The threat actor acknowledged as UAC-0099 has been connected to continued attacks aimed at Ukraine, some of which leverage a substantial-severity flaw in the WinRAR software package to supply a malware pressure termed LONEPAGE.
“The risk actor targets Ukrainian personnel doing work for companies outside the house of Ukraine,” cybersecurity firm Deep Instinct mentioned in a Thursday assessment.
UAC-0099 was initial documented by the Laptop Unexpected emergency Response Team of Ukraine (CERT-UA) in June 2023, detailing its attacks versus point out companies and media entities for espionage motives.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Approaching WEBINAR Conquer AI-Powered Threats with Zero Have confidence in – Webinar for Security Gurus
Common security measures will never reduce it in today’s globe. It can be time for Zero Belief Security. Secure your data like in no way prior to.
Be a part of Now
The attack chains leveraged phishing messages that contains HTA, RAR, and LNK file attachments that led to the deployment of LONEPAGE, a Visible Basic Script (VBS) malware that’s capable of getting in touch with a command-and-manage (C2) server to retrieve additional payloads such as keyloggers, stealers, and screenshot malware.
“For the duration of 2022-2023, the described team been given unauthorized remote entry to many dozen pcs in Ukraine,” CERT-UA mentioned at the time.
The latest examination from Deep Intuition reveals that the use of HTA attachments is just one of a few unique bacterial infections, the other two of which leverage self-extracting (SFX) archives and bobby-trapped ZIP information, which exploit the WinRAR vulnerability (CVE-2023-38831, CVSS score: 7.8) to distribute LONEPAGE.
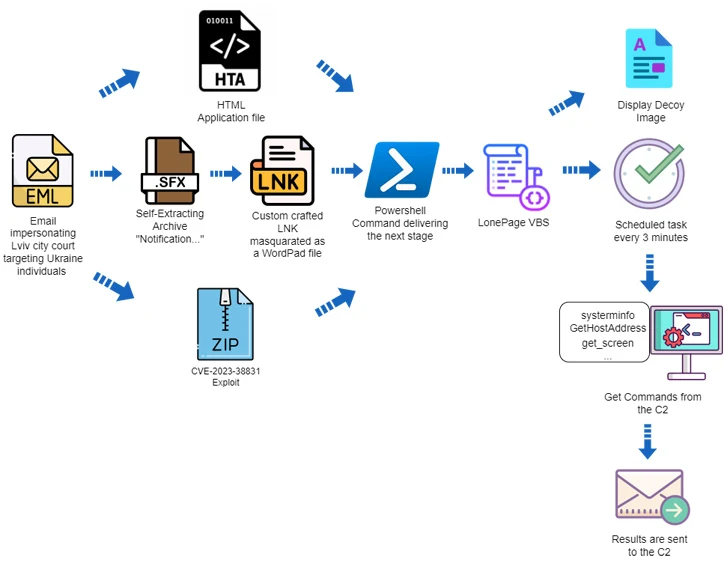
In the previous, the SFX file houses an LNK shortcut that’s disguised as a DOCX file for a court summons though working with the icon for Microsoft WordPad to entice the target into opening it, resulting in the execution of malicious PowerShell code that drops the LONEPAGE malware.
The other attack sequence works by using a specially crafted ZIP archive that is susceptible to CVE-2023-38831, with Deep Intuition obtaining two these kinds of artifacts produced by UAC-0099 on August 5, 2023, three days after WinRAR maintainers launched a patch for the bug.

“The methods utilised by ‘UAC-0099’ are straightforward, still helpful,” the business mentioned. “Regardless of the unique first an infection vectors, the main infection is the very same — they count on PowerShell and the generation of a scheduled task that executes a VBS file.”
The advancement arrives as CERT-UA warned of a new wave of phishing messages purporting to be excellent Kyivstar dues to propagate a remote accessibility trojan recognized as Remcos RAT. The agency attributed the marketing campaign to UAC-0050.
Discovered this write-up exciting? Abide by us on Twitter and LinkedIn to examine extra exceptional information we article.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Warns of New ‘FalseFont’ Backdoor Targeting the Defense Sector
Microsoft Warns of New ‘FalseFont’ Backdoor Targeting the Defense Sector