The Russian nation-point out threat actor acknowledged as APT28 has been observed building use of lures associated to the ongoing Israel-Hamas war to facilitate the shipping of a tailor made backdoor named HeadLace.
IBM X-Power is tracking the adversary under the name ITG05, which is also recognised as BlueDelta, Extravagant Bear, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Sednit, Sofacy, and TA422.
“The freshly learned campaign is directed towards targets based in at least 13 nations around the globe and leverages authentic paperwork produced by educational, finance and diplomatic centers,” security researchers Golo Mühr, Claire Zaboeva, and Joe Fasulo claimed.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“ITG05’s infrastructure guarantees only targets from a single precise state can get the malware, indicating the very targeted character of the marketing campaign.”
Future WEBINAR Cracking the Code: Master How Cyber Attackers Exploit Human Psychology
Ever puzzled why social engineering is so effective? Dive deep into the psychology of cyber attackers in our forthcoming webinar.
Be part of Now
Targets of the campaign involve Hungary, Türkiye, Australia, Poland, Belgium, Ukraine, Germany, Azerbaijan, Saudi Arabia, Kazakhstan, Italy, Latvia, and Romania.
The campaign includes the use of decoys that are made to principally one out European entities with a “immediate affect on the allocation of humanitarian support,” leveraging documents associated with the United Nations, the Bank of Israel, the U.S. Congressional Investigate Services, the European Parliament, a Ukrainian believe tank, and an Azerbaijan-Belarus Intergovernmental Commission.
Some of the attacks have been uncovered to make use of RAR archives exploiting the WinRAR flaw called CVE-2023-38831 to propagate HeadLace, a backdoor that was very first disclosed by the personal computer Emergency Reaction Staff of Ukraine (CERT-UA) in attacks aimed at critical infrastructure in the country.
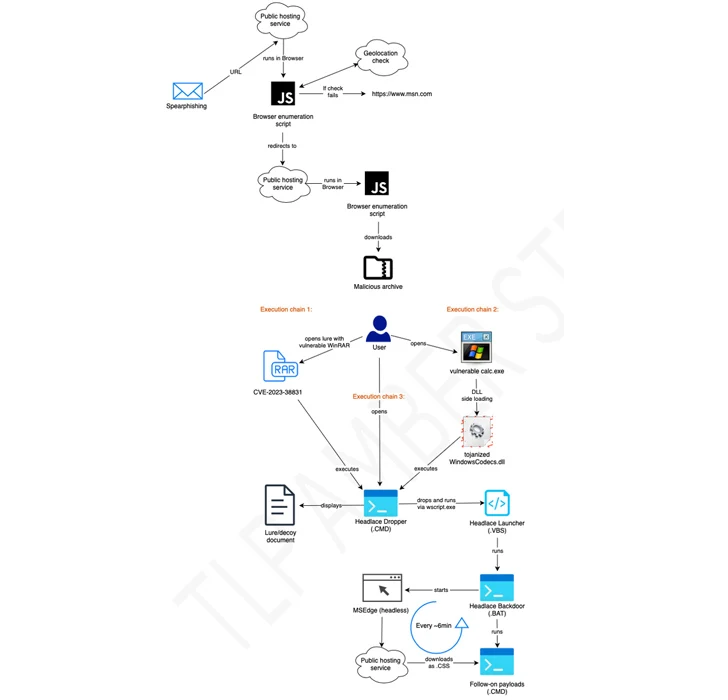
It’s worthy of noting that Zscaler revealed a identical campaign named Steal-It in late September 2023 that enticed targets with grownup-themed content material to trick them into parting with sensitive details.
The disclosure will come a week immediately after Microsoft, Palo Alto Networks Device 42, and Proofpoint thorough the risk actor’s exploitation of a critical security flaw of Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) to acquire unauthorized access to victims’ accounts within Exchange servers.

The reliance on official files as lures, thus, marks a deviation from earlier noticed exercise, “indicative of ITG05’s improved emphasis on a special target viewers whose passions would prompt interaction with material impacting rising plan development.”
“It is hugely probable the compromise of any echelon of worldwide foreign policy centers may perhaps support officials’ passions with advanced perception into critical dynamics bordering the Intercontinental Community’s (IC) tactic to competing priorities for security and humanitarian help,” the scientists said.
The development comes as CERT-UA linked the risk actor known as UAC-0050 to a huge email-dependent phishing attack versus Ukraine and Poland utilizing Remcos RAT and Meduza Stealer.
Observed this article attention-grabbing? Stick to us on Twitter and LinkedIn to browse much more unique information we put up.
Some areas of this article are sourced from:
thehackernews.com


 Non-Human Access is the Path of Least Resistance: A 2023 Recap
Non-Human Access is the Path of Least Resistance: A 2023 Recap