.
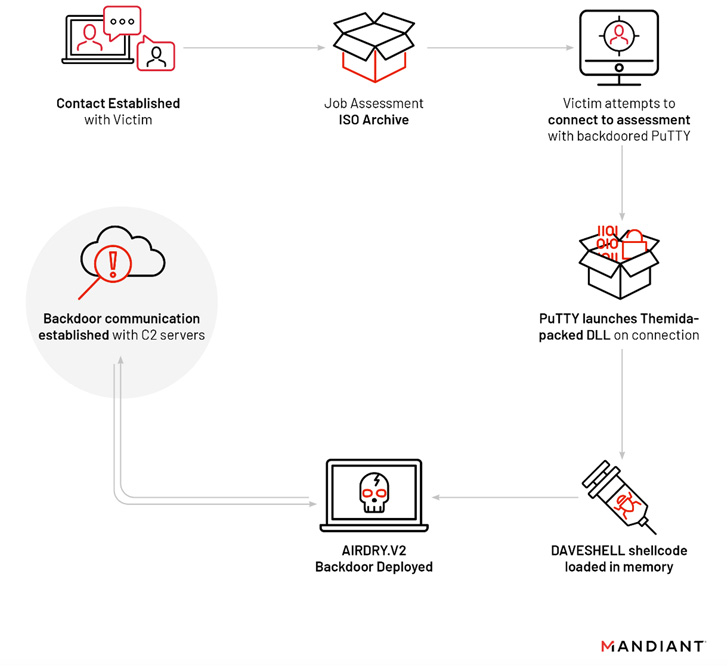
The archive, for its component, holds a textual content file containing an IP address and login credentials, and an altered model of PuTTY that, in transform, masses a dropper referred to as DAVESHELL, which deploys a more recent variant of a backdoor dubbed AIRDRY.
It is probable that the risk actor convinced the target to start a PuTTY session and use the qualifications provided in the TXT file to hook up to the remote host, correctly activating the infection.
AIRDRY, also regarded as BLINDINGCAN, has in the previous been employed by North Korea-joined hackers to strike U.S. defense contractors and entities in South Korea and Latvia.
Although before versions of the malware arrived with approximately 30 commands for file transfer, file administration, and command execution, the most recent model has been located to eschew the command-primarily based strategy in favor of plugins that are downloaded and executed in memory.

Mandiant explained it was equipped to consist of the compromise right before any more publish-exploitation functions could consider put adhering to the deployment of the implant.
The improvement is still yet another signal that the use of ISO files for preliminary access is gaining traction amongst threat actors to produce the two commodity and targeted malware.
The shift is also attributable to Microsoft’s conclusion to block Excel 4. (XLM or XL4) and Visual Standard for Purposes (VBA) macros for Place of work applications downloaded from the internet by default.
Found this post exciting? Comply with THN on Fb, Twitter and LinkedIn to read through a lot more exclusive articles we write-up.
Some areas of this article are sourced from:
thehackernews.com

 How to Use a UTM Solution & Win Time, Money and Resources
How to Use a UTM Solution & Win Time, Money and Resources