The risk actors powering RTM Locker have created a ransomware pressure that is capable of concentrating on Linux devices, marking the group’s to start with foray into the open source running technique.
“Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be encouraged by Babuk ransomware’s leaked source code,” Uptycs reported in a new report revealed Wednesday. “It takes advantage of a blend of ECDH on Curve25519 (asymmetric encryption) and Chacha20 (symmetric encryption) to encrypt data files.”
RTM Locker was first documented by Trellix earlier this thirty day period, describing the adversary as a private ransomware-as-a-service (RaaS) provider. It has its roots in a cybercrime group referred to as Go through The Manual (RTM) that’s known to be active since at the very least 2015.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The team is notable for intentionally averting significant-profile targets these kinds of as critical infrastructure, regulation enforcement, and hospitals so as to draw as small notice as attainable. It also leverages affiliates to ransom victims, in addition to leaking stolen knowledge really should they refuse to pay up.
The Linux taste is specifically geared to one out ESXi hosts by terminating all virtual devices running on a compromised host prior to commencing the encryption process. The specific first infector employed to deliver the ransomware is at the moment mysterious.
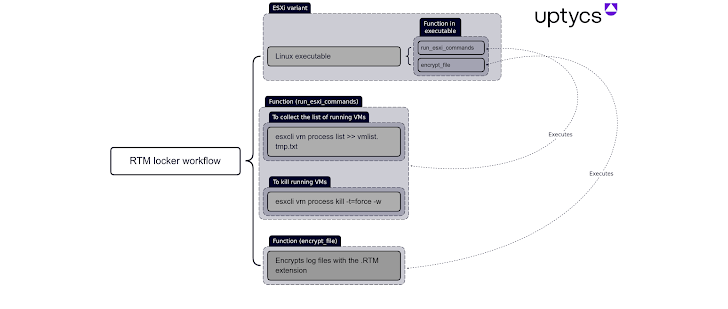
“It is statically compiled and stripped, building reverse engineering a lot more difficult and allowing the binary to operate on extra devices,” Uptycs spelled out. “The encryption operate also makes use of pthreads (aka POSIX threads) to velocity up execution.”
Future WEBINARZero Trust + Deception: Find out How to Outsmart Attackers!
Find out how Deception can detect superior threats, stop lateral motion, and enhance your Zero Believe in tactic. Join our insightful webinar!
Help you save My Seat!
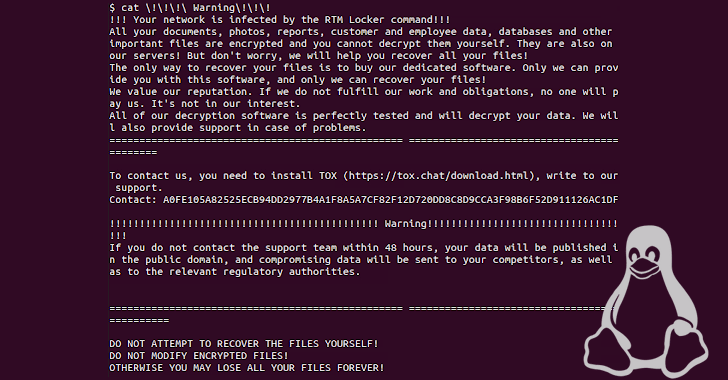
Subsequent profitable encryption, victims are urged to call the assistance workforce within just 48 several hours by using Tox or risk getting their information printed. Decrypting a file locked with RTM Locker requires the public key appended to the end of the encrypted file and the attacker’s non-public essential.
The growth arrives as Microsoft disclosed that vulnerable PaperCut servers are being actively specific by menace actors to deploy Cl0p and LockBit ransomware.
Uncovered this write-up appealing? Comply with us on Twitter and LinkedIn to browse far more distinctive content we article.
Some parts of this report are sourced from:
thehackernews.com

 Microsoft Blames Clop Affiliate for PaperCut Attacks
Microsoft Blames Clop Affiliate for PaperCut Attacks