A common program provide chain attack has qualified the NPM package deal supervisor at minimum given that December 2021 with rogue modules created to steal information entered in sorts by end users on web-sites that incorporate them.
The coordinated attack, dubbed IconBurst by ReversingLabs, consists of no less than two dozen NPM packages that include things like obfuscated JavaScript, which arrives with destructive code to harvest delicate information from kinds embedded downstream mobile applications and websites.
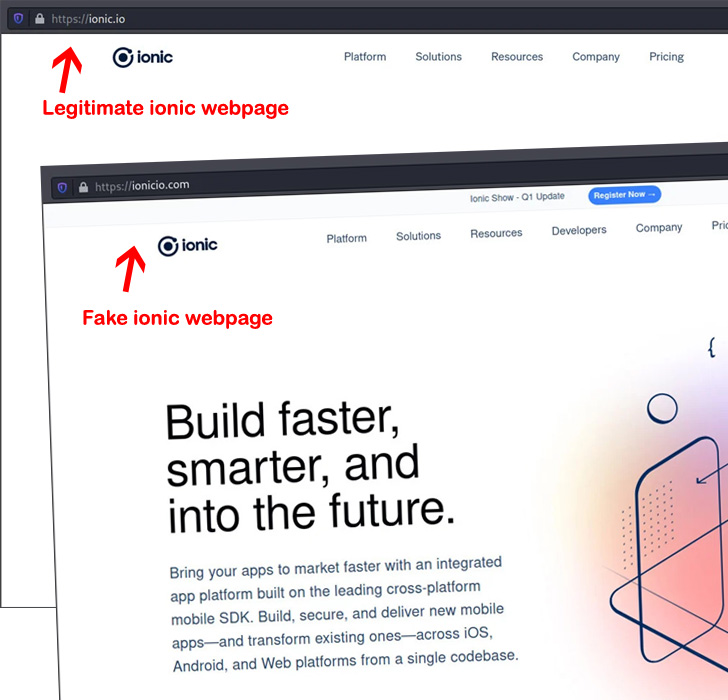
“These clearly malicious attacks relied on typo-squatting, a system in which attackers present up deals by means of community repositories with names that are comparable to — or typical misspellings of — respectable packages,” security researcher Karlo Zanki said in a Tuesday report. “Attackers impersonated higher-visitors NPM modules like umbrellajs and offers printed by ionic.io.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The packages in problem, most of which ended up posted in the previous months, have been collectively downloaded a lot more than 27,000 moments to date. Worse, a vast majority of the modules keep on to be obtainable for down load from the repository.
Some of the most down load malicious modules are outlined under –
- icon-package deal (17,774)
- ionicio (3,724)
- ajax-libs (2,440)
- footericon (1,903)
- umbrellaks (686)
- ajax-library (530)
- pack-icons (468)
- icons-package (380)
- swiper-bundle (185), and
- icons-deals (170)
In just one instance observed by ReversingLabs, information exfiltrated by icon-package deal was routed to a area named ionicio[.]com, a lookalike web page engineered to resemble the authentic ionic[.]io website.

The malware authors behind the campaign additional switched up their tactics in the latest months to assemble information from each form element on the web page, indicating an intense technique to information harvesting.
“The decentralized and modular mother nature of software growth usually means that programs and expert services are only as potent as their the very least secure component,” Zanki noted. “The achievement of this attack […] underscores the freewheeling mother nature of application advancement, and the minimal barriers to destructive or even susceptible code entering sensitive apps and IT environments.”
Discovered this write-up exciting? Stick to THN on Fb, Twitter and LinkedIn to examine more unique information we put up.
Some sections of this posting are sourced from:
thehackernews.com


 Pro-China Group Uses Dragonbridge Campaign to Target Rare Earth Mining Companies
Pro-China Group Uses Dragonbridge Campaign to Target Rare Earth Mining Companies