As many as 8 zero-working day vulnerabilities have been disclosed in Carrier’s LenelS2 HID Mercury entry manage technique that’s employed widely in health care, education and learning, transportation, and government facilities.
“The vulnerabilities uncovered permitted us to show the capacity to remotely unlock and lock doors, subvert alarms and undermine logging and notification devices,” Trellix security researchers Steve Povolny and Sam Quinn reported in a report shared with The Hacker News.
The issues, in a nutshell, could be weaponized by a malicious actor to obtain entire technique regulate, which include the potential to manipulate doorway locks. One particular of the bugs (CVE-2022-31481) contains an unauthenticated distant execution flaw that’s rated 10 out of 10 for severity on the CVSS scoring method.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Other shortcomings could guide to command injection (CVE-2022-31479, CVE-2022-31486), denial-of-services (CVE-2022-31480, CVE-2022-31482), person modification (CVE-2022-31484), and info spoofing (CVE-2022-31485) as effectively as attain arbitrary file write (CVE-2022-31483).
LenelS2 is used in environments to grant bodily accessibility to privileged facilities and combine with additional complicated making automation deployments. The subsequent HID Mercury obtain panels offered by LenelS2 are impacted –
- LNL-X2210
- LNL-X2220
- LNL-X3300
- LNL-X4420
- LNL-4420
- S2-LP-1501
- S2-LP-1502
- S2-LP-2500, and
- S2-LP-4502

Trellix mentioned that by chaining two of the aforementioned weaknesses, it was capable to obtain root-degree privileges on the system remotely and unlock and management the doorways, effectively subverting the method monitoring protections.
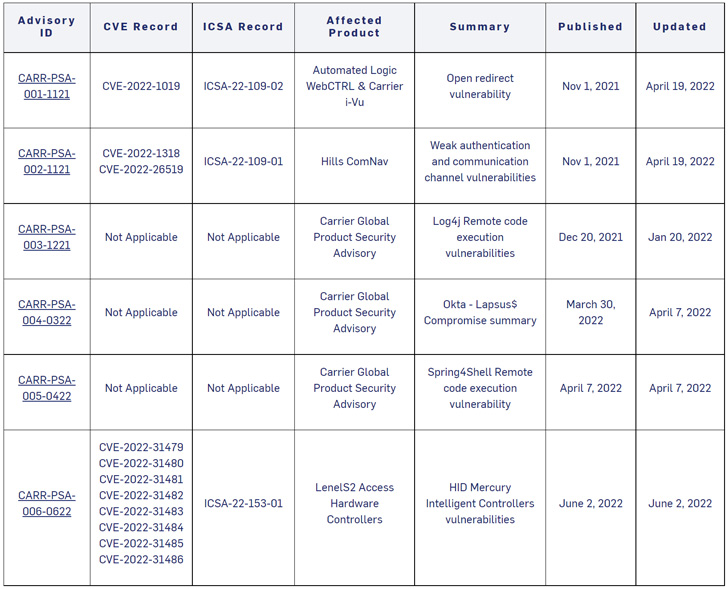
Coinciding with the community disclosure is an industrial regulate devices (ICS) advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), urging people to update the accessibility panels to the latest firmware model (CARR-PSA-006-0622).
“Effective exploitation of these vulnerabilities could let an attacker obtain to the gadget, allowing for checking of all communications sent to and from the product, modification of onboard relays, switching of configuration information, device instability, and a denial-of-provider situation,” the company mentioned in an alert.
Observed this write-up intriguing? Observe THN on Fb, Twitter and LinkedIn to go through additional exclusive content material we write-up.
Some areas of this posting are sourced from:
thehackernews.com

 #RSAC: Plain Language Threat Modeling for DevSecOps
#RSAC: Plain Language Threat Modeling for DevSecOps