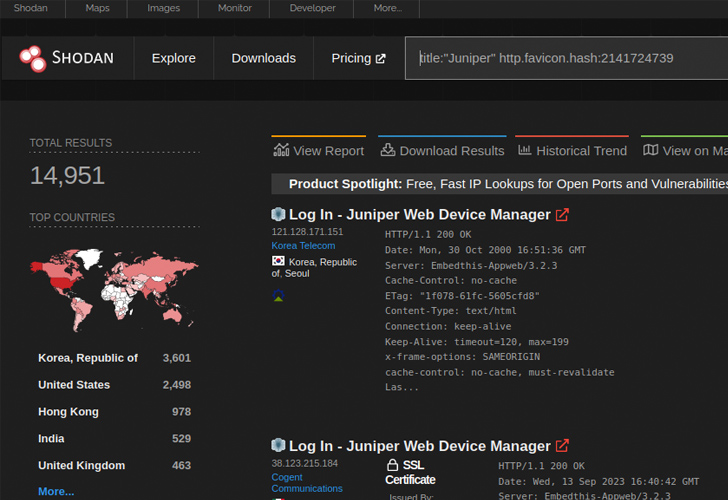
New investigate has uncovered that shut to 12,000 internet-uncovered Juniper firewall equipment are susceptible to a recently disclosed distant code execution flaw.
VulnCheck, which found out a new exploit for CVE-2023-36845, explained it could be exploited by an “unauthenticated and remote attacker to execute arbitrary code on Juniper firewalls without having generating a file on the method.”
CVE-2023-36845 refers to a medium-severity flaw in the J-Web component of Junos OS that could be weaponized by a risk actor to command certain, significant ecosystem variables. It was patched by Juniper Networks final month alongside CVE-2023-36844, CVE-2023-36846, and CVE-2023-36847 in an out-of-cycle update.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

A subsequent evidence-of-principle (PoC) exploit devised by watchTowr put together CVE-2023-36846 and CVE-2023-36845 to add a PHP file containing destructive shellcode and achieve code execution.
The latest exploit, on the other hand, impacts more mature techniques and can be composed applying a one cURL command. Particularly, it relies on just CVE-2023-36845 to comprehend the same goal.
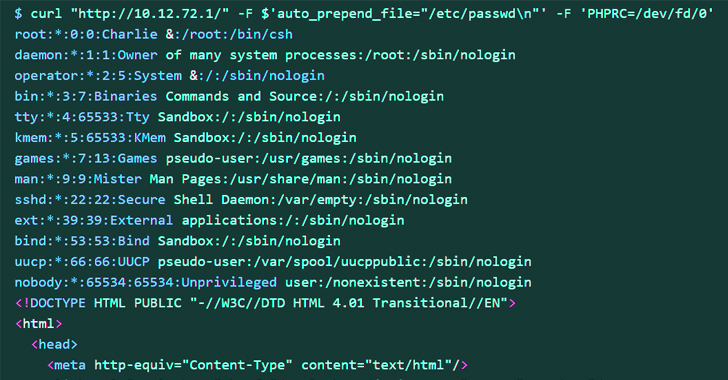
This, in transform, is attained by employing the common input stream (aka stdin) to set the PHPRC surroundings variable to “/dev/fd/” by way of a specially crafted HTTP ask for, efficiently turning “/dev/fd/” into a makeshift file, and leak sensitive info.
Arbitrary code execution is then realized by leveraging PHP’s automobile_prepend_file and allow for_url_incorporate possibilities in conjunction with the information:// protocol wrapper.
Forthcoming WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Fashionable Age
Dive deep into the long run of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why identification is the new endpoint. Secure your place now.
Supercharge Your Capabilities
“Firewalls are attention-grabbing targets to APT as they assistance bridge into the safeguarded network and can provide as valuable hosts for C2 infrastructure,” Jacob Baines reported. “Everyone who has an unpatched Juniper firewall should really analyze it for signals of compromise.”
Juniper has considering that disclosed that it can be not conscious of a effective exploit in opposition to its prospects, but warned that it has detected exploitation tries in the wild, earning it vital that users apply the needed fixes to mitigate opportunity threats.
Discovered this post exciting? Stick to us on Twitter and LinkedIn to read through additional special information we publish.
Some parts of this post are sourced from:
thehackernews.com

 Transparent Tribe Uses Fake YouTube Android Apps to Spread CapraRAT Malware
Transparent Tribe Uses Fake YouTube Android Apps to Spread CapraRAT Malware