In a continuing indicator that risk actors are adapting properly to a submit-macro globe, it has emerged that the use of Microsoft OneNote paperwork to provide malware via phishing attacks is on the rise.
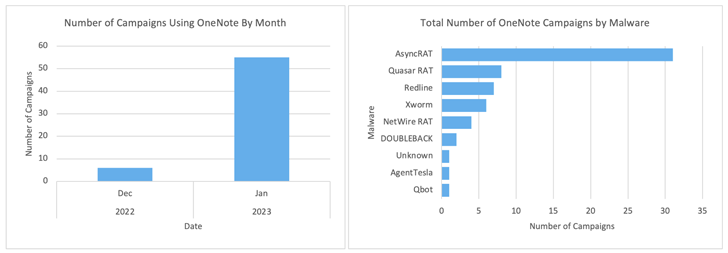
Some of the noteworthy malware households that are remaining distributed utilizing this strategy consist of AsyncRAT, RedLine Stealer, Agent Tesla, DOUBLEBACK, Quasar RAT, XWorm, Qakbot, BATLOADER, and FormBook.
Enterprise organization Proofpoint reported it detected about 50 strategies leveraging OneNote attachments in the month of January 2023 by yourself.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In some cases, the email phishing lures comprise a OneNote file, which, in convert, embeds an HTA file that invokes a PowerShell script to retrieve a malicious binary from a distant server.
Other scenarios entail the execution of a rogue VBScript which is embedded within the OneNote document and concealed at the rear of an impression that appears as a seemingly harmless button. The VBScript, for its section, is created to fall a PowerShell script to operate DOUBLEBACK.
“It is important to take note, an attack is only effective if the receiver engages with the attachment, specially by clicking on the embedded file and disregarding the warning concept exhibited by OneNote,” Proofpoint explained.
The an infection chains are created possible owing to a OneNote element that permits for the execution of pick file forms straight from within just the be aware-using application in what is a scenario of a “payload smuggling” attack.
“Most file forms that can be processed by MSHTA, WSCRIPT, and CSCRIPT can be executed from in just OneNote,” TrustedSec researcher Scott Nusbaum mentioned. “These file sorts incorporate CHM, HTA, JS, WSF, and VBS.”
As remedial actions, Finnish cybersecurity firm WithSecure is recommending people block OneNote mail attachments (.1 and .onepkg data files) and preserve shut tabs on the operations of the OneNote.exe procedure.
The change to OneNote is found as a reaction to Microsoft’s final decision to disallow macros by default in Microsoft Office apps downloaded from the internet final yr, prompting risk actors to experiment with unusual file sorts this sort of as ISO, VHD, SVG, CHM, RAR, HTML, and LNK.
The intention guiding blocking macros is two-fold: To not only lower the attack floor but also enhance the hard work demanded to pull off an attack, even as email carries on to be the top rated shipping and delivery vector for malware.
But these are not the only possibilities that have come to be a well-known way to conceal destructive code. Microsoft Excel insert-in (XLL) files and Publisher macros have also been set to use as an attack pathway to skirt Microsoft’s protections and propagate a remote obtain trojan identified as Ekipa RAT and other backdoors.
The abuse of XLL files has not absent unnoticed by the Windows maker, which is arranging an update to “block XLL increase-ins coming from the internet,” citing an “growing variety of malware attacks in new months.” The possibility is expected to be accessible someday in March 2023.
When attained for remark, Microsoft explained to The Hacker Information that it experienced almost nothing even further to share at this time.
“It can be crystal clear to see how cybercriminals leverage new attack vectors or a lot less-detected implies to compromise consumer products,” Bitdefender’s Adrian Miron said. “These campaigns are probably to proliferate in coming months, with cybercrooks screening out greater or improved angles to compromise victims.”
Found this short article intriguing? Stick to us on Twitter and LinkedIn to read through far more exceptional content material we submit.
Some parts of this post are sourced from:
thehackernews.com

 Windows 10 users locked out of devices by unskippable Microsoft 365 advert
Windows 10 users locked out of devices by unskippable Microsoft 365 advert