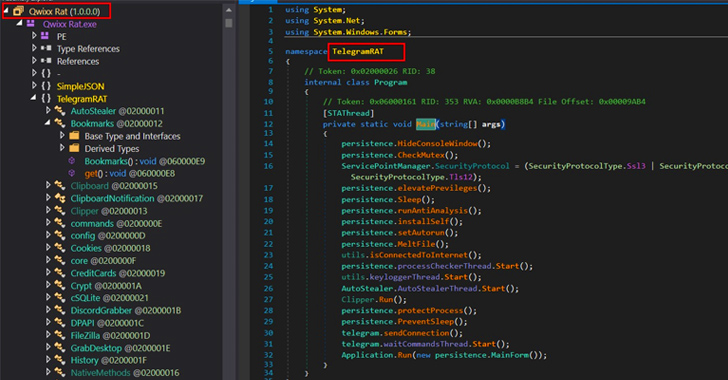
A new remote access trojan (RAT) named QwixxRAT is currently being marketed for sale by its menace actor by way of Telegram and Discord platforms.
“At the time set up on the victim’s Windows platform devices, the RAT stealthily collects delicate details, which is then despatched to the attacker’s Telegram bot, providing them with unauthorized entry to the victim’s delicate information and facts,” Uptycs reported in a new report printed these days.
The cybersecurity corporation, which found out the malware previously this thirty day period, said it really is “meticulously intended” to harvest web browser histories, bookmarks, cookies, credit score card info, keystrokes, screenshots, information matching specified extensions, and knowledge from applications like Steam and Telegram.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The tool is supplied for 150 rubles for weekly entry and 500 rubles for a lifetime license. It also comes in a confined free model.

A C#-centered binary, QwixxRAT arrives with many anti-examination attributes to remain covert and evade detection. This consists of a snooze function to introduce a hold off in the execution process as very well as run checks to ascertain regardless of whether it’s working within a sandbox or virtual atmosphere.
Other capabilities permit it to watch for a unique record of processes (e.g., “taskmgr,” “processhacker,” “netstat,” “netmon,” “tcpview,” and “wireshark”), and if detected, halts its own activity till the course of action is terminated.
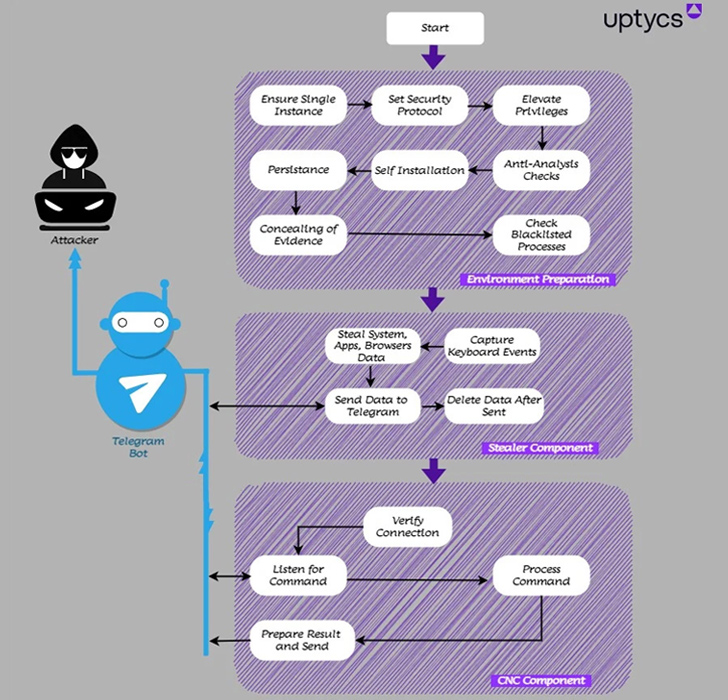
Also integrated in QwixxRAT is a clipper that stealthily accesses delicate facts copied to the device’s clipboard with an aim to carry out illicit fund transfers from cryptocurrency wallets.
Command-and-management (C2) is facilitated by implies of a Telegram bot, by means of which instructions are sent to carry out added knowledge assortment these as audio and webcam recordings and even remotely shutdown or restart the infected host.
The disclosure comes months right after Cyberint disclosed particulars of two other RAT strains dubbed RevolutionRAT and Venom Regulate RAT that’s also marketed on many Telegram channels with knowledge exfiltration and C2 connectivity capabilities.
Located this posting appealing? Follow us on Twitter and LinkedIn to browse a lot more exclusive material we write-up.
Some areas of this article are sourced from:
thehackernews.com

 Ongoing Xurum Attacks on E-commerce Sites Exploiting Critical Magento 2 Vulnerability
Ongoing Xurum Attacks on E-commerce Sites Exploiting Critical Magento 2 Vulnerability