The Russia-connected Gamaredon team tried to unsuccessfully split into a large petroleum refining corporation in just a NATO member condition earlier this calendar year amid the ongoing Russo-Ukrainian war.
The attack, which took put on August 30, 2022, is just one particular of various attacks orchestrated by the highly developed persistent risk (APT) that is attributed to Russia’s Federal Security Provider (FSB).
Gamaredon, also identified by the monikers Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and Winterflounder, has a heritage of mainly going soon after Ukrainian entities and, to a lesser extent, NATO allies to harvest delicate facts.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“As the conflict has continued on the floor and in cyberspace, Trident Ursa has been running as a dedicated obtain creator and intelligence gatherer,” Palo Alto Networks Device 42 said in a report shared with The Hacker News. “Trident Ursa continues to be a person of the most pervasive, intrusive, constantly lively and concentrated APTs focusing on Ukraine.”

Device 42’s ongoing monitoring of the group’s activities has uncovered far more than 500 new domains, 200 malware samples, and several shifts in its strategies over the past 10 months in response to ever-switching and expanding priorities.
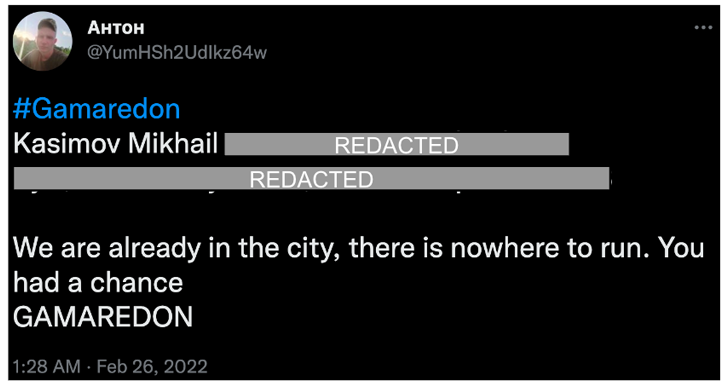
Outside of cyberattacks, the larger security community is claimed to have been at the getting end of threatening tweets from a purported Gamaredon associate, highlighting the intimidation approaches adopted by the adversary.
Other noteworthy strategies consist of the use of Telegram webpages to appear up command-and-handle (C2) servers and quickly flux DNS to rotate via several IP addresses in a limited span of time to make IP-based mostly denylisting and takedown attempts more difficult.
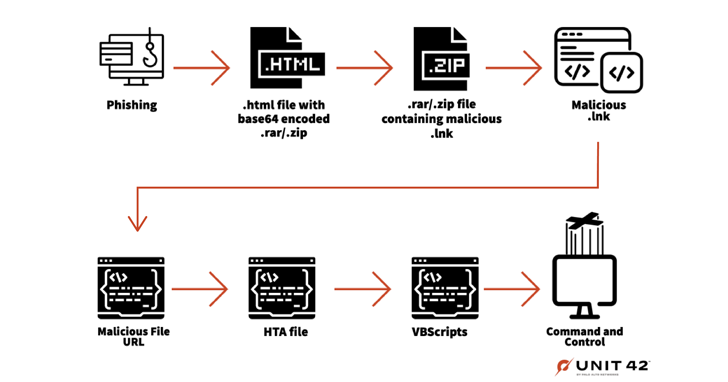
The attacks them selves entail the shipping of weaponized attachments embedded in spear-phishing e-mail to deploy a VBScript backdoor on the compromised host which is capable of creating persistence and executing added VBScript code supplied by the C2 server.
Gamaredon infection chains have also been noticed leveraging geoblocking to limit the attacks to particular places together with using dropper executables to start next-stage VBScript payloads, which subsequently hook up to the C2 server to execute further more instructions.
The geoblocking system functions as a security blindspot as it lessens the visibility of the risk actor’s attacks outside of the specific countries and tends to make its pursuits much more tough to track.
“Trident Ursa remains an agile and adaptive APT that does not use extremely advanced or complex strategies in its operations,” the researchers stated. “In most scenarios, they count on publicly offered tools and scripts – along with a significant amount of money of obfuscation – as very well as routine phishing tries to properly execute their operations.”
Located this short article appealing? Comply with us on Twitter and LinkedIn to study extra exceptional written content we write-up.
Some areas of this article are sourced from:
thehackernews.com


 A Guide to Efficient Patch Management with Action1
A Guide to Efficient Patch Management with Action1