A new phishing marketing campaign is leveraging decoy Microsoft Word paperwork as bait to deliver a backdoor prepared in the Nim programming language.
“Malware written in uncommon programming languages puts the security group at a downside as researchers and reverse engineers’ unfamiliarity can hamper their investigation,” Netskope scientists Ghanashyam Satpathy and Jan Michael Alcantara said.
Nim-centered malware has been a rarity in the danger landscape, although that has been gradually changing in recent a long time as attackers continue on to either establish tailor made tools from scratch utilizing the language or port existing versions of their nefarious packages to it.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This has been demonstrated in the case of loaders this sort of as NimzaLoader, Nimbda, IceXLoader, as very well as ransomware families tracked beneath the names Dark Electrical power and Kanti.
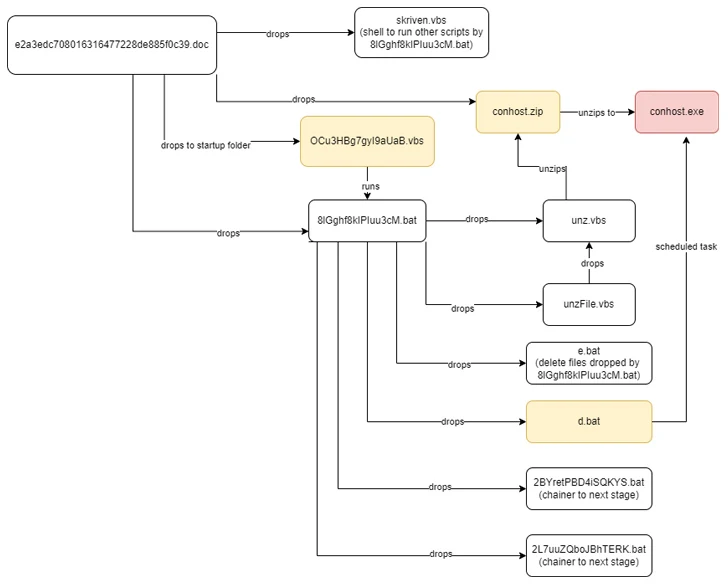
The attack chain documented by Netskope starts with a phishing email made up of a Phrase document attachment that, when opened, urges the receiver to allow macros to activate the deployment of the Nim malware. The email sender disguises them selves as a Nepali governing administration formal.
Once introduced, the implant is accountable for enumerating jogging processes to decide the existence of identified evaluation equipment on the infected host and immediately terminate itself should it uncover just one.
Future WEBINAR Beat AI-Driven Threats with Zero Rely on – Webinar for Security Gurus
Common security actions would not lower it in present-day globe. It can be time for Zero Have faith in Security. Protected your information like hardly ever in advance of.
Join Now
If not, the backdoor establishes connections with a remote server that mimics a govt area from Nepal, including the National Info Technology Heart (NITC) and awaits further more guidance. The command-and-handle (C2) servers are no more time accessible –
- mail[.]mofa[.]govnp[.]org
- nitc[.]govnp[.]org
- mx1[.]nepal[.]govnp[.]org
- dns[.]govnp[.]org
“Nim is a statically typed compiled programming language,” the researchers stated. “Aside from its familiar syntax, its cross-compilation capabilities let attackers to create just one malware variant and have it cross-compiled to focus on various platforms.”
The disclosure will come as Cyble revealed a social engineering campaign that leverages messages on social media platforms to provide a new Python-based stealer malware known as Editbot Stealer which is intended to harvest and exfiltrate worthwhile info through an actor-controlled Telegram channel.
Even as threat actors are experimenting with new malware strains, phishing campaigns have also been observed distributing identified malware these kinds of as DarkGate and NetSupport RAT by way of email and compromised internet sites with bogus update lures (aka RogueRaticate), particularly those people from a cluster dubbed BattleRoyal.
Business security business Proofpoint explained it recognized at minimum 20 campaigns that utilized DarkGate malware amongst September and November 2023, in advance of switching to NetSupport RAT before this thirty day period.
One particular attack sequence identified in early October 2023 specifically stands out for chaining two traffic delivery devices (TDSs) – 404 TDS and Keitaro TDS – to filter and redirect victims conference their conditions to an actor-operated area hosting a payload that exploited CVE-2023-36025 (CVSS score: 8.8), a large-severity Windows SmartScreen security bypass that was tackled by Microsoft in November 2023.

This indicates BattleRoyal weaponized this vulnerability as a zero-working day a thirty day period right before it was publicly revealed by the tech huge.
DarkGate is intended to steal information and facts and down load extra malware payloads, though NetSupport RAT, which began off as a bona fide distant administration software, has metamorphosed into a powerful weapon wielded by malevolent actors to infiltrate devices and establish unfettered distant manage.
“Cybercriminal menace actors [are] adopting new, assorted, and ever more creative attack chains – which include the use of various TDS resources – to help malware shipping,” Proofpoint said.
“Also, the use of the two email and phony update lures shows the actor making use of a number of forms of social engineering procedures in an try to get buyers to put in the ultimate payload.”
DarkGate has also been place to use by other threat actors like TA571 and TA577, both of those of which are identified to disseminate a wide variety of malware, like AsyncRAT, NetSupport, IcedID, PikaBot, and QakBot (aka Qbot).
“TA577 for instance, a single of the most well known Qbot distributors, returned to email menace info in September to produce DarkGate malware and has considering that been observed offering PikaBot in campaigns that usually have tens of countless numbers of messages,” Selena Larson, senior danger intelligence analyst at Proofpoint, explained to The Hacker Information.
Located this short article interesting? Follow us on Twitter and LinkedIn to examine more unique material we article.
Some pieces of this post are sourced from:
thehackernews.com

 UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware
UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware