Cybersecurity researchers have taken the wraps off a formerly undocumented ransomware pressure named Rorschach that is the two innovative and fast.
“What tends to make Rorschach stand out from other ransomware strains is its significant stage of customization and its technically distinctive attributes that have not been observed right before in ransomware,” Examine Level Analysis said in a new report. “In fact, Rorschach is a single of the fastest ransomware strains ever observed, in conditions of the speed of its encryption.”
The cybersecurity firm claimed it noticed the ransomware deployed against an unnamed U.S.-primarily based organization, introducing it uncovered no branding or overlaps that link it to any previously identified ransomware actors.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Having said that, further evaluation of Rorschach’s source code reveals similarities to Babuk ransomware, which experienced a leak in September 2021, and LockBit 2.. On prime of that, the ransom notes despatched out to the victims surface to be inspired by that of Yanluowang and DarkSide.
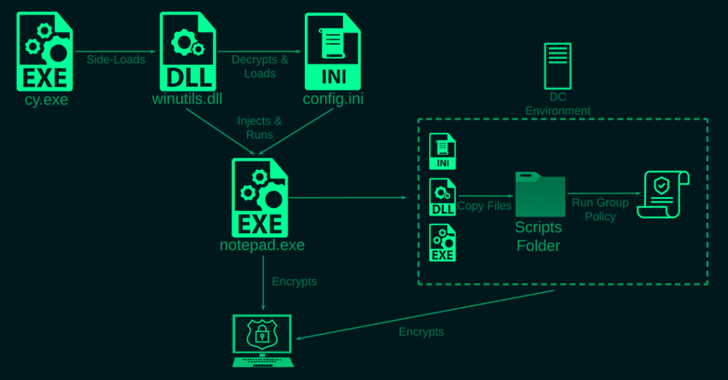
The most considerable facet of the intrusion is the use of a approach identified as DLL side-loading to load the ransomware payload, a process not noticed in such attacks. The enhancement marks a new sophistication in the techniques adopted by fiscally motivated teams to sidestep detection.
Exclusively, the ransomware is explained to have been deployed by abusing Palo Alto Network’s Cortex XDR Dump Service Resource (cy.exe) to sideload a library named “winutils.dll.”
A further special attribute is its highly customizable mother nature and the use of direct syscalls to manipulate data files and bypass defense mechanisms.
Rorschach ransomware is also tasked with terminating a predefined list of services, deleting shadow volumes and backups, clearing Windows occasions logs to erase forensic path, disabling the Windows firewall, and even deleting itself following finishing its steps.
Inside propagation is accomplished by compromising the domain controller and generating a team policy, in accordance to Test Position and South Korean cybersecurity corporation AhnLab, which erroneously attributed the infection chain to DarkSide earlier this February.
The ransomware, like other malware strains observed in the wild, skips devices that are situated in the Commonwealth of Unbiased States (CIS) countries by examining the procedure language.
THN WEBINARBecome an Incident Reaction Pro!
Unlock the secrets to bulletproof incident response – Master the 6-Period course of action with Asaf Perlman, Cynet’s IR Leader!
Will not Skip Out – Save Your Seat!
“The Rorschach ransomware employs a extremely effective and quick hybrid-cryptography scheme, which blends the curve25519 and eSTREAM cipher hc-128 algorithms for encryption reasons,” researchers Jiri Vinopal, Dennis Yarizadeh, and Gil Gekker spelled out.
This process is designed to only encrypt a particular part of the original file content instead of the overall file, and employs further compiler optimization strategies that make it a “pace demon.”
In five different exams carried out by Check Stage in a managed surroundings, 220,000 data files were being encrypted employing Rorschach inside of four minutes and 30 seconds on average. LockBit 3., on the other hand, took around 7 minutes.
“Its builders implemented new anti-investigation and protection evasion approaches to stay away from detection and make it extra tough for security application and researchers to review and mitigate its effects,” the scientists said.
“Additionally, Rorschach seems to have taken some of the ‘best’ functions from some of the foremost ransomwares leaked on-line, and integrated them all with each other. In addition to Rorschach’s self-propagating abilities, this raises the bar for ransom attacks.”
The findings occur as the Fortinet FortiGuard Labs detailed two rising ransomware households referred to as PayMe100USD, a Python-primarily based file-locking malware, and Dark Electric power, which is published in the Nim programming language.
Located this report appealing? Observe us on Twitter and LinkedIn to go through far more special content material we write-up.
Some pieces of this write-up are sourced from:
thehackernews.com

 New Rilide Malware Targeting Chromium-Based Browsers to Steal Cryptocurrency
New Rilide Malware Targeting Chromium-Based Browsers to Steal Cryptocurrency