Risk hunters have unmasked the most recent tricks adopted by a malware strain called GuLoader in an work to make investigation a lot more difficult.
“Whilst GuLoader’s main performance hasn’t changed considerably over the earlier number of many years, these continual updates in their obfuscation strategies make examining GuLoader a time-consuming and useful resource-intense procedure,” Elastic Security Labs researcher Daniel Stepanic mentioned in a report printed this 7 days.
To start with noticed in late 2019, GuLoader (aka CloudEyE) is an superior shellcode-dependent malware downloader which is employed to distribute a extensive range of payloads, such as info stealers, when incorporating a bevy of sophisticated anti-evaluation tactics to dodge conventional security answers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A continual stream of open-source reporting into the malware in new months has exposed the danger actors behind it have continued to strengthen its skill to bypass present or new security capabilities alongside other implemented options.
GuLoader is generally unfold as a result of phishing strategies, the place victims are tricked into downloading and installing the malware via emails bearing ZIP archives or one-way links that contains a Visible Basic Script (VBScript) file.
Impending WEBINAR Cracking the Code: Master How Cyber Attackers Exploit Human Psychology
Ever puzzled why social engineering is so productive? Dive deep into the psychology of cyber attackers in our approaching webinar.
Be a part of Now
Israeli cybersecurity organization Test Stage, in September 2023, revealed that “GuLoader is now marketed less than a new name on the very same system as Remcos and is implicitly promoted as a crypter that will make its payload fully undetectable by antiviruses.”
Just one of the modern improvements to the malware is an advancement of an anti-examination method initial disclosed by CrowdStroke in December 2022 and which is centered all-around its Vectored Exception Managing (VEH) functionality.
It is worthy of pointing out that the system was beforehand thorough by each McAfee Labs and Examine Level in May possibly 2023, with the former stating that “GuLoader employs the VEH primarily for obfuscating the execution circulation and to gradual down the examination.”
The process “is made up of breaking the ordinary movement of code execution by deliberately throwing a big variety of exceptions and dealing with them in a vector exception handler that transfers manage to a dynamically calculated handle,” Check out Level stated.
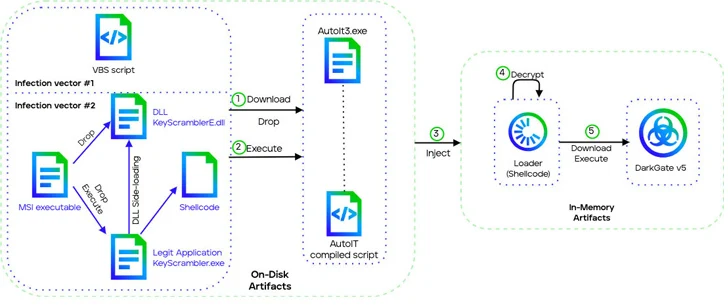
GuLoader is significantly from the only malware household to have acquired constant updates. Yet another notable example is DarkGate, a remote entry trojan (RAT) that allows attackers to completely compromise victim devices.
Bought as malware-as-a-provider (MaaS) by an actor recognised as RastaFarEye on underground boards for a every month cost of $15,000, the malware works by using phishing e-mails containing hyperlinks to distribute the initial infection vector: a VBScript or Microsoft Program Installer (MSI) file.
Trellix, which analyzed the hottest edition of DarkGate (5..19), claimed it “introduces a new execution chain making use of DLL side-loading and enhanced shellcodes and loaders.” Further more, it comes with a finish rework of the RDP password theft characteristic.
“The threat actor has been actively checking threat reports to carry out swift modifications hence evading detections,” security scientists Ernesto Fernández Provecho, Pham Duy Phuc, Ciana Driscoll, and Vinoo Thomas mentioned.

“Its adaptability, the velocity with which it iterates, and the depth of its evasion methods attest to the sophistication of fashionable malware threats.”
The improvement will come as remote access trojans like Agent Tesla and AsyncRAT have been observed getting propagated making use of novel email-centered an infection chains that leverage steganography and unusual file types in an endeavor to bypass antivirus detection actions.
It also follows a report from the HUMAN Satori Danger Intelligence Group about how an updated model of a malware obfuscation motor named ScrubCrypt (aka BatCloak) is remaining employed to produce the RedLine stealer malware.
“The new ScrubCrypt establish was bought to threat actors on a compact handful of dark web marketplaces, which includes Nulled Forum, Cracked Discussion board, and Hack Message boards,” the corporation claimed.
Discovered this write-up fascinating? Stick to us on Twitter and LinkedIn to go through far more exclusive articles we article.
Some elements of this write-up are sourced from:
thehackernews.com


 New 5G Modems Flaws Affect iOS Devices and Android Models from Major Brands
New 5G Modems Flaws Affect iOS Devices and Android Models from Major Brands