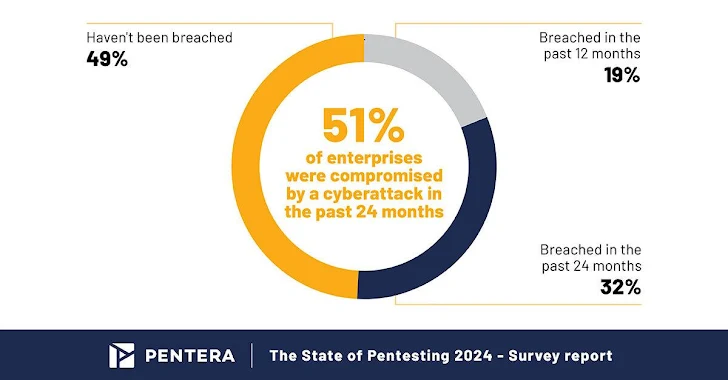
Above the past two several years, a surprising 51% of corporations surveyed in a major market report have been compromised by a cyberattack. Yes, around 50 %.
And this, in a environment where enterprises deploy an normal of 53 diverse security solutions to safeguard their electronic domain.
Alarming? Certainly.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A recent study of CISOs and CIOs, commissioned by Pentera and executed by World wide Surveyz Investigation, delivers a quantifiable glimpse into this evolving battlefield, revealing a stark contrast between the expanding threats and the tightening spending budget constraints less than which cybersecurity experts run.
With this report, Pentera has at the time once again taken a magnifying glass to the point out of pentesting to launch its once-a-year report about present day pentesting tactics. Engaging with 450 security executives from North America, LATAM, APAC, and EMEA—all in VP or C-level positions at corporations with more than 1,000 employees—the report paints a present photograph of contemporary security validation procedures across the company.
Critical results incorporate:
- The influence of a breach is substantial:
- 43% noted unplanned downtime
- 36% claimed details exposure
- 31% reported economical reduction
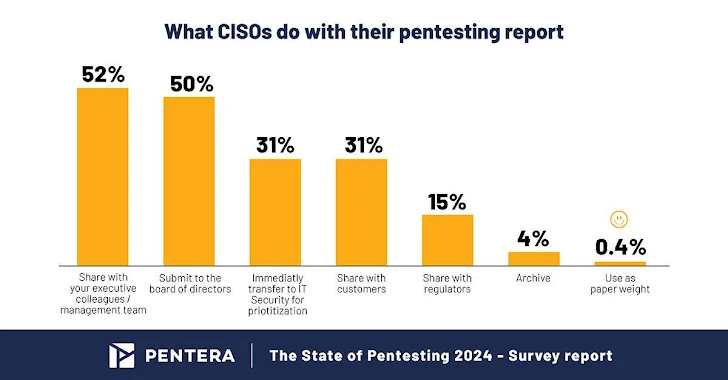
- As Board of Administrators (BoDs) turn out to be extra cyber mindful, about 50% of CISOs now share their pentesting stories with their BoDs.
- There is certainly a noteworthy gap involving the rate of improve in IT environments and the frequency of security tests, leaving organizations’ digital belongings untested for extended intervals of time.
- With an regular of 500 remediation activities for each week, efficient prioritization is 1 of the most crucial elements for security groups.

Security Breaches Persist Inspite of Investments
The 2024 report reveals that enterprises have an common of 53 security methods, however they are having difficulties to keep the Confidentiality, Integrity, Availability (CIA) triad. As element of security insurance policies and practices, this triad shields facts techniques and facts from a variety of threats, ensuring that data is secure, dependable, and obtainable to the proper individuals.
This truth is underscored by the fact that 51% of CISOs surveyed admitted to a cybersecurity breach in the previous two years. This kind of breaches have led to sizeable operational disruptions, which includes unplanned downtime, details exposure, and economical losses. Only 7% of enterprises averted substantial influence ensuing from a breach. These incidents show the great importance of getting robust cybersecurity defenses.
Enterprises professional a practically equal distribution of attacks throughout their IT infrastructure like distant equipment, on-premise, and cloud environments, pointing to the need to have to regularly examination and secure each of these domains. The heightened profile of the cloud as an attack goal is regular with other business reviews. Crowdstrike’s World Risk Report for 2024 documented a 75% increase in cloud intrusions YoY. They projected that in the coming years, as a lot more businesses progress with their cloud migration initiatives and shift toward predominantly cloud or cloud-indigenous deployments, this determine will raise.
Improved Executive and Board Involvement
In light of superior-profile breaches creating headlines, there’s a noteworthy surge in cybersecurity oversight from the top rated. Above half of the CISOs now often report pentest results to their boards of administrators, highlighting the strategic importance of cybersecurity to the organization. CISOs are more and more utilizing pentest stories as a way to much better connect cybersecurity challenges to their govt teams and boards.
Also, 31% of CISOs share pentest outcomes with customers, acknowledging the value of transparency in handling 3rd-party and supply chain threats. Adopting this exercise not only builds have confidence in but also encourages a culture of openness about cybersecurity difficulties and actions.
Closing the Pentesting Hole
The study highlights a disconcerting gap among the frequency of IT atmosphere adjustments and the cadence of security screening. When 73% of companies report earning quarterly IT modifications only 40% match this pace with their pentesting efforts. This leaves companies open up to risk for extended periods.
On typical, enterprises dedicate $164,400 to handbook pentesting, symbolizing 12.9% of their annual IT security price range. With 60% of businesses pentesting twice a year at most, this is a huge expenditure and a sizable part of the finances for a security action that gives just a snap-shot assessment of the security posture. Specified the significance of pentests to strengthening IT resilience, it really is truly worth taking into consideration options that give scalable ongoing pentesting.

Patch Fantastic Is not Practical
Beyond remediation pursuits, security teams are tasked with a varied established of obligations that stretch them to their restrictions.
From this backdrop, corporations are flooded with security occasions. With about 60% of enterprises reporting they acquire at minimum 500 incidents demanding remediation weekly, patch perfection has under no circumstances been additional elusive. It is significantly distinct that the artwork of prioritization is one that security teams will have to have to discover to maintain their organization’s perfectly-shielded. Security groups who are in a position to proficiently fully grasp the context of a vulnerability, its compensating controls, and the information it qualified prospects to will be the ones to keep in the game.
What do These Findings Indicate?
The Point out of Pentesting Study of 2024, by Pentera, underscores a critical juncture for cybersecurity: As threats keep on to evolve, several security methods are unsuccessful to mitigate them, necessitating CISOs to more regularly validate the security of their infrastructure.
The insights from this study are not just statistics—they are a call to action for improved, extra successful cybersecurity procedures that align with the economic and operational realities of our time.
Unpack key results from the 2024 Condition of Pentesting Survey in this webinar. Sign up for us as we examine the conclusions, focus on approaches to regulate cybersecurity, prioritize duties, and find out how to connect your security posture to leadership additional efficiently.
Obtain the 2024 Condition of Pentesting Study or sign-up listed here to go to the stay webinar.
Located this post appealing? This article is a contributed piece from 1 of our valued partners. Observe us on Twitter and LinkedIn to read a lot more special articles we article.
Some sections of this write-up are sourced from:
thehackernews.com


 MITRE Corporation Breached by Nation-State Hackers Exploiting Ivanti Flaws
MITRE Corporation Breached by Nation-State Hackers Exploiting Ivanti Flaws