New study has joined the operations of a politically enthusiastic hacktivist team recognised as Moses Employees to an additional nascent danger actor named Abraham’s Ax that emerged in November 2022.
This is primarily based on “numerous commonalities across the iconography, videography, and leak internet sites made use of by the teams, suggesting they are probable operated by the similar entity,” Secureworks Counter Risk Device (CTU) claimed in a report shared with The Hacker News.
Moses Personnel, tracked by the cybersecurity company underneath the moniker Cobalt Sapling, produced its initially appearance on the threat landscape in September 2021 with the objective of mainly targeting Israeli corporations.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The geopolitical team is considered to be sponsored by the Iranian government and has since been linked to a string of espionage and sabotage attacks that make use of tools like StrifeWater RAT and open supply utilities these types of as DiskCryptor to harvest delicate facts and lock sufferer info on contaminated hosts.
The crew is also recognised to keep a leak site which is utilized to distribute details stolen from their victims and disseminate their messaging, which contains “exposing the crimes of the Zionists in occupied Palestine.”
Now according to Secureworks’ analysis, “the Abraham’s Ax persona is currently being made use of in tandem to attack authorities ministries in Saudi Arabia” and that “this is possible in reaction to Saudi Arabia’s leadership part in improving upon relations in between Israel and Arab nations.”
For its section, Abraham’s Ax promises to be functioning on behalf of the Hezbollah Ummah. Hezbollah, which usually means “Party of Allah” in Arabic, is a Lebanese Shia Islamist political party and militant group that’s backed by Iran.
The placing overlaps in the modus operandi further more elevate the probability that the operators behind Abraham’s Ax are probable leveraging the identical custom malware which functions as a cryptographic wiper to encrypt details without the need of giving a signifies to get better the knowledge in the early levels.
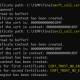
What is much more, both equally actors are united in their motivations in that they run devoid of a economical incentive, with the intrusions using a extra disruptive tone. The connections concerning the two teams is also evidenced by the actuality the WordPress-primarily based leak web sites were being hosted in the very same subnet in the early levels.
“Iran has a record of applying proxy teams and created personas to goal regional and intercontinental adversaries,” Rafe Pilling, Secureworks principal researcher, mentioned in a statement.
“About the very last few of yrs an increasing amount of prison and hacktivist group personas have emerged to concentrate on perceived enemies of Iran though providing plausible deniability to the Government of Iran about affiliation or responsibility for these attacks. This trend is very likely to carry on.”
Located this report exciting? Abide by us on Twitter and LinkedIn to read through more distinctive content we submit.
Some elements of this short article are sourced from:
thehackernews.com

 Is Once-Yearly Pen Testing Enough for Your Organization?
Is Once-Yearly Pen Testing Enough for Your Organization?