The Pakistan-primarily based highly developed persistent threat (APT) actor known as Transparent Tribe used a two-factor authentication (2FA) resource employed by Indian federal government agencies as a ruse to supply a new Linux backdoor identified as Poseidon.
“Poseidon is a 2nd-phase payload malware involved with Transparent Tribe,” Uptycs security researcher Tejaswini Sandapolla mentioned in a technological report printed this 7 days.
“It is a common-reason backdoor that gives attackers with a extensive selection of abilities to hijack an infected host. Its functionalities incorporate logging keystrokes, taking display captures, uploading and downloading files, and remotely administering the technique in several methods.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Clear Tribe is also tracked as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, and has a keep track of file of focusing on Indian governing administration organizations, army staff, protection contractors, and academic entities.
It has also repeatedly leveraged trojanized versions of Kavach, the Indian authorities-mandated 2FA program, to deploy a wide variety of malware, such as CrimsonRAT and LimePad to harvest worthwhile facts.
A further phishing marketing campaign detected late last calendar year took gain of weaponized attachments to download malware made to exfiltrate database information made by the Kavach app.
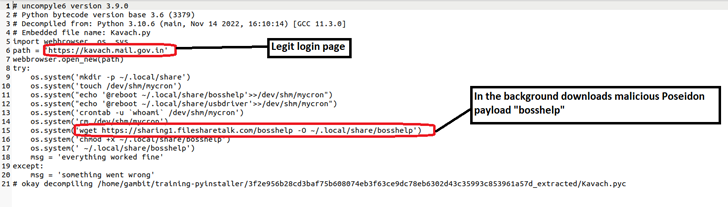
The most current established of attacks entail the use of a backdoored version of Kavach to focus on Linux customers doing the job for Indian federal government companies, indicating tries created by the danger actor to expand its attack spectrum past Windows and Android ecosystems.
“When a user interacts with the destructive variation of Kavach, the genuine login webpage is shown to distract them,” Sandapolla described. “In the meantime, the payload is downloaded in the history, compromising the user’s process.”
Forthcoming WEBINARMaster the Artwork of Dark Web Intelligence Collecting
Learn the art of extracting danger intelligence from the dark web – Be part of this skilled-led webinar!
Preserve My Seat!
The starting up point of the infections is an ELF malware sample, a compiled Python executable which is engineered to retrieve the 2nd-phase Poseidon payload from a remote server.
The cybersecurity organization observed that the phony Kavach applications are principally distributed by way of rogue sites that are disguised as legit Indian government web sites. This contains www.ksboard[.]in and www.rodra[.]in.
With social engineering currently being the key attack vector utilised by Transparent Tribe, people doing work inside the Indian federal government are suggested to double-verify URLs been given in emails prior to opening them.
“Repercussions of this APT36 attack could be important, top to loss of sensitive information and facts, compromised methods, economical losses, and reputational damage,” Sandapolla claimed.
Located this article appealing? Abide by us on Twitter and LinkedIn to read a lot more distinctive written content we write-up.
Some sections of this post are sourced from:
thehackernews.com


 Uncovering (and Understanding) the Hidden Risks of SaaS Apps
Uncovering (and Understanding) the Hidden Risks of SaaS Apps