A few new security flaws have been disclosed in Microsoft Azure API Management assistance that could be abused by malicious actors to achieve obtain to delicate info or backend solutions.
This consists of two server-aspect ask for forgery (SSRF) flaws and a single occasion of unrestricted file upload functionality in the API Administration developer portal, according to Israeli cloud security business Ermetic.
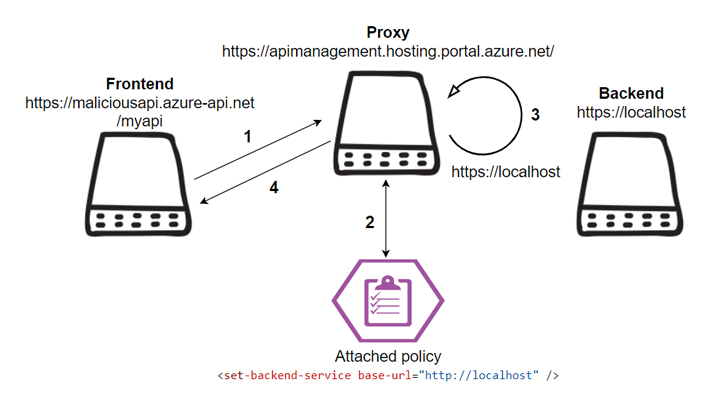
“By abusing the SSRF vulnerabilities, attackers could send out requests from the service’s CORS Proxy and the hosting proxy itself, access inside Azure property, deny provider and bypass web application firewalls,” security researcher Liv Matan stated in a report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“With the file upload route traversal, attackers could upload malicious information to Azure’s hosted internal workload.”
Azure API Management is a multicloud management platform that makes it possible for corporations to securely expose their APIs to exterior and inner customers and help a broad variety of linked experiences.

Of the two SSRF flaws discovered by Ermetic, just one of them is a bypass for a correct put in put by Microsoft to deal with a identical vulnerability described by Orca previously this 12 months. The other vulnerability resides in the API Administration proxy purpose.
Exploitation of SSRF flaws can end result in loss of confidentiality and integrity, allowing a risk actor to read through inner Azure methods and execute unauthorized code.
The path traversal flaw discovered in the developer portal, on the other hand, stems from a lack of validation of the file form and path of the files uploaded.
An authenticated consumer can leverage this loophole to upload malicious data files to the developer portal server and possibly even execute arbitrary code on the fundamental technique.
Future WEBINARLearn to Cease Ransomware with True-Time Defense
Be part of our webinar and find out how to stop ransomware attacks in their tracks with true-time MFA and assistance account defense.
Help you save My Seat!
Following liable disclosure, all the 3 flaws have been patched by Microsoft.
The results appear weeks soon after researchers from Orca specific a “by-design and style flaw” in Microsoft Azure could be exploited by attackers to obtain accessibility to storage accounts, shift laterally in the setting, and even execute remote code.
It also follows the discovery of an additional Azure vulnerability dubbed EmojiDeploy that could allow an attacker to seize management of a targeted application.
Observed this article attention-grabbing? Comply with us on Twitter and LinkedIn to study much more unique material we article.
Some areas of this write-up are sourced from:
thehackernews.com


 Researchers Uncover New Exploit for PaperCut Vulnerability That Can Bypass Detection
Researchers Uncover New Exploit for PaperCut Vulnerability That Can Bypass Detection