Google has taken measures to ax dozens of fraudulent applications from the official Play Retail store that have been spotted propagating Joker, Facestealer, and Coper malware people via the digital marketplace.
While the Android storefront is considered to be a trustworthy source for finding and setting up apps, lousy actors have frequently identified means to sneak previous security limitations erected by Google in hopes of luring unsuspecting users into downloading malware-laced apps.
The most current findings from Zscaler ThreatLabz and Pradeo are no various. “Joker is a person of the most popular malware households concentrating on Android devices,” researchers Viral Gandhi and Himanshu Sharma explained in a Monday report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Even with public recognition of this particular malware, it retains acquiring its way into Google’s formal application shop by consistently modifying the malware’s trace signatures together with updates to the code, execution solutions, and payload-retrieving methods.”

Classified as fleeceware, Joker (aka Bread) is developed to subscribe end users to undesirable compensated companies or make calls to top quality figures, even though also collecting SMS messages, get hold of lists, and system data. It was initial noticed in the Play Keep in 2017.
A full of 53 Joker downloader applications have been determined by the two cybersecurity corporations, with the programs downloaded cumulatively about 330,000 situations. These applications ordinarily pose as SMS, photograph editors, blood strain check, emoji keyboards, and translation apps that, in switch, request elevated permissions for the device to carry out its functions.
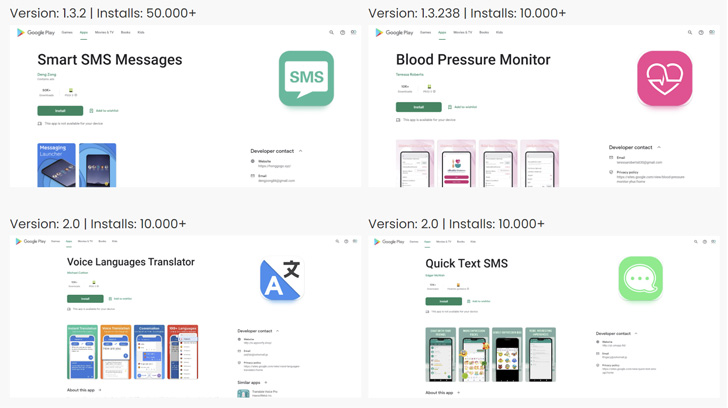
“As a substitute of waiting for apps to get a specified quantity of installs and reviews right before swapping for a malware-laced version, the Joker builders have taken to hiding the malicious payload in a frequent asset file and package deal software using business packers,” the scientists stated the new tactic adopted by the persistent malware to bypass detection.
It is really not just Joker, as security researcher Maxime Ingrao previous week disclosed 8 applications made up of a distinct variant of the malware referred to as Autolycos that racked up a full of in excess of a few million downloads prior to their elimination from the application retail store immediately after more than six months.
“What is new about this kind is that it no extended requires a WebView,” Malwarebytes researcher Pieter Arntz claimed. “Not demanding a WebView enormously minimizes the prospects that the user of an impacted machine notices a thing fishy is heading on. Autolycos avoids WebView by executing URLs on a distant browser and then which includes the result in HTTP requests.”
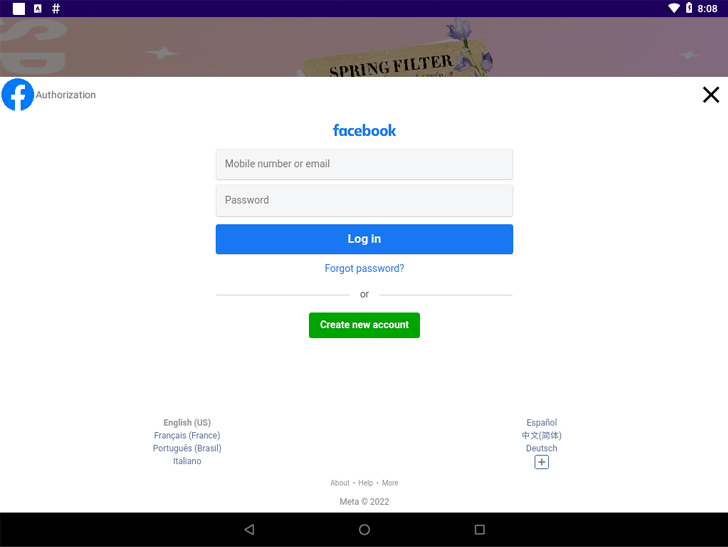
Also uncovered in the formal marketplace were applications embedding Facestealer and Coper malware. While the previous permits the operators to siphon Facebook qualifications and auth tokens, Coper — a descendant of the Exobot malware — functions as a banking trojan that can steal a wide selection of facts.

Coper is “able of intercepting and sending SMS textual content messages, creating USSD (Unstructured Supplementary Provider Data) requests to send messages, keylogging, locking/unlocking the unit display, doing extremely attacks, blocking uninstalls and normally enabling attackers to acquire control and execute instructions on contaminated product by using remote relationship with a C2 server,” the scientists mentioned.
The malware, like other banking trojans, is also recognised to abuse the accessibility permissions on Android to get whole manage of the victim’s phone. The listing of Facestealer and Coper dropper applications is as follows –
- Vanilla Camera (cam.vanilla.snapp)
- Unicc QR Scanner (com.qrdscannerratedx)
If nearly anything, the findings increase to Google’s storied record of struggling to retain these types of fleeceware and adware apps off its cell app shop, in component owing to a multitude of evolving tactics adopted by danger actors to fly less than the radar.
Besides the normal guidelines of thumb when it arrives to downloading applications from application suppliers, end users are advised to chorus from granting avoidable permissions to apps and confirm their legitimacy by examining for developer information and facts, looking through evaluations, and scrutinizing their privacy insurance policies.
Located this write-up appealing? Observe THN on Facebook, Twitter and LinkedIn to study additional exclusive information we article.
Some components of this report are sourced from:
thehackernews.com


 FBI Warns of Fake Cryptocurrency Apps Stealing Millions from Investors
FBI Warns of Fake Cryptocurrency Apps Stealing Millions from Investors