Modern data breaches across CircleCI, LastPass, and Okta underscore a frequent topic: The enterprise SaaS stacks related to these industry-foremost apps can be at significant risk for compromise.
CircleCI, for instance, performs an integral, SaaS-to-SaaS position for SaaS application development. Equally, tens of 1000’s of organizations rely on Okta and LastPass security roles for SaaS id and obtain management. Company and niche SaaS applications alike have correctly launched multitudes of unmonitored endpoints into organizations of all measurements.
Whilst spending for SaaS security is trending up, it lags behind classes these types of as cloud infrastructure defense and network security. According to Statista, the normal group employs 100+ SaaS applications, many of which are unsanctioned by IT, making a evident hole in SaaS security.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Why End users Flock to SaaS Applications — And Normally Bypass IT in the Method
As productivity applications for duties this sort of as advertising and marketing automation, document signature, and sales forecasting have shifted from set up software package to SaaS, so have the behaviors of close-consumers. Staff members find SaaS solutions to support them achieve more in much less time, in particular with the raising decentralization of the IT operate.
Staff members will constantly search for methods to boost their efficiency with instruments of their selection. This actions is almost nothing novel or in and of alone destructive, but it poses substantial security dangers. In the period of mounted application, corporations included endpoint security to get the job done machines and gadgets to make certain their workers could not obtain harmful program or fall target to malware-primarily based attacks. This tactic remains a vital side of over-all endpoint security, but it will not replicate the evolution of the way folks are now working: exterior the purview of corporate networks, and normally on personalized units.
Relatively than approaching Security or IT to realize guidelines for onboarding new SaaS methods — and dealing with the likelihood of purple tape, delays, or denial for their requests — they split out the credit card or decide for a 30-working day free of charge trial of the SaaS apps. Staff seldom contemplate the security implications of the shadow IT they have launched into the ecosystem as they authorize connecting their new applications to company SaaS units this sort of as Microsoft 365, Salesforce, Workday, or ServiceNow.
These connections, coupled with the users’ inherited permission settings, could contact the organization’s most sensitive information, with no ability to monitor or regulate this attack floor risk. And it takes place each and every day.
AppOmni: SaaS Security and SSPM System
Secure your business’s useful details across a number of purposes with AppOmni’s powerful SaaS security management program. Obtain insights and visibility to safeguard in opposition to prospective security threats. Our cutting-edge technology guarantees protection against publicly-exposed SaaS knowledge, over-privileged exterior buyers, 3rd-party programs, and additional. Relaxation quick knowing your company’s knowledge is in great hands with AppOmni. Try it now.
Ask for a Demo
How SaaS Applications Inherit Permissions through OAuth Tokens
In numerous businesses, the SaaS applications (and SaaS-to-SaaS connections) capitalize on OAuth obtain tokens both of those at the level of preliminary connection and through their lifecycle. The system ordinarily follows these techniques:
- A consumer has been authenticated into an enterprise SaaS application, regardless of whether through uncomplicated authentication or potent zero rely on authentication. They’re now in the SaaS cloud.
- That user wishes to conserve time toggling concerning their task management software and documents, spreadsheets, and e-mails. Appropriately, they research for ways to streamline their do the job. That research qualified prospects to a well known project management SaaS plug-in, perhaps with a absolutely free trial, and the person decides to try out it.
- The user starts the set up and clicks on “Indeed” to a prompt authorizing read-compose obtain to knowledge in a key SaaS system like an business efficiency suite, and the info affiliated with it. There are no tiers of different authorization rights for the user to pick.
- An OAuth token is designed by the business office productiveness suite. This token will allow the venture administration app and business office productivity suite to sustain API-centered cloud-to-cloud interaction with no the person getting to log in and authenticate routinely.
From this issue ahead, the task management app is frequently linked after the first solid authentication. CASBs and SWGs will not detect this SaaS-to-SaaS connectivity.
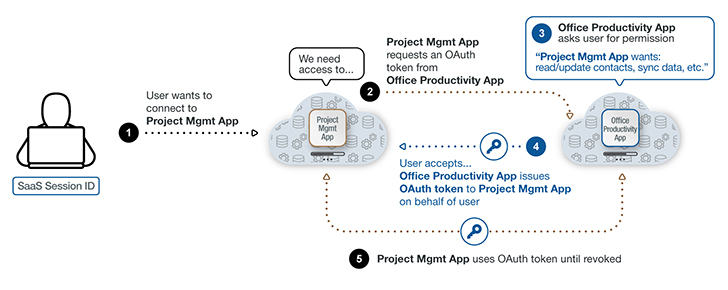 Determine 1: A breakdown of how a SaaS-to-SaaS connection interacts with an OAuth token.
