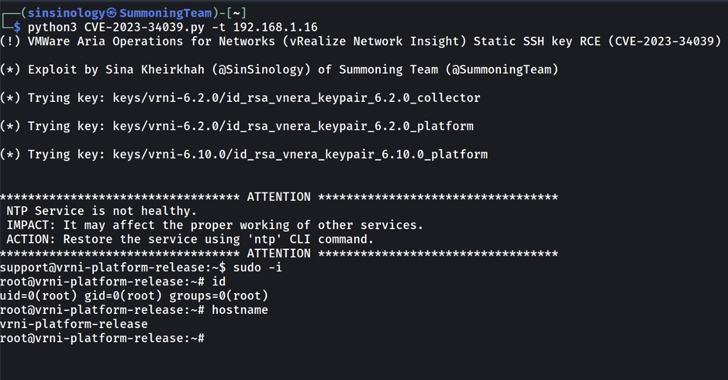
Evidence-of-notion (PoC) exploit code has been designed available for a lately disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Perception).
The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a utmost of 10 for severity and has been explained as a case of authentication bypass due to a deficiency of exceptional cryptographic key technology.
“A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to acquire obtain to the Aria Functions for Networks CLI,” VMware stated previously this week.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Summoning Team’s Sina Kheirkhah, who released the PoC adhering to an analyzing the patch by VMware, explained the root cause can be traced back to a bash script that contains a technique named refresh_ssh_keys(), which is accountable for overwriting the latest SSH keys for the aid and ubuntu end users in the licensed_keys file.
“There is SSH authentication in place even so, VMware forgot to regenerate the keys,” Kheirkhah stated. “VMware’s Aria Functions for Networks had hard-coded its keys from variation 6. to 6.10.”

VMware’s most up-to-date fixes also address CVE-2023-20890, an arbitrary file publish vulnerability impacting Aria Functions for Networks that could be abused by an adversary with administrative obtain to compose data files to arbitrary spots and realize remote code execution.
In other terms, a danger actor could leverage the PoC to obtain admin obtain to the machine and exploit CVE-2023-20890 to operate arbitrary payloads, creating it critical that people implement the updates to secure from possible threats.
The release of the PoC coincides with the virtualization technology giant issuing fixes for an superior-severity SAML token signature bypass flaw (CVE-2023-20900, CVSS score: 7.5) across various Windows and Linux versions of VMware Applications.
“A destructive actor with gentleman-in-the-middle (MITM) network positioning in the virtual equipment network might be ready to bypass SAML token signature verification, to accomplish VMware Applications Visitor Operations,” the corporation claimed in an advisory produced Thursday.
Peter Stöckli of GitHub Security Lab has been credited with reporting the flaw, which affects the adhering to variations –
- VMware Tools for Windows (12.x.x, 11.x.x, 10.3.x) – Fixed in 12.3.
- VMware Equipment for Linux (10.3.x) – Fastened in 10.3.26
- Open up-source implementation of VMware Instruments for Linux or open-vm-instruments (12.x.x, 11.x.x, 10.3.x) – Fixed in 12.3. (to be dispersed by Linux sellers)
The improvement also will come as Fortinet FortiGuard Labs warned of ongoing exploitation of Adobe ColdFusion Vulnerabilities by threat actors to deploy cryptocurrency miners and hybrid bots this kind of as Satan DDoS (aka Lucifer) and RudeMiner (aka SpreadMiner) that are able of carrying out cryptojacking and dispersed denial-of-service (DDoS) attacks.
Also deployed is a backdoor named BillGates (aka Setag), which is recognised for hijacking programs, stealing delicate data, and initiating DDoS attacks.
Located this short article fascinating? Abide by us on Twitter and LinkedIn to read through extra exclusive content material we put up.
Some pieces of this posting are sourced from:
thehackernews.com

 Okta Warns of Social Engineering Attacks Targeting Super Administrator Privileges
Okta Warns of Social Engineering Attacks Targeting Super Administrator Privileges