Russian risk actors capitalized on the ongoing conflict versus Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service (DDoS) attacks from Russian internet sites.
Google Risk Analysis Group (TAG) attributed the malware to Turla, an superior persistent threat also regarded as Krypton, Venomous Bear, Waterbug, and Uroburos, and linked to Russia’s Federal Security Assistance (FSB).
“This is the initially known instance of Turla distributing Android-connected malware,” TAG researcher Billy Leonard stated. “The applications had been not dispersed by way of the Google Engage in Retail outlet, but hosted on a area controlled by the actor and disseminated by using one-way links on 3rd party messaging products and services.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

It is worth noting that the onslaught of cyberattacks in the quick aftermath of Russia’s unprovoked invasion of Ukraine prompted the latter to kind an IT Army to stage counter-DDoS attacks towards Russian internet sites. The target of the Turla operation, it seems, is to use this volunteer-run work to their possess edge.
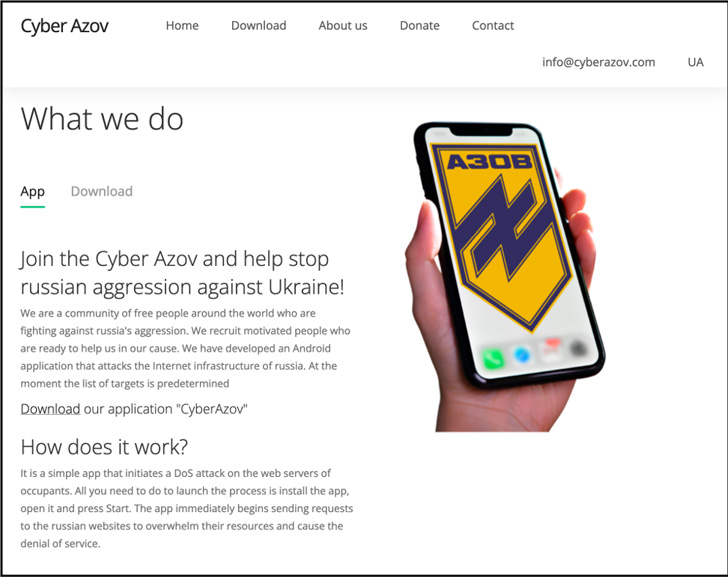
The decoy application was hosted on a domain masquerading as the Azov Regiment, a device of the Nationwide Guard of Ukraine, calling on individuals from all around the environment to combat “Russia’s aggression” by initiating a denial-of-support attack on the web servers belonging to “Russian internet websites to overwhelm their resources.”
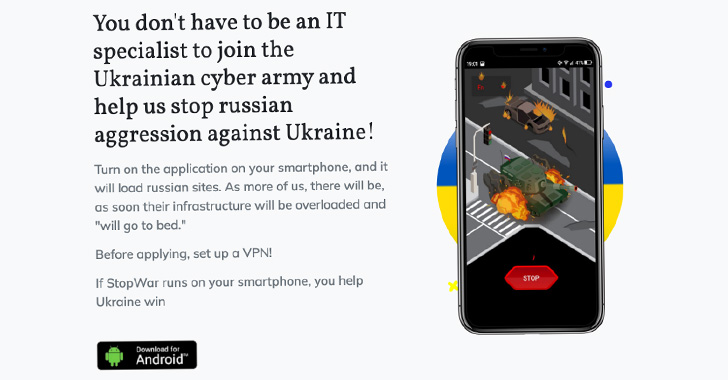
Google TAG stated the actors drew inspiration from one more Android application dispersed through a web page named “stopwar[.]pro” that is also designed to carry out DoS attacks by frequently sending requests to the goal web sites.
That stated, the real quantity of periods the destructive Cyber Azov application was installed is minuscule, posing no important influence on Android end users.
In addition, the Sandworm group (aka Voodoo Bear) has been related to a independent established of malicious activities leveraging the Follina vulnerability (CVE-2022-30190) in the Microsoft Windows Assistance Diagnostic Instrument (MSDT) to deliver backlinks pointing to Microsoft Place of work documents hosted on compromised websites focusing on media entities in Ukraine.

UAC-0098, a danger actor that CERT-UA last thirty day period warned of distributing tax-themed paperwork carrying a Follina exploit, has also been assessed to be a previous preliminary access broker with ties to the Conti group in charge of disseminating the IcedID banking trojan.
Other forms of cyber exercise incorporate credential phishing attacks mounted by an adversary referred to as COLDRIVER (aka Callisto) aimed at governing administration and defense officials, politicians, NGOs and think tanks, and journalists.
These contain sending e-mails possibly straight, which includes the phishing domain or containing links to files hosted on Google Travel and Microsoft OneDrive that, in turn, feature links to an attacker-controlled website created to steal passwords.
The most up-to-date developments are yet yet another indicator of how Russian danger actors are exhibiting continued signs of increasing sophistication in their makes an attempt to target in means that highlight their evolving tactics.
Discovered this report fascinating? Comply with THN on Facebook, Twitter and LinkedIn to read additional exceptional content material we put up.
Some pieces of this posting are sourced from:
thehackernews.com

 Russian Hackers Using DropBox and Google Drive to Drop Malicious Payloads
Russian Hackers Using DropBox and Google Drive to Drop Malicious Payloads