Determine 1: A breakdown of how a SaaS-to-SaaS connection interacts with an OAuth token.
These software tokens are useful mainly because they make the job administration application conveniently available for the consumer. Unfortunately, they’re equally, if not extra, important for attackers looking for an simply exploitable entry position into an enterprise SaaS method.
The Attain — and Risk — SaaS Applications and SaaS-to-SaaS Connections Existing
If danger actors can properly hijack OAuth tokens, they can attain entry into CRMs, code repos, and more. 1 compromised SaaS-to-SaaS relationship can provide valid, authorized API access into a multiplicity of distinct generation SaaS environments and data.
Security and IT teams are overburdened with checking and protecting the configuration options and advancement of their organization SaaS platforms, enable by yourself unauthorized SaaS applications. With out any security overview, SaaS-to-SaaS connections generate most likely vulnerable endpoints.
The prevalence of these SaaS-to-SaaS connections is substantial and regularly underestimated by IT corporations. According to SaaS security company AppOmni:
- The common company firm has additional than 42 unique SaaS-to-SaaS applications related into live SaaS environments inside an company. Approximately 50 percent of these apps were being related directly by end-buyers, not by IT teams.
- Approximately half of these 42 connected apps have not been employed in the previous 6 months. No matter if lively or dormant, related SaaS-to-SaaS applications retain their information entry rights.
- Lots of of these corporations have achieved a whole of virtually 900 consumer-to-software connections.
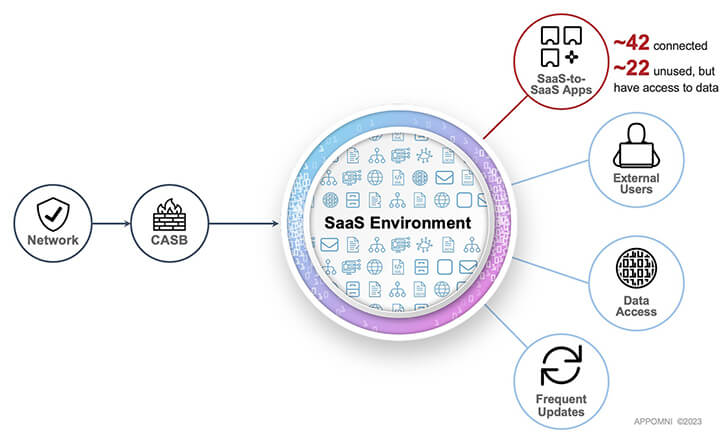 Determine 2: SaaS environments contain several entry factors outside the house classic network and CASB defense.
Determine 2: SaaS environments contain several entry factors outside the house classic network and CASB defense.
As this analysis demonstrates, the selection of “licensed” applications in contact with potentially sensitive info is infeasible to evaluate and observe without the need of the accurate SaaS security tooling.
Practical Ways for Checking and Securing SaaS Connections
Most Security groups lack the proper tooling to achieve visibility into SaaS connectivity and the linked person exercise. SaaS Security Posture Administration (SSPM) options address these fears by bringing visibility and control more than the SaaS estate.
A Security or IT skilled can, for occasion, utilize SSPM to explore almost everything managing in Salesforce, together with the SaaS applications related to it. The same is correct for several other SaaS applications utilized by the group.
This extra visibility and command in ongoing checking of SaaS apps and SaaS-to-SaaS connections minimizes attack surface area risk and allows proactive security manage. If a vulnerability is uncovered, the Security staff can consider action, this sort of as pinpointing unsanctioned, unsecure, and above-permissioned SaaS applications.
Thanks to an SSPM solution’s continual monitoring abilities, the Security crew is able to figure out a baseline of SaaS activity to use as a time-in-point body of reference. Even though the likely for a SaaS-associated breach can under no circumstances be entirely eradicated, utilizing SSPM drives down that risk considerably.
Identified this article fascinating? Observe us on Twitter and LinkedIn to go through extra exceptional material we post.
Some areas of this post are sourced from:
thehackernews.com

 Police Escape $1.2m Fine For Secretly Recording Phone Calls
Police Escape $1.2m Fine For Secretly Recording Phone Calls