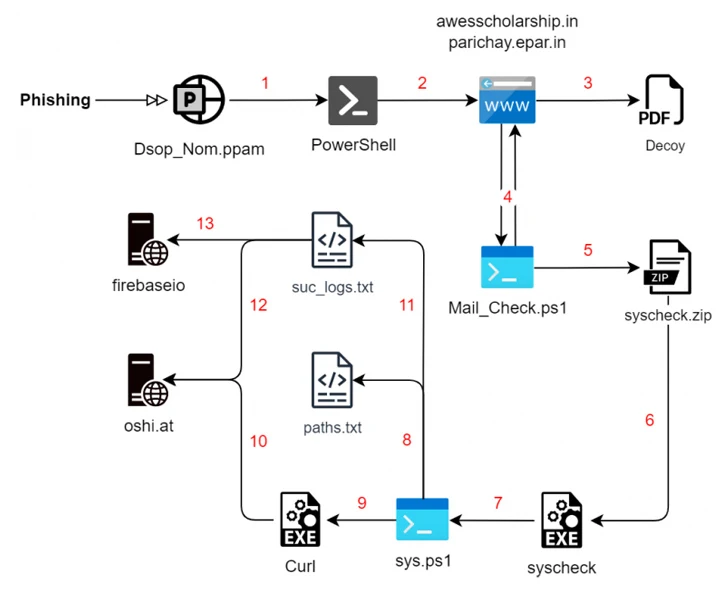
Indian governing administration entities and the protection sector have been specific by a phishing marketing campaign that’s engineered to drop Rust-primarily based malware for intelligence gathering.
The exercise, initially detected in Oct 2023, has been codenamed Procedure RusticWeb by business security business SEQRITE.
“New Rust-based mostly payloads and encrypted PowerShell instructions have been utilized to exfiltrate confidential paperwork to a web-based mostly support engine, in its place of a devoted command-and-manage (C2) server,” security researcher Sathwik Ram Prakki said.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Tactical overlaps have been uncovered concerning the cluster and these extensively tracked beneath the monikers Clear Tribe and SideCopy, both equally of which are assessed to be linked to Pakistan.
SideCopy is also a suspected subordinate aspect within just Transparent Tribe. Very last thirty day period, SEQRITE detailed many strategies carried out by the risk actor focusing on Indian authorities bodies to supply various trojans this kind of as AllaKore RAT, Ares RAT, and DRat.
Approaching WEBINAR Conquer AI-Run Threats with Zero Rely on – Webinar for Security Experts
Common security steps will not cut it in today’s entire world. It’s time for Zero Have confidence in Security. Protected your data like under no circumstances prior to.
Sign up for Now
Other current attack chains documented by ThreatMon have used decoy Microsoft PowerPoint documents as effectively as specifically crafted RAR archives vulnerable to CVE-2023-38831 for malware shipping and delivery, enabling unbridled distant accessibility and handle.
“The SideCopy APT Group’s infection chain entails numerous techniques, each meticulously orchestrated to make certain productive compromise,” ThreatMon famous earlier this yr.
The hottest set of attacks commences with a phishing email, leveraging social engineering techniques to trick victims into interacting with destructive PDF documents that fall Rust-based mostly payloads for enumerating the file technique in the background whilst exhibiting the decoy file to the sufferer.
Apart from amassing files of desire, the malware is equipped to collect technique info and transmit them to the C2 server but lacks the attributes of other advanced stealer malware offered in the cybercrime underground.
A next infection chain discovered by SEQRITE in December employs a identical multi-stage course of action but substitutes the Rust malware with a PowerShell script that requires care of the enumeration and exfiltration measures.
But in an exciting twist, the remaining-phase payload is introduced by means of a Rust executable that goes by the identify “Cisco AnyConnect Web Helper.” The collected details is in the end uploaded to oshi[.]at area, an nameless public file-sharing engine called OshiUpload.
“Operation RusticWeb could be connected to an APT menace as it shares similarities with several Pakistan-connected teams,” Ram Prakki claimed.

The disclosure comes nearly two months immediately after Cyble uncovered a malicious Android application utilized by the DoNot Team concentrating on folks in the Kashmir location of India.
The country-state actor, also known by the names APT-C-35, Origami Elephant, and SECTOR02, is thought to be of Indian origin and has a heritage of employing Android malware to infiltrate products belonging to people in Kashmir and Pakistan.
The variant examined by Cyble is a trojanized model of an open up-resource GitHub venture called “QuranApp: Go through and Discover” that arrives fitted with a extensive assortment of adware options to report audio and VoIP calls, seize screenshots, assemble facts from different apps, obtain supplemental APK documents, and keep track of the victim’s site.
“The DoNot group’s relentless efforts to refine their resources and strategies underscore the ongoing risk they pose, significantly in their targeting of individuals in the delicate Kashmir area of India,” Cyble explained.
Found this report appealing? Follow us on Twitter and LinkedIn to read through a lot more exclusive content material we submit.
Some parts of this short article are sourced from:
thehackernews.com

 Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware
Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware