The maintainers of the Python Deal Index (PyPI) repository briefly suspended new consumer signal-ups following an influx of malicious jobs uploaded as part of a typosquatting campaign.
It explained “new venture generation and new person registration” was temporarily halted to mitigate what it claimed was a “malware add campaign.” The incident was resolved 10 hours afterwards, on March 28, 2024, at 12:56 p.m. UTC.
Program offer chain security firm Checkmarx explained the unidentified threat actors powering flooding the repository specific builders with typosquatted variations of preferred deals.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This is a multi-phase attack and the malicious payload aimed to steal crypto wallets, sensitive details from browsers (cookies, extensions data, etc.), and numerous qualifications,” researchers Yehuda Gelb, Jossef Harush Kadouri, and Tzachi Zornstain claimed. “In addition, the destructive payload utilized a persistence system to survive reboots.”
The findings had been also corroborated independently by Mend.io, which pointed out that it detected a lot more than 100 destructive offers concentrating on device studying (ML) libraries such as Pytorch, Matplotlib, and Selenium.

The growth arrives as open up-resource repositories are significantly turning into an attack vector for danger actors to infiltrate company environments.
Typosquatting is a perfectly-documented attack method in which adversaries upload packages with names intently resembling their legit counterparts (e.g., Matplotlib vs. Matplotlig or tensorflow vs. tensourflow) in buy to trick unsuspecting people into downloading them.
These misleading variants – totalling more than 500 deals, for every Check out Place – have been found to be uploaded from a one of a kind account starting off March 26, 2024, suggesting that the entire procedure was automatic.
“The decentralized mother nature of the uploads, with every offer attributed to a various person, complicates endeavours to cross-recognize these destructive entries,” the Israeli cybersecurity corporation claimed.
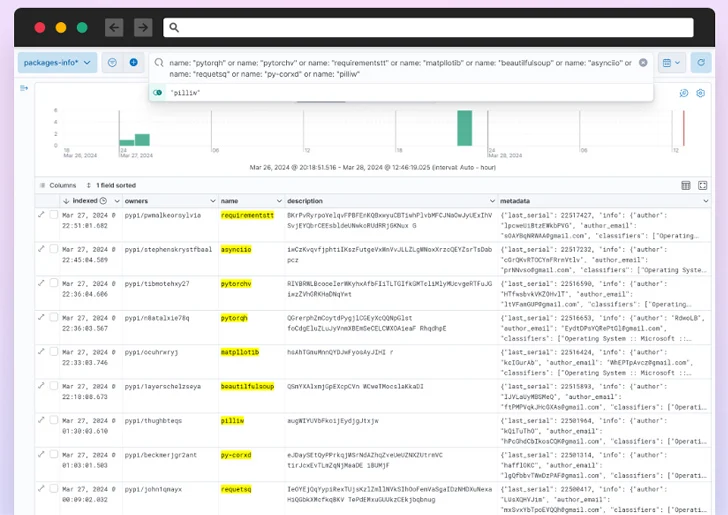
Cybersecurity organization Phylum, which has also been monitoring the same campaign, reported the attackers posted –
- 67 versions of needs
- 38 variations of Matplotlib
- 36 versions of requests
- 35 variants of colorama
- 29 variations of tensorflow
- 28 versions of selenium
- 26 variations of BeautifulSoup
- 26 variants of PyTorch
- 20 variations of pillow
- 15 variants of asyncio
The offers, for their component, look at if the installer’s operating procedure was Windows, and if so, proceed to obtain and execute an obfuscated payload retrieved from an actor-managed domain (“funcaptcha[.]ru”).

The malware features as a stealer, exfiltrating documents, Discord tokens, as very well as info from web browsers and cryptocurrency wallets to the exact same server. It more attempts to obtain a Python script (“hvnc.py”) to the Windows Startup folder for persistence.
The enhancement as soon as again illustrates the escalating risk posed by software program supply chain attacks, creating it important that builders scrutinize each 3rd-party part to assure that it safeguards versus potential threats.
This is not the to start with time PyPI has resorted to these types of a evaluate. In May possibly 2023, it quickly disabled person signal-ups after obtaining that the “quantity of destructive consumers and malicious initiatives getting established on the index in the past week has outpaced our capability to reply to it in a well timed style.”
PyPI suspended new consumer registrations a next-time last calendar year on December 27 for equivalent factors. It was subsequently lifted on January 2, 2024.
Discovered this short article attention-grabbing? Observe us on Twitter and LinkedIn to browse more distinctive content we publish.
Some pieces of this post are sourced from:
thehackernews.com


 Linux Version of DinodasRAT Spotted in Cyber Attacks Across Several Countries
Linux Version of DinodasRAT Spotted in Cyber Attacks Across Several Countries