Spotify’s Backstage has been identified as susceptible to a serious security flaw that could be exploited to achieve remote code execution by leveraging a recently disclosed bug in a 3rd-party module.
The vulnerability (CVSS score: 9.8), at its core, takes advantage of a critical sandbox escape in vm2, a preferred JavaScript sandbox library (CVE-2022-36067 aka Sandbreak), that arrived to light-weight last month.
“An unauthenticated risk actor can execute arbitrary method instructions on a Backstage application by exploiting a vm2 sandbox escape in the Scaffolder main plugin,” application security business Oxeye said in a report shared with The Hacker Information.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Backstage is an open up supply developer portal from Spotify that permits users to create, regulate, and investigate software parts from a unified “front doorway.” It can be employed by quite a few providers like Netflix, DoorDash, Roku, and Expedia, amongst other folks.
In accordance to Oxeye, the flaw is rooted in a device referred to as software package templates that can be utilised to generate factors within Backstage.
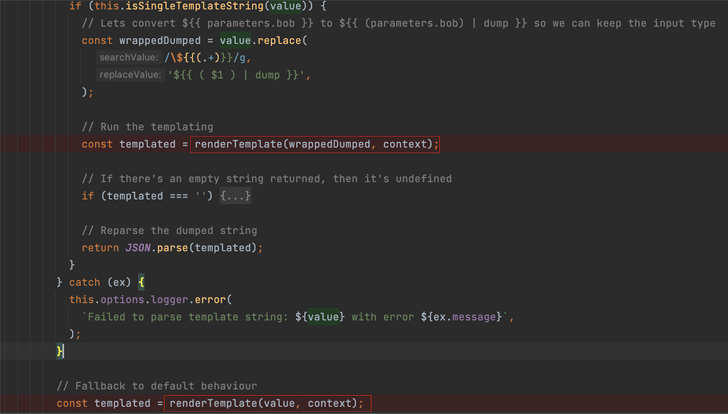 Screenshot demonstrates Backstage contacting the renderTemplate operate (that phone calls renderString2) 2 times in the party of an error.
Screenshot demonstrates Backstage contacting the renderTemplate operate (that phone calls renderString2) 2 times in the party of an error.
Even though the template engine utilizes vm2 to mitigate the risk linked with functioning untrusted code, the sandbox escape flaw in the latter created it possible to execute arbitrary process commands exterior of the security perimeter.
Oxeye stated it was in a position to recognize far more than 500 publicly-exposed Backstage scenarios on the internet, which could then be remotely weaponized by an adversary with no necessitating any authorization.

Following accountable disclosure on August 18, the issue was resolved by the undertaking maintainers in edition 1.5.1 unveiled on August 29, 2022.
“The root of any template-centered VM escape is attaining JavaScript execution rights inside the template,” the Israeli organization famous. “By using ‘logic-less’ template engines this kind of as Mustache, you can stay away from introducing server-facet template injection vulnerabilities.”
“Separating the logic from the presentation as a lot as feasible can greatly decrease your publicity to the most risky template-dependent attacks,” it more additional.
Located this short article attention-grabbing? Observe THN on Facebook, Twitter and LinkedIn to study additional distinctive articles we put up.
Some elements of this write-up are sourced from:
thehackernews.com


 PCSpoof: New Vulnerability Affects Networking Tech Used by Spacecraft and Aircraft
PCSpoof: New Vulnerability Affects Networking Tech Used by Spacecraft and Aircraft