The sophisticated persistent danger (APT) actor acknowledged as SideWinder has been accused of deploying a backdoor in attacks directed from Pakistan govt businesses as section of a campaign that commenced in late November 2022.
“In this campaign, the SideWinder state-of-the-art persistent danger (APT) group used a server-centered polymorphism system to provide the subsequent phase payload,” the BlackBerry Study and Intelligence Group claimed in a complex report revealed Monday.
A different campaign learned by the Canadian cybersecurity organization in early March 2023 exhibits that Turkey has also landed in the crosshairs of the menace actor’s collection priorities.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
SideWinder has been on the radar considering that at the very least 2012 and it truly is generally regarded to focus on different Southeast Asian entities located in Pakistan, Afghanistan, Bhutan, China, Myanmar, Nepal, and Sri Lanka.
Suspected to be an Indian state-sponsored team, SideWinder is also tracked below the monikers APT-C-17, APT-Q-39, Hardcore Nationalist (HN2), Rattlesnake, Razor Tiger, and T-APT4.

Usual attack sequences mounted by the actor entail working with carefully crafted email lures and DLL facet-loading procedures to fly under the radar and deploy malware capable of granting the actors distant access to the focused systems.
Around the earlier calendar year, SideWinder has been joined to a cyber attack aimed at Pakistan Navy War College or university (PNWC) as very well as an Android malware campaign that leveraged rogue phone cleaner and VPN applications uploaded to the Google Engage in Shop to harvest delicate information.
The most recent infection chain documented by BlackBerry mirrors conclusions from Chinese cybersecurity firm QiAnXin in December 2022 detailing the use of PNWC entice paperwork to fall a lightweight .NET-dependent backdoor (App.dll) that’s capable of retrieving and executing following-stage malware from a distant server.
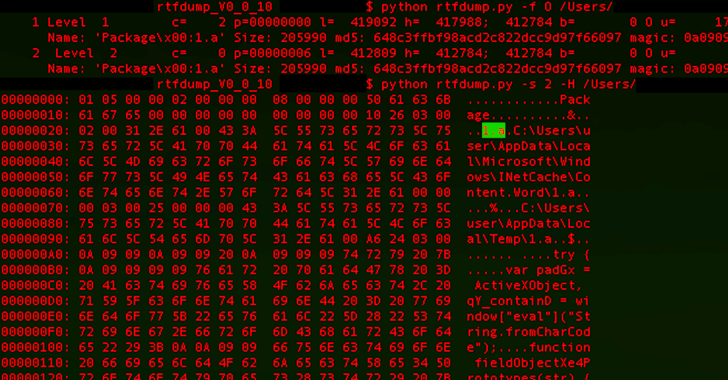
What makes the campaign also stand out is the risk actor’s use of server-based polymorphism as a way to probably sidestep regular signature-centered antivirus (AV) detection and distribute more payloads by responding with two diverse versions of an intermediate RTF file.
Specifically, the PNWC document employs a system recognized as distant template injection to fetch the RTF file these types of that it harbors the malicious code only if the request originates from a person in the Pakistan IP deal with vary.
“It is vital to notice that in both of those instances, only the title of the file ‘file.rtf’ and the file variety are the very same however, the contents, file size and the file hash are various,” BlackBerry explained.
Approaching WEBINARLearn to Halt Ransomware with Actual-Time Safety
Join our webinar and learn how to prevent ransomware attacks in their tracks with actual-time MFA and services account safety.
Help you save My Seat!
“If the user is not in the Pakistani IP variety, the server returns an 8-byte RTF file (file.rtf) that has a one string: rtf1 . Nonetheless, if the person is in just the Pakistani IP range, the server then returns the RTF payload, which differs between 406 KB – 414 KB in dimension.”
The disclosure arrives soon immediately after Fortinet and Staff Cymru disclosed information of attacks perpetrated by a Pakistan-based mostly threat actor known as SideCopy in opposition to Indian protection and armed forces targets.
“The most recent SideWinder marketing campaign targeting Turkey overlaps with the most recent developments in geopolitics specially, in Turkey’s help of Pakistan and the ensuing response from India,” BlackBerry claimed.
Uncovered this short article attention-grabbing? Abide by us on Twitter and LinkedIn to browse extra exceptional articles we put up.
Some components of this posting are sourced from:
thehackernews.com

 EU’s Client-Side Scanning Plans Could be Unlawful
EU’s Client-Side Scanning Plans Could be Unlawful