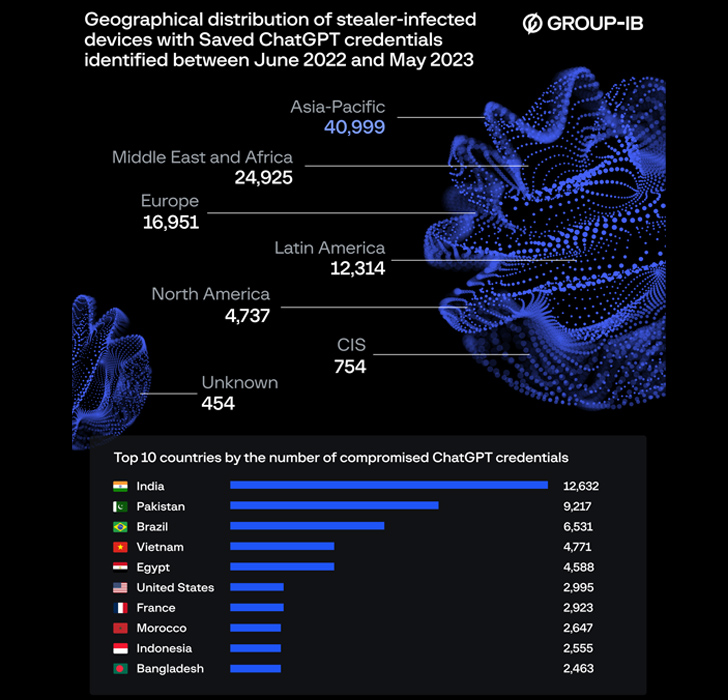
Over 100,000 compromised OpenAI ChatGPT account qualifications have observed their way on illicit dark web marketplaces between June 2022 and May well 2023, with India alone accounting for 12,632 stolen credentials.
The qualifications were found out in information stealer logs built offered for sale on the cybercrime underground, Team-IB claimed in a report shared with The Hacker News.
“The quantity of out there logs made up of compromised ChatGPT accounts arrived at a peak of 26,802 in May possibly 2023,” the Singapore-headquartered firm explained. “The Asia-Pacific location has experienced the greatest concentration of ChatGPT qualifications staying supplied for sale above the past 12 months.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Other international locations with the most variety of compromised ChatGPT qualifications include things like Pakistan, Brazil, Vietnam, Egypt, the U.S., France, Morocco, Indonesia, and Bangladesh.
A additional examination has exposed that the bulk of logs made up of ChatGPT accounts have been breached by the notorious Raccoon information stealer, adopted by Vidar and RedLine.

Data stealers have grow to be preferred amid cybercriminals for their capability to hijack passwords, cookies, credit rating cards, and other data from browsers, and cryptocurrency wallet extensions.
“Logs containing compromised info harvested by information stealers are actively traded on dark web marketplaces,” Team-IB claimed.
“Added data about logs out there on this kind of marketplaces includes the lists of domains located in the log as effectively as the information about the IP handle of the compromised host.”
Typically offered dependent on a subscription-based mostly pricing model, they have not only lowered the bar for cybercrime, but also provide as a conduit for launching follow-on attacks using the siphoned qualifications.
“Several enterprises are integrating ChatGPT into their operational flow,” Dmitry Shestakov, head of menace intelligence at Group-IB, claimed.
“Staff enter categorized correspondences or use the bot to enhance proprietary code. Presented that ChatGPT’s regular configuration retains all conversations, this could inadvertently offer you a trove of delicate intelligence to risk actors if they acquire account qualifications.”
To mitigate these challenges, it really is suggested that buyers stick to ideal password hygiene techniques and secure their accounts with two-factor authentication (2FA) to avoid account takeover attacks.
The development will come amid an ongoing malware campaign that’s leveraging bogus OnlyFans webpages and adult information lures to produce a remote obtain trojan and an facts stealer referred to as DCRat (or DarkCrystal RAT), a modified edition of AsyncRAT.
Upcoming WEBINAR🔐 Mastering API Security: Knowing Your Genuine Attack Surface
Find out the untapped vulnerabilities in your API ecosystem and just take proactive actions toward ironclad security. Be part of our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:right afterdisplay screen:inline-block.check out_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-prime-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-weight:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-prime:2px good #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-fat:900textual content-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-size:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
“In noticed situations, victims have been lured into downloading ZIP information containing a VBScript loader which is executed manually,” eSentire scientists claimed, noting the exercise has been underway given that January 2023.
“File naming conference implies the victims were being lured using express images or OnlyFans articles for a variety of grownup movie actresses.”
It also follows the discovery of a new VBScript variant of a malware identified as GuLoader (aka CloudEyE) that employs tax-themed decoys to start PowerShell scripts capable of retrieving and injecting Remcos RAT into a legit Windows procedure.
“GuLoader is a extremely evasive malware loader usually used to deliver data-stealers and Remote Administration Tools (RATs),” the Canadian cybersecurity organization mentioned in a report published before this thirty day period.
“GuLoader leverages user-initiated scripts or shortcut data files to execute many rounds of remarkably obfuscated commands and encrypted shellcode. The result is a memory-resident malware payload running inside of a respectable Windows method.”
Identified this write-up attention-grabbing? Comply with us on Twitter and LinkedIn to read additional exceptional written content we write-up.
Some elements of this report are sourced from:
thehackernews.com


 Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign
Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign