In yet an additional occasion of how menace actors are abusing Google Ads to provide malware, a menace actor has been observed leveraging the technique to provide a new Windows-primarily based economical trojan and data stealer referred to as LOBSHOT.
“LOBSHOT carries on to obtain victims whilst being beneath the radar,” Elastic Security Labs researcher Daniel Stepanic reported in an analysis revealed previous 7 days.
“One particular of LOBSHOT’s main abilities is all-around its hVNC (Concealed Virtual Network Computing) ingredient. These types of modules permit for immediate and unobserved obtain to the device.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The American-Dutch firm attributed the malware strain to a danger actor acknowledged as TA505 based on infrastructure historically connected to the team. TA505 is a fiscally determined e-crime syndicate that overlaps with action clusters tracked less than the names Evil Corp, FIN11, and Indrik Spider.

The latest progress is significant since it can be a signal that TA505, which is related with the Dridex banking trojan, is once once more growing its malware arsenal to perpetrate details theft and economic fraud.
LOBSHOT, with early samples relationship again to July 2022, is dispersed by usually means of rogue Google ads for reputable instruments like AnyDesk that are hosted on a network of lookalike landing pages managed by the operators.
The malware incorporates dynamic import resolution (i.e., resolving the names of needed Windows APIs at runtime), anti-emulation checks, and string obfuscation to evade detection by security program.
When set up, it makes Windows Registry modifications to set up persistence and siphons info from over 50 cryptocurrency wallet extensions current in web browsers like Google Chrome, Microsoft Edge, and Mozilla Firefox.
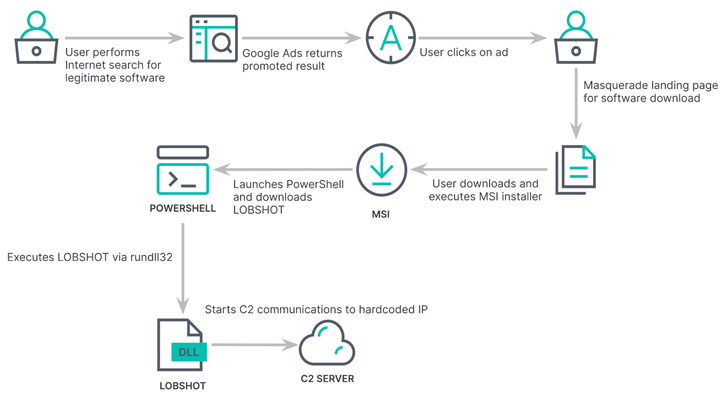
LOBSHOT’s other noteworthy options revolve all around its capability to remotely entry the compromised host through an hVNC module and stealthily carry out steps on it without attracting the victim’s attention.
“Danger groups are continuing to leverage malvertising methods to masquerade authentic application with backdoors like LOBSHOT,” Stepanic reported.
“These types of malware feel smaller, but conclude up packing substantial operation which aids risk actors go immediately all through the original entry levels with fully interactive remote command abilities.”
Approaching WEBINARLearn to Halt Ransomware with Authentic-Time Defense
Sign up for our webinar and discover how to halt ransomware attacks in their tracks with true-time MFA and support account safety.
Save My Seat!
The conclusions also underscore how an growing amount of adversaries are adopting malvertising and search motor optimization (Web optimization) poisoning as a system to redirect users to pretend web-sites and down load trojanized installers of well-known software.
In accordance to info from eSentire, the danger actors at the rear of GootLoader have been joined to a string of attacks concentrating on legislation companies and corporate legal departments in the U.S., Canada, the U.K., and Australia.
GootLoader, lively due to the fact 2018 and which capabilities as an original entry-as-a-company procedure for ransomware attacks, employ Search engine optimisation poisoning to entice victims searching for agreements and contracts to infected WordPress weblogs that level to one-way links that contains the malware.
Moreover implementing geofencing to target victims in select regions, the attack chain is made this sort of that the malware can only be downloaded at the time for every day from the hijacked websites in purchase to elude discovery by incident responders.
GootLoader’s use of the IP deal with approach to display screen currently hacked victims, eSentire discovered, could be employed from it to preemptively block the close users’ IP addresses and prevent corporations from probable infections.
Uncovered this report exciting? Observe us on Twitter and LinkedIn to read through much more special material we publish.
Some parts of this report are sourced from:
thehackernews.com

 North Korea’s ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
North Korea’s ScarCruft Deploys RokRAT Malware via LNK File Infection Chains