A assortment of security flaws in the firmware implementation of 5G cellular network modems from important chipset sellers this kind of as MediaTek and Qualcomm affect USB and IoT modems as effectively as hundreds of smartphone products working Android and iOS.
Of the 14 flaws – collectively named 5Ghoul (a blend of “5G” and “Ghoul”) – 10 have an effect on 5G modems from the two businesses, out of which three have been categorised as substantial-severity vulnerabilities.
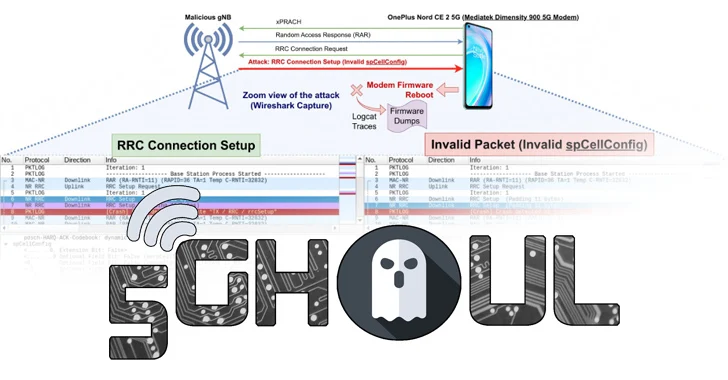
“5Ghoul vulnerabilities may perhaps be exploited to repeatedly start attacks to fall the connections, freeze the connection that involve handbook reboot or downgrade the 5G connectivity to 4G,” the scientists explained in a examine published today.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
As a lot of as 714 smartphones from 24 brand names are impacted, including people from Vivo, Xiaomi, OPPO, Samsung, Honor, Motorola, realme, OnePlus, Huawei, ZTE, Asus, Sony, Meizu, Nokia, Apple, and Google.
Forthcoming WEBINAR Cracking the Code: Study How Cyber Attackers Exploit Human Psychology
At any time questioned why social engineering is so effective? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Join Now
The vulnerabilities had been disclosed by a workforce of scientists from the ASSET (Automatic Systems SEcuriTy) Study Group at the Singapore University of Technology and Layout (SUTD), who also previously disclosed BrakTooth in September 2021 and SweynTooth in February 2020.
The attacks, in a nutshell, endeavor to deceive a smartphone or a 5G-enabled gadget to connect a rogue foundation station (gNB), resulting in unintended penalties.
“The attacker does not have to have to be conscious of any top secret information and facts of the target UE e.g., UE’s SIM card specifics, to comprehensive the NAS network registration,” the researchers stated. “The attacker only requirements to impersonate the authentic gNB employing the acknowledged Cell Tower connection parameters.”

A threat actor can achieve this by applying apps like Mobile-Pro to establish the Relative Signal Power Indicator (RSSI) readings and trick the user machines to link to the adversarial station (i.e., a software package-outlined radio) as very well as an cheap mini Laptop.
Notable amongst the 14 flaws is CVE-2023-33042, which can permit an attacker in just radio variety to trigger a 5G connectivity downgrade or a denial-of-provider (DoS) within Qualcomm’s X55/X60 modem firmware by sending malformed Radio Source Management (RRC) frame to the focus on 5G gadget from a close by malicious gNB.

Productive exploitation of the other DoS vulnerabilities could have to have a guide reboot of the device to restore 5G connectivity.
Patches have been introduced by both MediaTek and Qualcomm for 12 of the 14 flaws. Facts of the two other vulnerabilities have been withheld thanks to confidentiality reasons and are envisioned to be disclosed in the foreseeable future.
“Obtaining issues in the implementation of the 5G modem vendor greatly impacts merchandise distributors downstream,” the researchers mentioned, adding that “it can usually just take six or additional months for 5G security patches to lastly reach the conclude-person via an OTA update.”
“This is since the application dependency of item suppliers on the Modem / Chipset Vendor provides complexity and as a result delays to the system of generating and distributing patches to the stop-person.”
Discovered this short article interesting? Observe us on Twitter and LinkedIn to read more exclusive information we publish.
Some elements of this short article are sourced from:
thehackernews.com

 N. Korean Kimsuky Targeting South Korean Research Institutes with Backdoor Attacks
N. Korean Kimsuky Targeting South Korean Research Institutes with Backdoor Attacks