Credit history: Marina Minkin
A novel attack technique has been disclosed from a crucial piece of technology termed time-triggered ethernet (TTE) which is applied in security-critical infrastructure, possibly leading to the failure of techniques powering spacecraft and aircraft.
Dubbed PCspooF by a group of academics and scientists from the University of Michigan, the College of Pennsylvania, and the NASA Johnson Room Heart, the technique is made to split TTE’s security guarantees and induce TTE equipment to shed synchronization for up to a 2nd, a behavior that can even lead to uncontrolled maneuvers in spaceflight missions and threaten crew basic safety.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
TTE is one particular between the networking technologies which is element of what is actually known as a combined-criticality network wherein targeted visitors with distinct timing and faults tolerance demands coexist in the exact physical network. This signifies that both equally critical units, which, say, enable car management, and non-critical equipment, which are applied for checking and details assortment, share the exact same network.
An obvious advantage to this technique is the actuality that there are lesser weight and energy necessities as effectively as lessen improvement and time expenses stemming as a final result of relying on just just one technology. But this also will come with drawbacks of its personal.
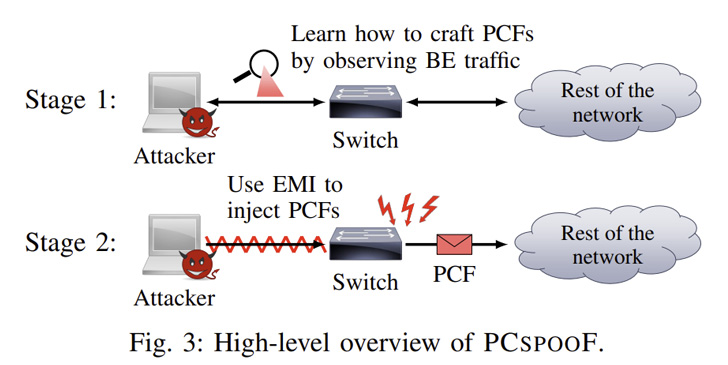
“This mixed-criticality solution puts a great deal much more strain on the design and style of the network to offer isolation,” Andrew Loveless, the guide author of the study, informed The Hacker Information. “Now that critical and non-critical products may well join to the exact switch, the network protocol and hardware have to have to do excess work to make guaranteed the critical targeted visitors is generally confirmed to get by way of efficiently and on time.”
 Credit rating: European House Company
Credit rating: European House Company
On top rated of that, although critical products in the network are subjected to thorough vetting, the non-critical counterparts are not only business-off-the-shelf (COTS) products but also absence the exact same arduous process, primary to achievable avenues for supply chain compromises that could be weaponized to activate the attack by integrating a rogue third-party component into the program.
This is wherever a combined-criticality network will help be certain that even if the COTS gadget is malicious, it can’t interfere with critical site visitors.
“In PCspooF, we uncovered a way for a malicious non-critical system to crack this isolation assure in a TTE network,” Baris Kasikci, an assistant professor in the electrical engineering and computer system science office at the College of Michigan, told the publication.
This, in transform, is accomplished by utilizing the nefarious system to inject electromagnetic interference (EMI) into a TTE switch around an Ethernet cable, efficiently tricking the change into sending authentic-looking synchronization messages (i.e., protocol regulate frames or PCFs) and get them accepted by other TTE units.
These an “electrical noise” technology circuit can get up as small as 2.5cm × 2.5cm on a single-layer printed circuit board, demanding only negligible ability and which can be concealed in a finest-work machine and integrated into a TTE method with no raising any red flags.

As mitigations, the review suggests making use of optocouplers or surge protectors to block electromagnetic interference, checking the source MAC addresses to ensure they’re reliable, hiding critical PCF fields, applying a website link-layer authentication protocol like IEEE 802.1AE, growing the amount of sync masters, and disabling dangerous state transitions.
The results show that the use of widespread components in a system engineered to deliver demanding isolation assurances can at times defeat all those really protections, the scientists pointed out, adding blended-criticality program units must be examined meticulously in a identical manner to assure the isolation mechanisms are foolproof.
“The TTE protocols are pretty experienced and perfectly-vetted, and a lot of of the most crucial components are formally confirmed,” Kasikci reported.
“In a way that is what makes our attack exciting – that we were capable to figure out how to violate some ensures of the protocol despite its maturity. But to do that, we had to consider exterior the box and determine out how to make the hardware behave in a way the protocol does not count on.”
Located this write-up interesting? Abide by THN on Fb, Twitter and LinkedIn to study far more unique material we article.
Some areas of this post are sourced from:
thehackernews.com


 Lazarus Backdoor DTrack Evolves to Target Europe and Latin America
Lazarus Backdoor DTrack Evolves to Target Europe and Latin America