More than a dozen security flaws have been disclosed in E11, a smart intercom item designed by Chinese company Akuvox.
“The vulnerabilities could let attackers to execute code remotely in buy to activate and handle the device’s camera and microphone, steal video and pictures, or obtain a network foothold,” Claroty security researcher Vera Mens claimed in a complex write-up.
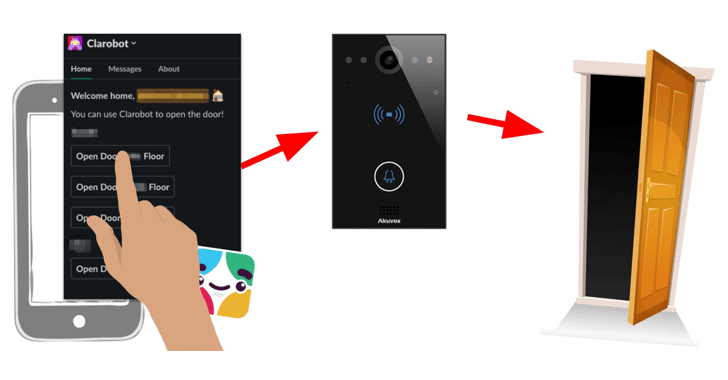
Akuvox E11 is explained by the corporation on its website as a “SIP [Session Initiation Protocol] video clip doorphone specifically developed for villas, houses, and residences.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The item listing, nevertheless, has been taken down from the web site, displaying an mistake message: “Web page does not exist.” A snapshot captured by Google demonstrates that the web page was dwell as lately as March 12, 2023, 05:59:51 GMT.
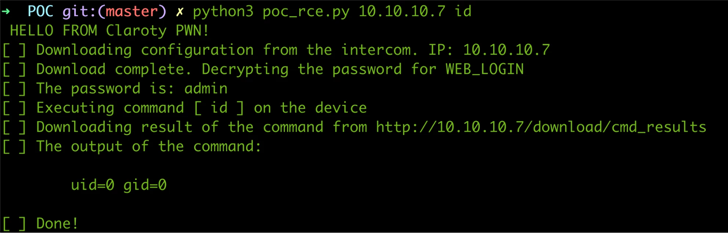
The attacks can manifest both as a result of distant code execution within the community location network (LAN) or remote activation of the E11’s camera and microphone, letting the adversary to obtain and exfiltrate multimedia recordings.
A 3rd attack vector requires edge of an external, insecure file transfer protocol (FTP) server to down load saved illustrations or photos and facts.
The most serious of the issues are as follows –
- CVE-2023-0344 (CVSS score: 9.1) – Akuvox E11 appears to be utilizing a tailor made edition of dropbear SSH server. This server makes it possible for an insecure solution that by default is not in the formal dropbear SSH server.
- CVE-2023-0345 (CVSS score: 9.8) – The Akuvox E11 protected shell (SSH) server is enabled by default and can be accessed by the root user. This password cannot be transformed by the user.
- CVE-2023-0352 (CVSS rating: 9.1) – The Akuvox E11 password recovery webpage can be accessed with out authentication, and an attacker could down load the machine key file. An attacker could then use this web site to reset the password back again to the default.
- CVE-2023-0354 (CVSS score: 9.1) – The Akuvox E11 web server can be accessed without having any person authentication, and this could enable an attacker to entry delicate information and facts, as perfectly as create and download packet captures with known default URLs.
A the greater part of the 13 security issues continue to be unpatched to date, with the industrial and IoT security organization noting that Akuvox has given that tackled the FTP server permissions issue by disabling the “the skill to record its material so malicious actors could not enumerate information any longer.”
WEBINARDiscover the Hidden Risks of Third-Party SaaS Apps
Are you knowledgeable of the challenges involved with third-party app access to your firm’s SaaS apps? Join our webinar to learn about the forms of permissions currently being granted and how to lessen risk.
RESERVE YOUR SEAT
The findings have also prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to launch an Industrial Manage Units (ICS) advisory of its individual very last 7 days.
“Prosperous exploitation of these vulnerabilities could lead to reduction of sensitive data, unauthorized entry, and grant comprehensive administrative manage to an attacker,” the company cautioned.
In the absence of patches, organizations applying the doorphone are encouraged to disconnect it from the internet till the vulnerabilities are preset to mitigate possible remote attacks.
It’s also advised to alter the default password made use of to secure the web interface and “segment and isolate the Akuvox gadget from the rest of the company network” to stop lateral motion attacks.
The enhancement will come as Wago released patches for many of its programmable logic controllers (PLCs) to handle 4 vulnerabilities (CVE-2022-45137, CVE-2022-45138, CVE-2022-45139, and CVE-2022-45140) two of which could be exploited to obtain comprehensive technique compromise.
Located this post attention-grabbing? Adhere to us on Twitter and LinkedIn to read through much more exclusive material we submit.
Some components of this article are sourced from:
thehackernews.com

 KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets
KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets