The Dark Pink sophisticated persistent threat (APT) actor has been linked to a new established of attacks concentrating on govt and army entities in Southeast Asian international locations with a malware known as KamiKakaBot.
Dark Pink, also referred to as Saaiwc, was initial profiled by Group-IB before this year, describing its use of tailor made resources these as TelePowerBot and KamiKakaBot to run arbitrary instructions and exfiltrate sensitive facts.
The threat actor is suspected to be of Asia-Pacific origin and has been active due to the fact at least mid-2021, with an improved tempo noticed in 2022.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The latest attacks, which took put in February 2023, ended up almost identical to previous attacks,” Dutch cybersecurity corporation EclecticIQ disclosed in a new report published past week.
“The key variance in the February campaign is that the malware’s obfuscation regimen has enhanced to far better evade anti-malware steps.”
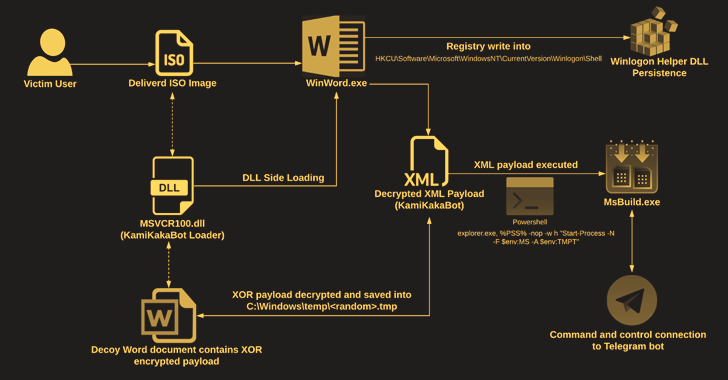
The attacks perform out in the sort of social engineering lures that consist of ISO impression file attachments in email messages to deliver the malware.
The ISO picture includes an executable (Winword.exe), a loader (MSVCR100.dll), and a decoy Microsoft Phrase doc, the latter of which will come embedded with the KamiKakaBot payload.
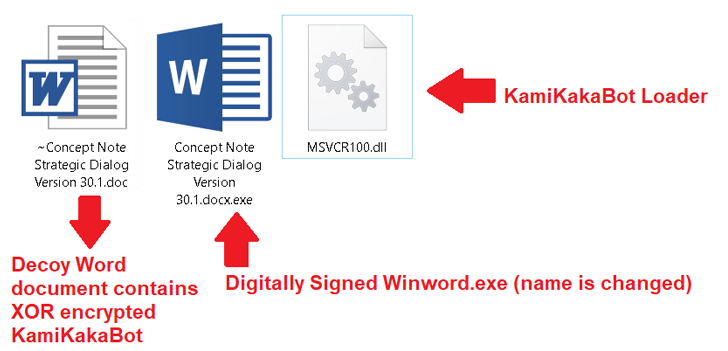
The loader, for its aspect, is built to load the KamiKakaBot malware by leveraging the DLL aspect-loading technique to evade security protections and load it into the memory of the Winword.exe binary.
KamiKakaBot is mostly engineered to steal details stored in web browsers and execute distant code making use of Command Prompt (cmd.exe), while also embracing evasion tactics to mix in with sufferer environments and hinder detection.
WEBINARDiscover the Concealed Hazards of 3rd-Party SaaS Applications
Are you conscious of the challenges connected with 3rd-party application access to your firm’s SaaS apps? Join our webinar to study about the kinds of permissions being granted and how to limit risk.
RESERVE YOUR SEAT
Persistence on the compromised host is realized by abusing the Winlogon Helper library to make destructive Windows Registry crucial modifications. The gathered information is subsequently exfiltrated to a Telegram bot as a ZIP archive.
“The use of legit web services as a command-and-manage (C2) server, these as Telegram, stays the range a single option for unique risk actors, ranging from typical cyber criminals to state-of-the-art persistent risk actors,” the Amsterdam-dependent enterprise explained.
“The Dark Pink APT team is extremely probably a cyber espionage-inspired menace actor that especially exploits relations concerning ASEAN and European nations to build phishing lures during the February 2023 campaign.”
Found this post attention-grabbing? Adhere to us on Twitter and LinkedIn to go through additional unique material we write-up.
Some pieces of this post are sourced from:
thehackernews.com

 BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads
BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads