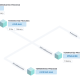
The North Korean risk actor acknowledged as ScarCruft started experimenting with oversized LNK information as a shipping and delivery route for RokRAT malware as early as July 2022, the exact month Microsoft started blocking macros across Business paperwork by default.
“RokRAT has not transformed drastically about the yrs, but its deployment techniques have developed, now using archives that contains LNK documents that initiate multi-stage an infection chains,” Check Position claimed in a new technical report.
“This is a different illustration of a big craze in the menace landscape, exactly where APTs and cybercriminals alike attempt to get over the blocking of macros from untrusted sources.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
ScarCruft, also known by the names APT37, InkySquid, Nickel Foxcroft, Reaper, RedEyes, and Ricochet Chollima, is a risk team that almost exclusively targets South Korean individuals and entities as component of spear-phishing attacks intended to supply an array of custom made tools.

The adversarial collective, in contrast to the Lazarus Team or Kimsuky, is overseen by North Korea’s Ministry of Point out Security (MSS), which is tasked with domestic counterespionage and overseas counterintelligence routines, per Mandiant.
The group’s main malware of choice is RokRAT (aka DOGCALL), which has given that been tailored to other platforms this sort of as macOS (CloudMensis) and Android (RambleOn), indicating that the backdoor is becoming actively produced and managed.
RokRAT and its variants are outfitted to carry out a large selection of things to do like credential theft, info exfiltration, screenshot seize, method data gathering, command and shellcode execution, and file and directory administration.
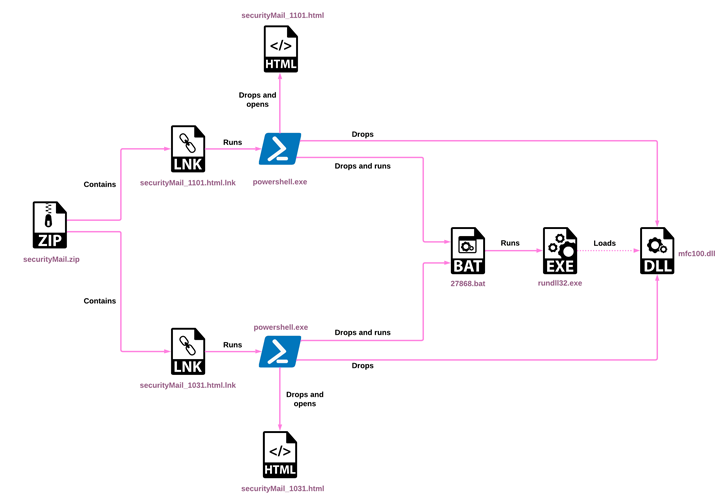
The gathered data, some of which is saved in the type of MP3 documents to protect its tracks, is despatched back employing cloud companies like Dropbox, Microsoft OneDrive, pCloud and Yandex Cloud in a bid to disguise the command-and-management (C2) communications as respectable.
Other bespoke malware utilized by the team include, but not restricted to, Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most a short while ago, M2RAT. It really is also known to use commodity malware these types of as Amadey, a downloader that can obtain commands from the attacker to download additional malware, in a bid to confuse attribution.
The use of LNK files as decoys to activate the an infection sequences was also highlighted by the AhnLab Security Emergency Response Middle (ASEC) final 7 days, with the data files that contains PowerShell commands that deploy the RokRAT malware.
While the improve in modus operandi indicators ScarCruft’s endeavors to continue to keep up with the shifting menace ecosystem, it has ongoing to leverage macro-based malicious Term documents as recently as April 2023 to fall the malware, mirroring a related chain that was reported by Malwarebytes in January 2021.
Upcoming WEBINARLearn to Stop Ransomware with Genuine-Time Defense
Join our webinar and understand how to cease ransomware attacks in their tracks with actual-time MFA and support account defense.
Help you save My Seat!
Yet another attack wave observed at the starting of November 2022, according to the Israeli cybersecurity organization, employed ZIP archives incorporating LNK documents to deploy the Amadey malware.
“[The LNK file] technique can set off an similarly powerful an infection chain by a very simple double click on, 1 that is more reliable than n-day exploits or the Office macros which need added clicks to launch,” Check Point said.
“APT37 carries on to pose a significant risk, launching many strategies across the platforms and considerably bettering its malware delivery strategies.”
The conclusions come as Kaspersky disclosed a new Go-primarily based malware designed by ScarCruft codenamed SidLevel that makes use of the cloud messaging provider Ably as a C2 system for the very first time and will come with “extensive abilities to steal delicate information and facts from victims.”
“The team continues to target individuals similar to North Korea, which include novelists, tutorial pupils, and also small business persons who appear to send funds back to North Korea,” the Russian cybersecurity agency famous in its APT Tendencies Report for Q1 2023.
Found this posting intriguing? Stick to us on Twitter and LinkedIn to browse far more exceptional material we article.
Some elements of this write-up are sourced from:
thehackernews.com

 Alert: Active Exploitation of TP-Link, Apache, and Oracle Vulnerabilities Detected
Alert: Active Exploitation of TP-Link, Apache, and Oracle Vulnerabilities Detected