Spoiler Notify: Corporations with 10,000 SaaS people that use M365 and Google Workspace normal around 4,371 supplemental linked applications.
SaaS-to-SaaS (third-party) app installations are growing nonstop at corporations all over the environment. When an personnel needs an more application to boost their efficiency or productiveness, they rarely assume twice just before putting in. Most workers you should not even notice that this SaaS-to-SaaS connectivity, which requires scopes like the means to read through, update, produce, and delete content material, will increase their organization’s attack surface area in a major way.
Third-party app connections usually consider location exterior the perspective of the security staff, are not vetted to recognize the level of risk they pose.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Adaptive Shield’s latest report, Uncovering the Challenges & Realities of 3rd-Party Connected Apps, dives into the facts on this topic. It assessments the normal number of SaaS-to-SaaS apps corporations have, and the amount of risk they current. Listed here are the prime 5 results.
Locating #1: Related Applications Run Deep
The report focuses on Google Workspace and Microsoft 365 (M365), as it paints a obvious picture of the scope of apps that are integrating with the two programs.
On average, a firm with 10,000 SaaS consumers working with M365 has 2,033 apps related to its suite of apps. Firms of that measurement applying Google Workspace have more than a few-situations the amount, averaging 6,710 linked apps.
Even smaller sized companies usually are not immune. The report discovered that firms utilizing M365 normal .2 purposes for each user, whilst those making use of Google Workspace normal .6 applications for every person.
Finding #2: The Much more Workforce, the More Applications
In contrast to most advancement curves, the investigation displays that the selection of apps for every person would not amount off or plateau after reaching a critical mass of customers. Rather, the number of programs proceeds to develop with the variety of customers.
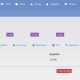
As witnessed in determine 1, businesses applying Google Workspace with 10,000-20,000 staff members normal almost 14,000 unique linked purposes. This ongoing expansion is surprising to security teams, and would make it just about unachievable for them to manually discover and deal with the substantial quantity of purposes.
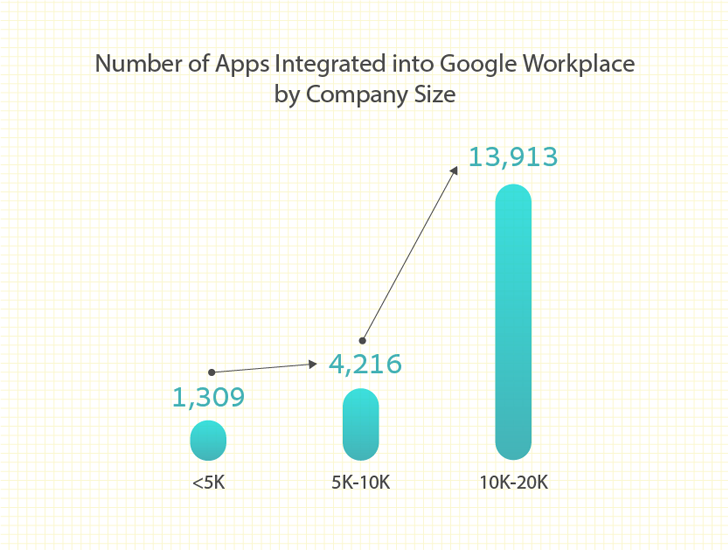 Figure 1: Typical number of applications integrated with Google Workspace by people
Figure 1: Typical number of applications integrated with Google Workspace by people
For the complete 2023 SaaS-to-SaaS Entry Report, click here.
Finding #3: SaaS-to-SaaS App Risk is High
When third-party applications combine with main SaaS applications, they get entry using an OAuth course of action. As aspect of this system, programs request certain scopes. These scopes hand about a good deal of electricity to the applications.
Among high-risk scopes, 15% of M365 programs ask for the authority to delete all information that the user can access. It receives even scarier in Google Workspace programs, wherever 40% of large-risk scopes acquire the potential to delete all Google Push data files.
As shown in this permission tab, the software explicitly requests permission to see, edit, build, and delete all Google Docs files, Google Travel data files, Google Slides displays, and Google Sheets spreadsheets.
For security teams accustomed to controlling the knowledge, permission sets like these are unsettling. Contemplating that lots of apps are created by specific builders who might not have prioritized security in their program progress, these permissions give menace actors with anything they have to have to accessibility and steal or encrypt firm information. Even with out a threat actor, a bug in the software program can have disastrous effects for a company’s facts.
Figure 2: Significant-Risk Authorization Request from a third-party application
Finding #4: Connected Apps Also Have Incredible Breadth
Even though the report deep dives into the massive two SaaS applications, it does also launch investigate into Salesforce (and Slack). Salesforce averages 41 integrated apps for every occasion. The implication of this is noteworthy.
Salesforce is generally utilized by a tiny subset of the organization. In that regard, it is similar to Workday, Github, and ServiceNow, which are made use of by HR, builders, and finance teams. A common enterprise with 10,000 staff members has about 350 SaaS programs in its stack, lots of of which are made use of by smaller sized departments like the apps reviewed right here.
Assuming Salesforce is standard of very similar purposes, people 350 applications integrating with 40 apps just about every provides an more 14,000 third-party apps into the equation.
Locating #5: M365 and Google Workspace Have Comparable Amount of Superior-Risk Applications
A person of the far more attention-grabbing takeaways was the superior volume of superior-risk apps connecting to Microsoft compared to Google Workspace. Applications ask for large-risk permissions from M365 39% of the time Google Workspace apps only request high-risk permissions 11% of the time. In conditions of actual figures, an normal installation in a business with 10,000 SaaS consumers applying M365 will have 813 higher-risk applications, even though Google Workspace will have 738 apps that are thought of substantial-risk.
In all probability, this disparity is brought on because of to the application generation process. Google requires apps requesting higher-risk (it calls them Restrictive) permissions to be reviewed. The critique method is significantly a lot easier for people requesting medium, or delicate, permissions. Microsoft would not label asked for scopes with severity concentrations. This absence of oversight tends to make it a lot simpler for apps that hook up with M365 to request significant-risk scopes.
SaaS Security is Much A lot more Advanced than Most Realize
The overall takeaway from reading through the report is the immense problem of securing SaaS application. It truly is distinct that security teams require visibility into the thousands of apps getting related to the SaaS stack, and make a price tag-profit evaluation for each and every superior-risk related app.
SaaS security alternatives, like Adaptive Defend, supply security groups with the visibility wanted to see linked purposes and their scopes, amongst other critical SaaS security capabilities. Armed with this info, security teams will be in a far better position to harden their applications’ security posture and stop information from falling into the mistaken arms.
Routine a demo to see how several SaaS-to-SaaS apps are related to your SaaS Stack
Discovered this write-up fascinating? Observe us on Twitter and LinkedIn to read through additional special content material we publish.
Some components of this posting are sourced from:
thehackernews.com


 News Corp admits China-linked hackers breached company for two years
News Corp admits China-linked hackers breached company for two years