The RIG exploit kit (EK) touched an all-time substantial productive exploitation rate of just about 30% in 2022, new conclusions reveal.
“RIG EK is a monetarily-motivated plan that has been energetic considering that 2014,” Swiss cybersecurity business PRODAFT said in an exhaustive report shared with The Hacker Information.
“Even though it has still to substantially alter its exploits in its a lot more modern exercise, the style and version of the malware they distribute regularly improve. The frequency of updating samples ranges from weekly to day by day updates.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Exploit kits are programs applied to distribute malware to significant numbers of victims by using edge of recognized security flaws in frequently-made use of application these as web browsers.
The fact that RIG EK runs as a service model means risk actors can economically compensate the RIG EK administrator for setting up malware of their decision on victim machines. The RIG EK operators largely make use of malvertising to assure a superior infection charge and huge-scale protection.
As a end result, site visitors working with a susceptible edition of a browser to entry an actor-controlled web page or a compromised-but-legitimate website are redirected applying malicious JavaScript code to a proxy server, which, in turn, communicates with an exploit server to produce the appropriate browser exploit.
The exploit server, for its aspect, detects the user’s browser by parsing the Consumer-Agent string and returns the exploit that “matches the pre-defined vulnerable browser variations.”
“The suave layout of the Exploit Package enables it to infect devices with tiny to no conversation from the conclusion user,” the scientists claimed. “In the meantime, its use of proxy servers can make infections more difficult to detect.”
Considering the fact that arriving on the scene in 2014, RIG EK has been noticed offering a wide vary of money trojans, stealers, and ransomware these as AZORult, CryptoBit, Dridex, Raccoon Stealer, and WastedLoader. The operation was dealt a massive blow in 2017 adhering to a coordinated action that dismantled its infrastructure.
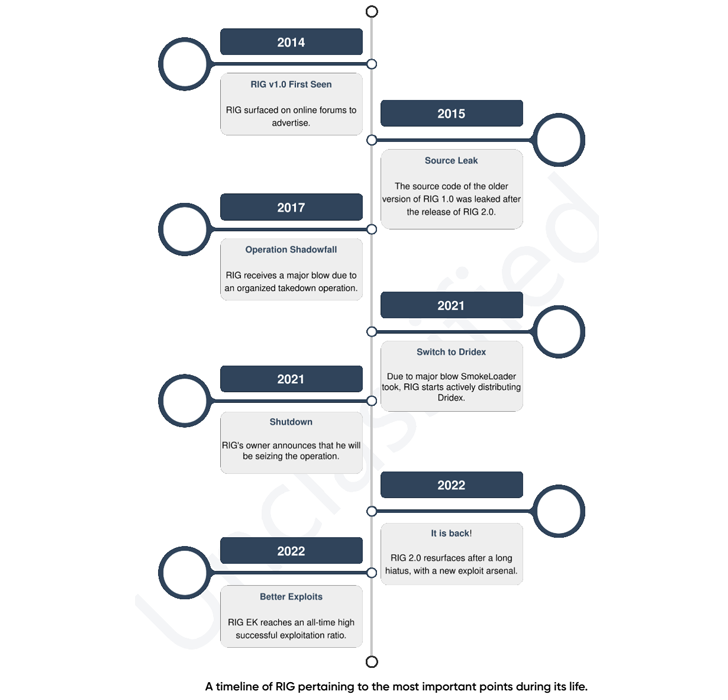
Modern RIG EK strategies have qualified a memory corruption vulnerability impacting Internet Explorer (CVE-2021-26411, CVSS rating: 8.8) to deploy RedLine Stealer.
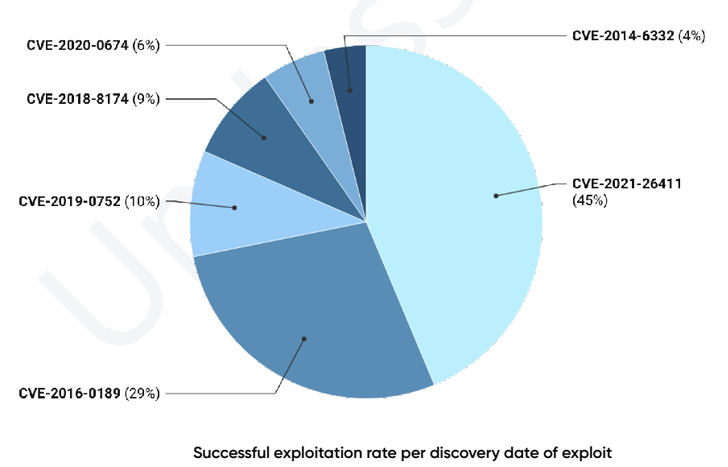
Other browser flaws weaponized by the malware consist of CVE-2013-2551, CVE-2014-6332, CVE-2015-0313, CVE-2015-2419, CVE-2016-0189, CVE-2018-8174, CVE-2019-0752, and CVE-2020-0674.
In accordance to data collected by PRODAFT, 45% of the successful bacterial infections in 2022 leveraged CVE-2021-26411, followed by CVE-2016-0189 (29%), CVE-2019-0752 (10%), CVE-2018-8174 (9%), and CVE-2020-0674 (6%).
Aside from Dridex, Raccoon, and RedLine Stealer, some of the notable malware family members dispersed employing RIG EK are SmokeLoader, PureCrypter, IcedID, ZLoader, TrueBot, Ursnif, and Royal ransomware.
Moreover, the exploit package is stated to have captivated site visitors from 207 nations around the world, reporting a 22% results amount about the past two months alone. The most number of compromises are located in Russia, Egypt, Mexico, Brazil, Saudi Arabia, Turkey, and quite a few countries throughout Europe.
“Curiously ample, the exploit check out prices have been the best on Tuesday, Wednesday and Thursday – with effective bacterial infections getting place on the very same times of the week,” the scientists spelled out.
PRODAFT, which also managed to acquire visibility into the kit’s command panel, said there are about six unique end users, two of whom (admin and vipr) have admin privileges. A person profile with the alias “pit” or “pitty” has subadmin permissions, and 3 other individuals (lyr, ump, and check1) have person privileges.
“admin” is also a dummy user generally reserved for developing other end users. The administration panel, which works with a subscription, is managed applying the “pitty” consumer.
Having said that, an operational security blunder that exposed the git server led PRODAFT to de-anonymize two of the menace actors: a 31-calendar year-outdated Uzbekistan nationwide named Oleg Lukyanov and a Russian who goes by the identify Vladimir Nikonov.
It also assessed with higher self-confidence that the developer of the Dridex malware has a “shut partnership” with the RIG EK’s administrators, owing to the more guide
configuration actions taken to “ensure that the malware was dispersed easily.”
“Over-all, RIG EK runs a pretty fruitful business of exploit-as-a-company, with victims across the globe, a very productive exploit arsenal and several buyers with continuously updating malware,” the scientists said.
Identified this write-up intriguing? Abide by us on Twitter and LinkedIn to examine additional special articles we article.
Some areas of this article are sourced from:
thehackernews.com

 Shocking Findings from the 2023 Third-Party App Access Report
Shocking Findings from the 2023 Third-Party App Access Report