The threat actor recognized as ToddyCat has been observed using a large variety of equipment to keep obtain to compromised environments and steal beneficial info.
Russian cybersecurity organization Kaspersky characterized the adversary as relying on a variety of systems to harvest information on an “industrial scale” from mainly governmental businesses, some of them protection related, positioned in the Asia-Pacific area.
“To gather substantial volumes of information from quite a few hosts, attackers need to automate the facts harvesting procedure as much as doable, and deliver a number of alternate suggests to continually access and keep an eye on devices they attack,” security researchers Andrey Gunkin, Alexander Fedotov, and Natalya Shornikova claimed.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
ToddyCat was initial documented by the firm in June 2022 in connection with a sequence of cyber attacks aimed at government and armed forces entities in Europe and Asia considering that at least December 2020. These intrusions leveraged a passive backdoor dubbed Samurai that will allow for distant entry to the compromised host.
A closer evaluation of the danger actor’s tradecraft has considering the fact that uncovered supplemental info exfiltration resources like LoFiSe and Pcexter to get information and add archive files to Microsoft OneDrive.

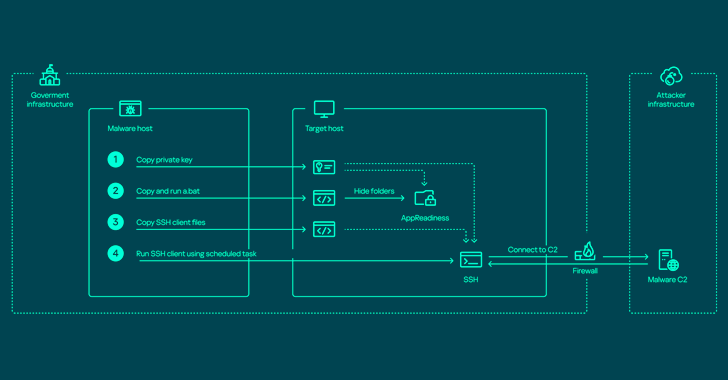
The most current set of packages entail a blend of tunneling info collecting application, which are set to use following the attacker has now obtained entry to privileged person accounts in the infected method. This contains –
- Reverse SSH tunnel using OpenSSH
- SoftEther VPN, which is renamed to seemingly innocuous information like “boot.exe,” “mstime.exe,” “netscan.exe,” and “kaspersky.exe”
- Ngrok and Krong to encrypt and redirect command-and-command (C2) site visitors to a certain port on the concentrate on procedure
- FRP shopper, an open-resource Golang-based mostly quick reverse proxy
- Cuthead, a .NET compiled executable to research for paperwork matching a specific extension or a filename, or the date when they are modified
- WAExp, a .NET plan to capture data involved with the WhatsApp web app and conserve it as an archive, and
- TomBerBil to extract cookies and credentials from web browsers like Google Chrome and Microsoft Edge
“The attackers are actively applying procedures to bypass defenses in an endeavor to mask their existence in the technique,” Kaspersky mentioned.

“To protect the organization’s infrastructure, we recommend incorporating to the firewall denylist the methods and IP addresses of cloud providers that give targeted traffic tunneling. In addition, buyers should be essential to prevent storing passwords in their browsers, as it helps attackers to obtain sensitive information and facts.”
Uncovered this posting fascinating? Comply with us on Twitter and LinkedIn to browse a lot more unique content we article.
Some areas of this short article are sourced from:
thehackernews.com

 Pentera’s 2024 Report Reveals Hundreds of Security Events per Week, Highlighting the Criticality of Continuous Validation
Pentera’s 2024 Report Reveals Hundreds of Security Events per Week, Highlighting the Criticality of Continuous Validation