A new significant-scale smishing campaign is concentrating on the U.S. by sending iMessages from compromised Apple iCloud accounts with an purpose to carry out identity theft and money fraud.
“The Chinese-talking danger actors behind this marketing campaign are functioning a package-monitoring textual content rip-off despatched by using iMessage to acquire personally identifying information and facts (PII) and payment credentials from victims, in the furtherance of identification theft and credit rating card fraud,” Resecurity said in an assessment revealed previous 7 days.
The cybercrime team, dubbed Smishing Triad, is also reported to be in the organization of “fraud-as-a-services,” featuring other actors completely ready-to-use smishing kits through Telegram that expense $200 a month.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
These kits impersonate well-known postal and shipping and delivery providers in the U.S, the U.K, Poland, Sweden, Italy, Indonesia, Malaysia, Japan, and other countries.

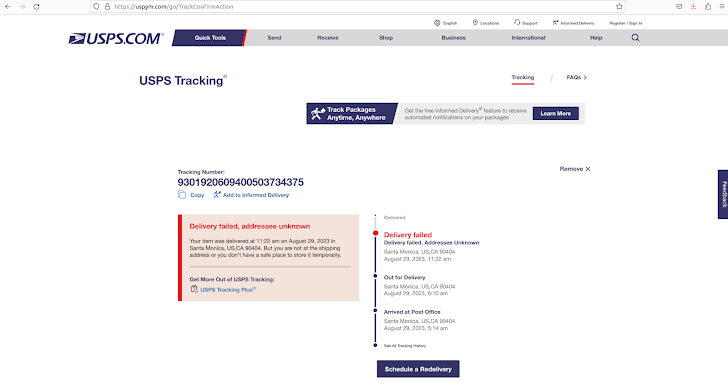
A stand-out factor of the exercise is the use of breached Apple iCloud accounts as a supply vector to ship package delivery failure messages, urging recipients to simply click on a connection to reschedule the delivery and enter their credit score card information and facts in a fake variety.
Resecurity’s analysis of the smishing package exposed an SQL injection vulnerability that it claimed allowed them to retrieve about 108,044 data of victims’ data.
“Thinking about the determined vulnerability or possible backdoor, it is attainable that critical customers of ‘Smishing Triad’ organized a covert channel to obtain success with intercepted individual and payment details from other customers and consumers leveraging their package,” the firm reported.
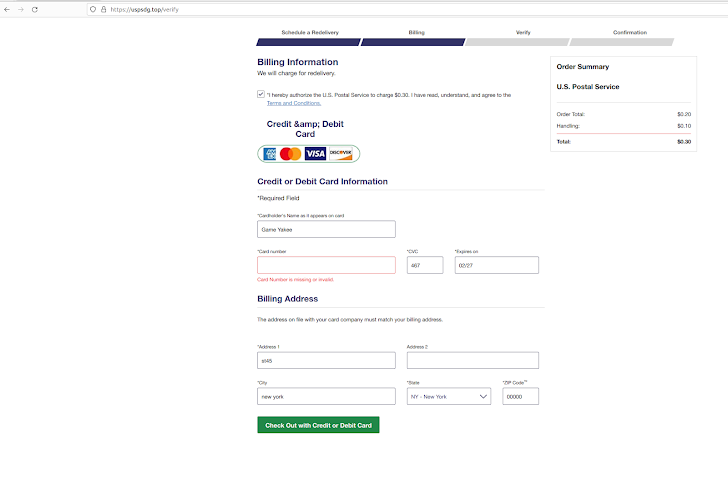
“This kind of tradecraft is commonly utilised by cybercriminals in password stealers and phishing kits, allowing them to income from the pursuits of their clientele, or at minimum to seamlessly keep track of their exercise just by logging into an administration panel.”
The Telegram team affiliated with Smishing Triad incorporates graphic designers, web builders, and income folks, who oversee the enhancement of higher-excellent phishing kits as perfectly as their promoting on dark web cybercrime forums.
Forthcoming WEBINARDetect, Reply, Defend: ITDR and SSPM for Full SaaS Security
Discover how Identity Threat Detection & Reaction (ITDR) identifies and mitigates threats with the aid of SSPM. Discover how to protected your corporate SaaS apps and safeguard your facts, even soon after a breach.
Supercharge Your Capabilities
Many Vietnamese-talking users of the team have been observed collaborating with the principal threat actors in these initiatives, with the latter also collaborating with very similar economically determined teams to scale their functions.
Bundle monitoring textual content frauds notwithstanding, Smishing Triad is also recognized to indulge in Magecart-like attacks that infect on the web purchasing platforms with destructive code injections to intercept customer knowledge.
“Smishing remains a speedily evolving attack vector focusing on buyers throughout the world,” Resecurity explained.
“The risk group’s tactics, tactics, and treatments incorporate two properly-recognized procedures: social engineering and the deployment of a phishing kit via iMessage. Given that users are likely to belief SMS and iMessage interaction channels more than e-mail, this attack has properly compromised quite a few victims.”
Found this posting exciting? Comply with us on Twitter and LinkedIn to go through much more distinctive material we submit.
Some areas of this short article are sourced from:
thehackernews.com

 PoC Exploit Released for Critical VMware Aria’s SSH Auth Bypass Vulnerability
PoC Exploit Released for Critical VMware Aria’s SSH Auth Bypass Vulnerability