The Russian condition-sponsored hacking collective acknowledged as APT29 has been attributed to a new phishing campaign that usually takes benefit of genuine cloud products and services like Google Travel and Dropbox to provide destructive payloads on compromised techniques.
“These strategies are thought to have focused various Western diplomatic missions in between Might and June 2022,” Palo Alto Networks Device 42 mentioned in a Tuesday report. “The lures included in these campaigns counsel focusing on of a foreign embassy in Portugal as perfectly as a overseas embassy in Brazil.”
APT29, also tracked under the monikers Cozy Bear, Cloaked Ursa, or The Dukes, has been characterized as an structured cyberespionage group working to gather intelligence that aligns with Russia’s strategic objectives.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Some aspects of the highly developed persistent threat’s activities, including the infamous SolarWinds source chain attack of 2020, are separately tracked by Microsoft under the name Nobelium, with Mandiant calling it an evolving, disciplined, and very skilled danger actor that operates with a heightened level of operational security.”

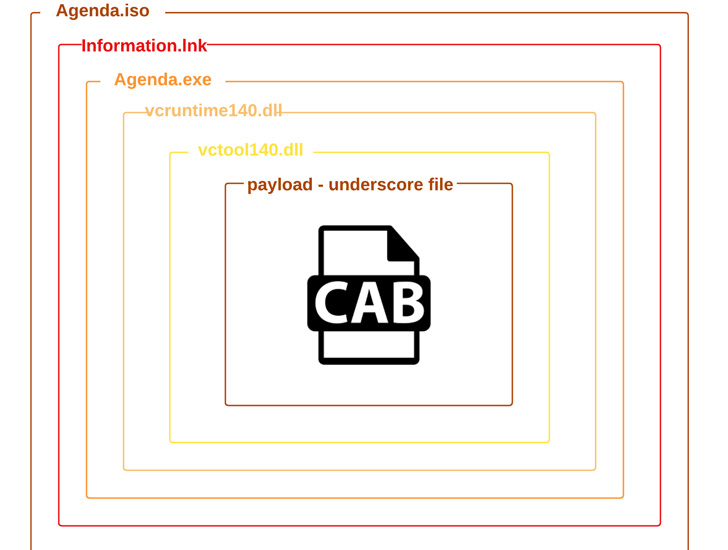
The most recent intrusions are a continuation of the same covert procedure formerly detailed by Mandiant and Cluster25 in May perhaps 2022, in which the spear-phishing email messages led to the deployment of Cobalt Strike Beacons by usually means of an HTML dropper attachment dubbed EnvyScout (aka ROOTSAW) attached immediately to the missives.
What is actually adjusted in the more recent iterations is the use of cloud products and services like Dropbox and Google Drive to conceal their steps and retrieve more malware into concentrate on environments. A next version of the attack observed in late May 2022 is claimed to have tailored further to host the HTML dropper in Dropbox.
“The campaigns and the payloads analyzed above time demonstrate a sturdy target on operating under the radar and reducing the detection costs,” Cluster25 famous at the time. “In this regard, even the use of legit services these types of as Trello and Dropbox advise the adversary’s will to run for a prolonged time inside the target environments remaining undetected.”
EnvyScout, for its portion, serves as an auxiliary resource to further infect the focus on with the actor’s implant of decision, in this circumstance, a .NET-primarily based executable that’s hid in multiple layers of obfuscation and utilised to exfiltrate technique info as well as execute next-stage binaries this kind of as Cobalt Strike fetched from Google Travel.

“The use of DropBox and Google Push solutions […] is a new tactic for this actor and one that proves demanding to detect thanks to the ubiquitous nature of these products and services and the simple fact that they are reliable by thousands and thousands of shoppers throughout the world,” the researchers explained.
The results also coincide with a new declaration from the Council of the European Union, calling out the spike in malicious cyber activities perpetrated by Russian risk actors and “condemn[ing] this unacceptable habits in cyberspace.”
“This increase in destructive cyber activities, in the context of the war versus Ukraine, makes unacceptable pitfalls of spillover results, misinterpretation and attainable escalation,” the Council stated in a press statement.
Found this post attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to go through extra distinctive written content we submit.
Some parts of this short article are sourced from:
thehackernews.com

 Best web browsers 2022: Google Chrome vs Microsoft Edge vs Firefox
Best web browsers 2022: Google Chrome vs Microsoft Edge vs Firefox